[copy]
{
"type": "bundle",
"id": "bundle--00c1539d-f7f5-4df9-ad9d-05f7b84e510e",
"objects": [
{
"type": "marking-definition",
"spec_version": "2.1",
"id": "marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"created": "2022-10-01T00:00:00.000Z",
"definition_type": "tlp:2.0",
"name": "TLP:CLEAR",
"definition": {
"tlp": "clear"
}
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--32baab15-09fe-4841-8608-790a4ac4ca43",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"name": "MikeGPT Intelligence Platform",
"description": "AI-powered threat intelligence collection and analysis platform providing automated cybersecurity intelligence feeds",
"identity_class": "organization",
"sectors": [
"technology",
"defense"
],
"contact_information": "Website: https://mikegptai.com | Email: intel@mikegptai.com",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"type": "report",
"spec_version": "2.1",
"id": "report--f6cd7c3b-aff6-4f64-a7fe-dd9b729e123d",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"name": "Threat Intelligence Report - 2026-01-09",
"description": "Threat Intelligence Report - 2026-01-09\n\nThis report consolidates actionable cybersecurity intelligence from 88 sources, processed through automated threat analysis and relationship extraction.\n\nKEY FINDINGS:\n• Vulnerability in firmware of KAON CG3000T/CG3000TC routers (Score: 100)\n• Vulnerabilities in firmware of Vivotek IP7137 camera (Score: 100)\n• Exploit for VMware Zero-Day Flaws Likely Built a Year Before Public Disclosure (Score: 100)\n• Trend Micro Apex Central RCE Flaw Scores 9.8 CVSS in On-Prem Windows Versions (Score: 100)\n• The Week in Vulnerabilities: 2026 Starts with 100 PoCs and New Exploits (Score: 100)\n\nEXTRACTED ENTITIES:\n• 24 Attack Pattern(s)\n• 1 Marking Definition(s)\n• 9 Tool(s)\n• 9 Vulnerability(s)\n\nCONFIDENCE ASSESSMENT:\nVariable confidence scoring applied based on entity type and intelligence source reliability. Confidence ranges from 30-95% reflecting professional intelligence assessment practices.\n\nGENERATION METADATA:\n- Processing Time: Automated\n- Validation: Three-LLM consensus committee\n- Standards Compliance: STIX 2.1\n",
"published": "2026-01-09T16:58:51.950Z",
"object_refs": [
"identity--32baab15-09fe-4841-8608-790a4ac4ca43",
"vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"vulnerability--d95868d7-4f07-4d84-b742-07ee4cf4adbf",
"identity--6741006f-839c-40a5-9d6e-5c3499671c57",
"identity--0f9dfab5-c9f5-4fef-b687-02b16bd9cd44",
"identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"tool--1c477a18-f48c-4db2-811d-30db0f2048c2",
"tool--f9d3fdc3-b825-4a3f-b385-d6afc1d5ac3a",
"identity--562e37e9-4a8b-4e03-bfb5-df3d48cdbac2",
"identity--161fc746-cd49-4615-ab48-81a93a1b16b4",
"identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"identity--d6d78394-a68a-4742-9c28-bc2485e0a1b5",
"tool--64a2e1d0-3271-4fea-9042-f00f041b6446",
"vulnerability--f2c85047-039e-45c6-be89-858863997f27",
"vulnerability--5bde0d49-60e8-4c46-816a-eb224d341549",
"vulnerability--4637304d-01b4-4252-8a74-007180df9397",
"vulnerability--f2f1df71-921f-44d8-a94c-7a29f2936114",
"vulnerability--639be3fc-320d-4c17-b84b-60b43d2dda98",
"vulnerability--773c21cf-7a9e-4746-b0ab-233a26535983",
"identity--ef71ec8f-ffa1-4759-ab5b-736db5801d23",
"tool--23492da9-0478-447b-bf37-841f0783b37c",
"identity--7e0c53f7-b1f3-413c-ac52-b63802f49b97",
"identity--7d9e6598-3c1b-45cc-bb32-6528b09d05b5",
"tool--e25006a6-ff66-430c-9799-5eba4b395058",
"tool--c03eb907-e48e-4969-99d1-e8fa5b77ad95",
"identity--0186ae1b-86aa-44d7-b12e-8dd8db99009b",
