
Playbook for the Secure Enterprise

CyberSecurity Latest Rundown
Heroes, your curated look at the current cybersecurity landscape for Jan 12, 2026.
 CRITICAL ITEMS
CRITICAL ITEMS
-
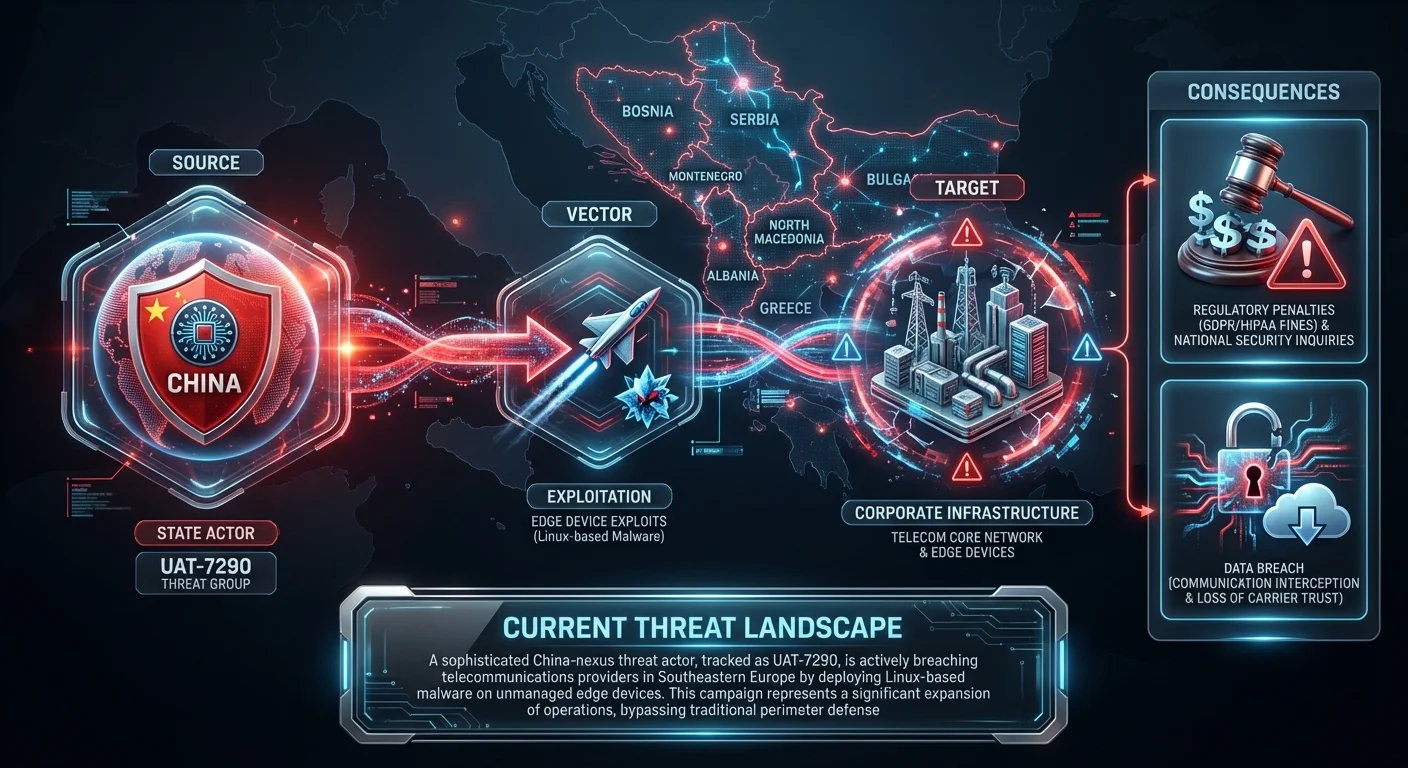
New China-linked hackers breach telcos using edge device exploits
Date & Time: 2026-01-10T07:22:05
A sophisticated China-nexus threat actor, tracked as UAT-7290, is actively breaching telecommunications providers in Southeastern Europe by deploying Linux-based malware on unmanaged edge devices. This campaign represents a significant expansion of operations, bypassing traditional perimeter defenses to establish persistent access.