"identity--6e4095b9-c779-46d7-b6a4-7d192e9e340a",
"tool--b9a8e822-a324-4724-aec8-c0829e3991f4",
"tool--fdd26621-04c4-49df-8347-1cdfddcaa78b",
"tool--f4264dbc-7c8f-4b58-b01d-5563efb59bb8",
"attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"attack-pattern--2c821981-fda2-4cb8-926c-6edd4905d65c",
"attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"attack-pattern--01df90e4-619d-4268-90c9-6e2aa84079d9",
"attack-pattern--06cf8802-38e4-4421-a699-33a0bae74d96",
"attack-pattern--2e52cc86-c2ef-43d7-9f1e-2fc59c4845ee",
"attack-pattern--943edc6f-c0f9-48f1-b8d4-4666aa0abae1",
"attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"attack-pattern--8dd2a740-fa1b-4f41-be82-018bed51553e",
"attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"attack-pattern--171b894d-4a95-4d61-a038-093eaef8dc9e",
"attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6"
],
"labels": [
"threat-report",
"threat-intelligence"
],
"created_by_ref": "identity--32baab15-09fe-4841-8608-790a4ac4ca43",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.361Z",
"modified": "2026-01-09T16:58:51.361Z",
"confidence": 89,
"type": "vulnerability",
"id": "vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"name": "CVE-2025",
"description": "A high-severity security flaw in MongoDB",
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025"
},
{
"source_name": "nvd",
"external_id": "CVE-2025",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.361Z",
"modified": "2026-01-09T16:58:51.361Z",
"confidence": 87,
"type": "vulnerability",
"id": "vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"name": "SecurityWeek",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.361Z",
"modified": "2026-01-09T16:58:51.361Z",
"confidence": 89,
"type": "vulnerability",
"id": "vulnerability--d95868d7-4f07-4d84-b742-07ee4cf4adbf",
"name": "React2Shell",
"description": "React2Shell is a vulnerability in React Server Components that could lead to denial-of-service attacks or the exposure of source code. It is one of several recently discovered flaws in React Server Components, including CVE-2025-55183, CVE-2025-55184, and CVE-2025-67779. React2Shell is considered a dangerous vulnerability that requires immediate attention from security teams to prevent exploitation by threat actors.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.361Z",
"modified": "2026-01-09T16:58:51.361Z",
"confidence": 95,
"type": "identity",
"id": "identity--6741006f-839c-40a5-9d6e-5c3499671c57",
"name": "Cisco",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Cisco is a technology company.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.361Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--0f9dfab5-c9f5-4fef-b687-02b16bd9cd44",
"name": "Cybercrime Magazine",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Cybersecurity news and information website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"name": "Sausalito",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"name": "China",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "China is a country.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"name": "Non-Human Identities",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "tool",
"id": "tool--1c477a18-f48c-4db2-811d-30db0f2048c2",
"name": "Android",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Android is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "tool",
"id": "tool--f9d3fdc3-b825-4a3f-b385-d6afc1d5ac3a",
"name": "Creators & Presenters",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "CloudFront is a cloud infrastructure service",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--562e37e9-4a8b-4e03-bfb5-df3d48cdbac2",
"name": "TechRepublic",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Technology news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--161fc746-cd49-4615-ab48-81a93a1b16b4",
"name": "GitHub",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "GitHub is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"name": "Security Boulevard",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "identity",
"id": "identity--d6d78394-a68a-4742-9c28-bc2485e0a1b5",
"name": "the World Economic Forum",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "International organization focused on global economic issues",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "tool",
"id": "tool--64a2e1d0-3271-4fea-9042-f00f041b6446",
"name": "FIDO2",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Covenant Health data breach incident",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.362Z",
"modified": "2026-01-09T16:58:51.362Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--f2c85047-039e-45c6-be89-858863997f27",
"name": "CVE-2025-7072",
"description": "The firmware in KAON CG3000TC and CG3000T routers contains hard-coded credentials in clear text (shared across all routers of this model) that an unauthenticated remote attacker could use to execute commands with root privileges.\nThis vulnerability has been fixed in firmware version: 1.00.67 for CG3000TC and 1.00.27 for CG3000T.. EPSS: 0.2% exploitation probability",
"x_kev_status": false,
"x_epss_score": 0.00213,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-7072",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-7072"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-7072",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-7072"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--5bde0d49-60e8-4c46-816a-eb224d341549",
"name": "CVE-2025-69258",
"description": "A LoadLibraryEX vulnerability in Trend Micro Apex Central could allow an unauthenticated remote attacker to load an attacker-controlled DLL into a key executable, leading to execution of attacker-supplied code under the context of SYSTEM on affected installations.. CVSS Score: 9.8 (CRITICAL). EPSS: 0.2% exploitation probability",
"x_cvss_score": 9.8,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.00153,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-69258",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-69258"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-69258",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-69258"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "vulnerability",
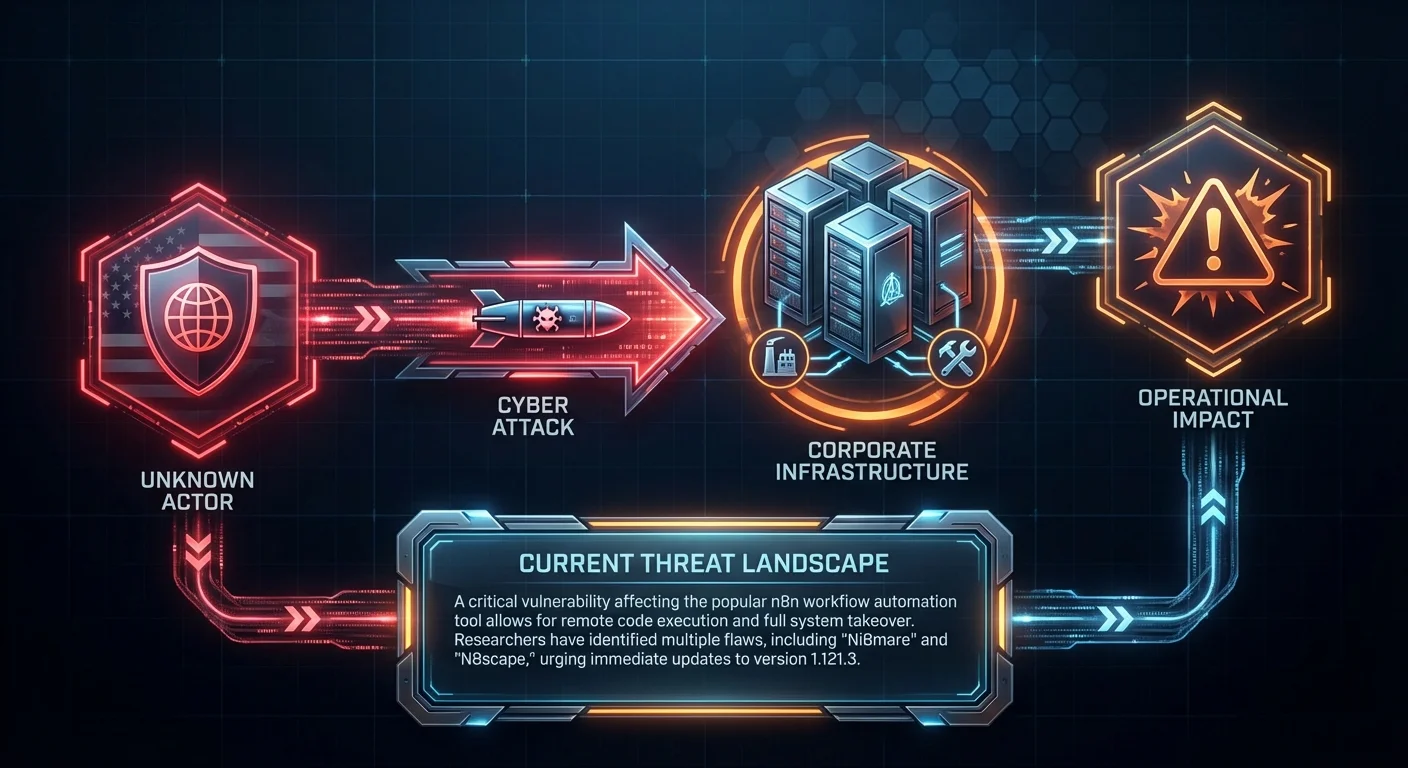
"id": "vulnerability--4637304d-01b4-4252-8a74-007180df9397",
"name": "CVE-2026-21858",
"description": "n8n is an open source workflow automation platform. Versions starting with 1.65.0 and below 1.121.0 enable an attacker to access files on the underlying server through execution of certain form-based workflows. A vulnerable workflow could grant access to an unauthenticated remote attacker, resulting in exposure of sensitive information stored on the system and may enable further compromise depending on deployment configuration and workflow usage. This issue is fixed in version 1.121.0.. CVSS Score: 10.0 (CRITICAL). EPSS: 0.0% exploitation probability",
"x_cvss_score": 10.0,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.0003,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2026-21858",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2026-21858"
},
{