Business impactExploitation of edge devices allows attackers to intercept communications and pivot into core networks, leading to severe regulatory fines under GDPR/HIPAA, loss of carrier trust, and potential national security inquiries.Recommended actionAsk your IT team: Do we have a verified inventory of all edge devices (VPNs, routers) and are they running the latest firmware? Verify that management interfaces are not exposed to the public internet.CVE: n/a | Compliance: HIPAA, GDPR | Source: Lifeboat ↗ ↗
-
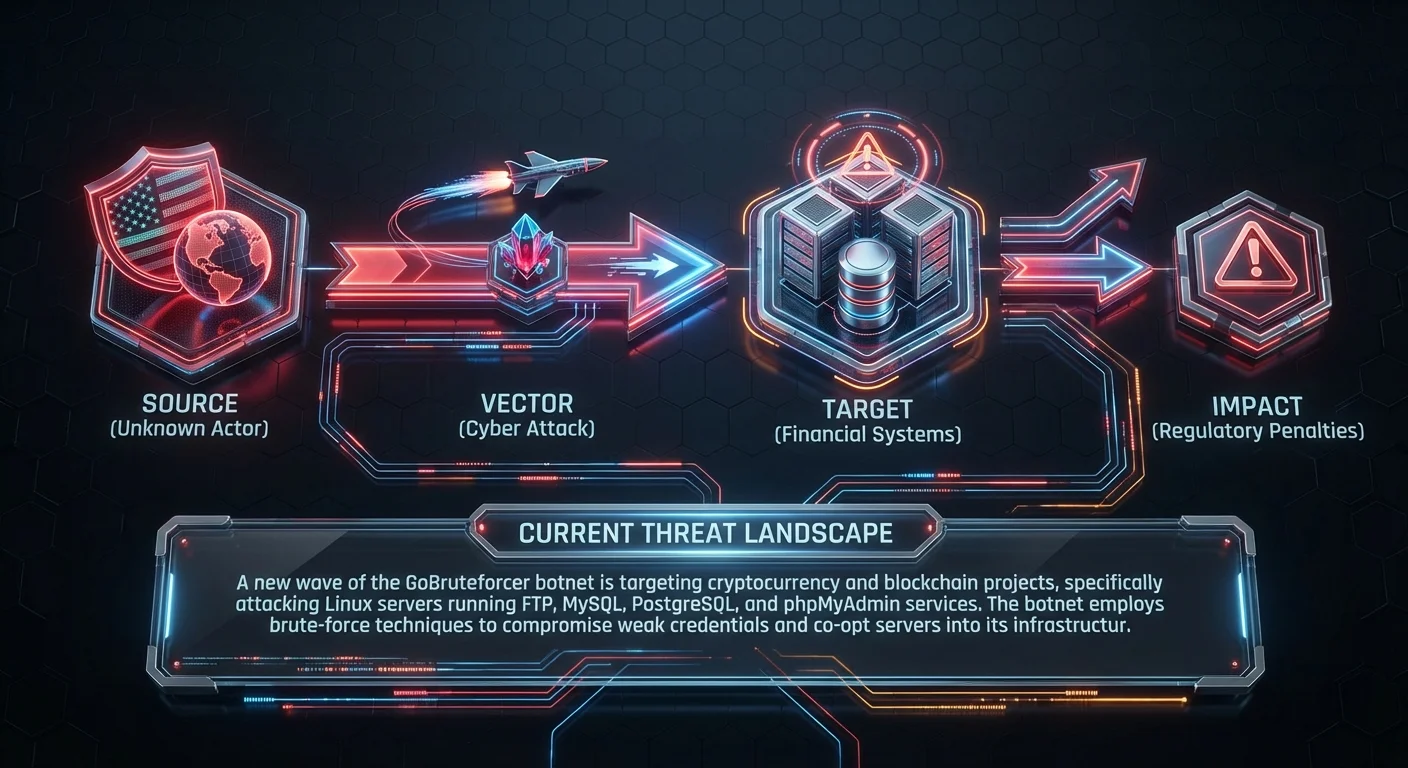
GoBruteforcer Botnet Targets Crypto Project Databases
Date & Time: 2026-01-12T10:48:00
A new wave of the GoBruteforcer botnet is targeting cryptocurrency and blockchain projects, specifically attacking Linux servers running FTP, MySQL, PostgreSQL, and phpMyAdmin services. The botnet employs brute-force techniques to compromise weak credentials and co-opt servers into its infrastructure.
Business impactSuccessful compromise can lead to direct theft of digital assets, corruption of transaction ledgers, and unauthorized access to customer PII, resulting in immediate financial loss and NIS2 non-compliance penalties.Recommended actionAsk your Security Operations team: Have we enforced strict IP allow-listing for all database management ports? Confirm that complex password policies are enforced for all service accounts.CVE: n/a | Compliance: GDPR | Source: The Hacker News ↗ ↗
 HIGH SEVERITY ITEMS
HIGH SEVERITY ITEMS
-
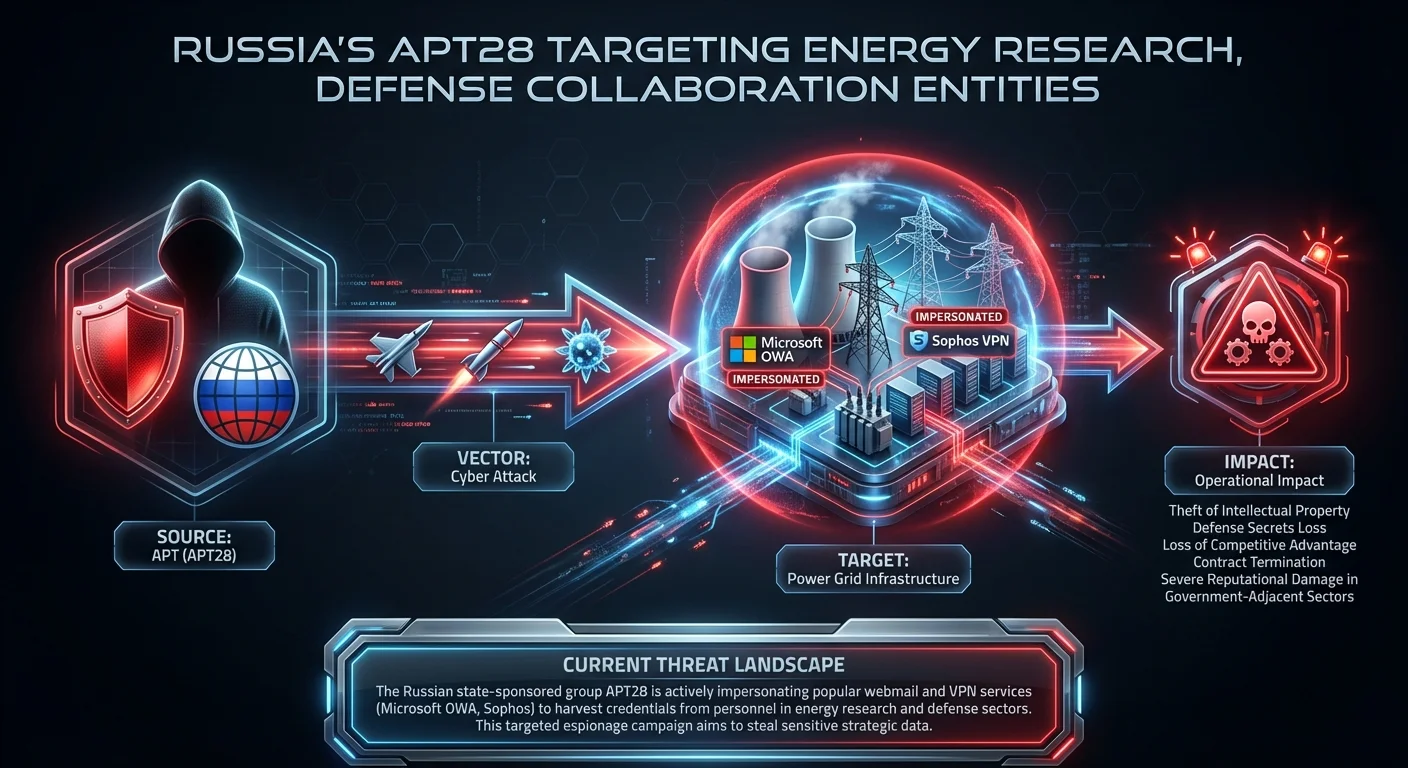
Russia’s APT28 Targeting Energy Research, Defense Collaboration Entities
Date & Time: 2026-01-12T12:23:13
The Russian state-sponsored group APT28 is actively impersonating popular webmail and VPN services (Microsoft OWA, Sophos) to harvest credentials from personnel in energy research and defense sectors. This targeted espionage campaign aims to steal sensitive strategic data.
Business impactTheft of intellectual property and defense secrets can lead to loss of competitive advantage, contract termination, and severe reputational damage in government-adjacent sectors.Recommended actionAsk your Identity team: Do we require FIDO2/hardware-based MFA for all external access points? Legacy MFA methods (SMS/Push) are insufficient against these phishing proxies.CVE: n/a | Compliance: SOX | Source: SecurityWeek ↗ ↗
OTHER NOTEWORTHY ITEMS

-
Palo Alto Networks Defines SHIELD Framework to Secure Vibecoding
Date & Time: 2026-01-12T12:28:24
Palo Alto Networks has released the SHIELD framework to address security risks in "vibecoding" (AI-assisted coding) environments. This framework provides best practices to mitigate vulnerabilities introduced by rapid, AI-generated development cycles.
CVE: n/a | Compliance: SOX | Source: Security Boulevard ↗ ↗
-
Turkish Security Researcher Gets Nod From NASA Over Vulnerability Discoveries
Date & Time: 2026-01-12T09:58:23
NASA has publicly acknowledged a researcher for responsibly disclosing vulnerabilities via their VDP. This reinforces the value of maintaining robust vulnerability disclosure programs for organizational security.
CVE: n/a | Compliance: SOX | Source: Security Boulevard ↗ ↗

-
Investors Are Getting Into Data Centers And Downtime Is A Serious Concern
Date & Time: 2026-01-12T13:16:21
With data storage needs hitting 200 zettabytes, investors are increasingly focused on data center resilience. Downtime is becoming a critical financial risk factor beyond just technical operations.
CVE Details: n/a
Source: Cybersecurity Ventures ↗ ↗
 EXECUTIVE INSIGHTS
EXECUTIVE INSIGHTS
-
Tenable Is a Gartner® Peer InsightsTM Customers’ Choice for Cloud-Native Application Protection Platforms
Date & Time: 2026-01-12T13:28:28 Summary & Significance: Tenable has been recognized for its Cloud-Native Application Protection Platform (CNAPP), highlighting the market consolidation around unified cloud security tools. For executives, this validates the shift towards integrated platforms for SOX/SOC 2 compliance in cloud environments. Source: Tenable ↗
 VENDOR SPOTLIGHT
VENDOR SPOTLIGHT
-
Eclypsium (Specialized Vendor)
Specialization: Firmware and Hardware Supply Chain Security
Why Eclypsium Today: Eclypsium specializes in securing the firmware and hardware layer of IT infrastructure, which is directly relevant to the reported China-linked attacks targeting telecommunications providers via edge device exploits. Their platform detects vulnerabilities and implants in network gear and VPN appliances, a critical defense against sophisticated actors like UAT-7290 that leverage Linux-based malware on unmanaged edge devices.
Key Capability: Automated discovery and integrity verification of firmware in network and edge devices
Recommended Actions: 1. Navigate to Eclypsium Console → Risks → Threats & Integrity → Filter by Device Type: 'Network' 2. Navigate to Eclypsium Console → Risks → Vulnerabilities → Filter by Severity: 'Critical' & Device Type: 'Network' 3. Navigate to Eclypsium Console → Devices → Network Devices → Select Target Subnets → Actions → Scan Now
Verification Steps: - Review 'Last Scanned' timestamp and 'Scan Status' in the Devices inventory for critical edge assets. - Drill down into a specific remediated asset: Device Details → Firmware → Change Log.
This guidance assumes the Eclypsium platform is correctly configured with network scanning capabilities for edge devices. UI paths may vary slightly based on SaaS version updates.
 DETECTION & RESPONSE KIT
DETECTION & RESPONSE KIT
-
⚠️ Disclaimer: Test all detection logic in non-production environments before deployment.
1. Vendor Platform Configuration - Eclypsium
2. YARA Rule for APT28 Indicators
3. SIEM Query — GoBruteforcer Database Attack Detection
4. PowerShell Script — Tycoon/Palo Alto Indicator Check
This rundown should provide a solid overview of the current threat landscape. Thank you to all our cyberheroes for your diligence and hard work. Stay vigilant!