"source_name": "nvd",
"external_id": "CVE-2026-21858",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2026-21858"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--f2f1df71-921f-44d8-a94c-7a29f2936114",
"name": "CVE-2025-66049",
"description": "Vivotek IP7137 camera with firmware version 0200a is vulnerable to an information disclosure issue where live camera footage can be accessed through the RTSP protocol on port 8554 without requiring authentication. This allows unauthorized users with network access to view the camera's feed, potentially compromising user privacy and security. \nThe vendor has not replied to the CNA. Possibly all firmware versions are affected. Since the product has met End-Of-Life phase, a fix is not expected to b. EPSS: 0.1% exploitation probability",
"x_kev_status": false,
"x_epss_score": 0.0005,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-66049",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-66049"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-66049",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-66049"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--639be3fc-320d-4c17-b84b-60b43d2dda98",
"name": "CVE-2026-20029",
"description": "A vulnerability in the licensing features of Cisco Identity Services Engine (ISE) and Cisco ISE Passive Identity Connector (ISE-PIC) could allow an authenticated, remote attacker with administrative privileges to gain access to sensitive information. \r\n\r\nThis vulnerability is due to improper parsing of XML that is processed by the web-based management interface of Cisco ISE and Cisco ISE-PIC. An attacker could exploit this vulnerability by uploading a malicious file to the application.. CVSS Score: 4.9 (MEDIUM). EPSS: 0.0% exploitation probability",
"x_cvss_score": 4.9,
"x_cvss_severity": "MEDIUM",
"x_kev_status": false,
"x_epss_score": 0.00033,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2026-20029",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2026-20029"
},
{
"source_name": "nvd",
"external_id": "CVE-2026-20029",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2026-20029"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--773c21cf-7a9e-4746-b0ab-233a26535983",
"name": "CVE-2025-37164",
"description": "A remote code execution issue exists in HPE OneView.. CVSS Score: 10.0 (CRITICAL). CISA KEV: Active exploitation confirmed. EPSS: 81.3% exploitation probability",
"x_cvss_score": 10.0,
"x_cvss_severity": "CRITICAL",
"x_kev_status": true,
"x_epss_score": 0.8131,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-37164",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-37164"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-37164",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-37164"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "identity",
"id": "identity--ef71ec8f-ffa1-4759-ab5b-736db5801d23",
"name": "Description CERT Polska",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "CERT Polska is a cybersecurity incident response team.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "tool",
"id": "tool--23492da9-0478-447b-bf37-841f0783b37c",
"name": "Vivotek IP7137",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Vivotek IP7137 is a camera model.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "identity",
"id": "identity--7e0c53f7-b1f3-413c-ac52-b63802f49b97",
"name": "Vivotek",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Vivotek is a company that produces IP cameras.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "identity",
"id": "identity--7d9e6598-3c1b-45cc-bb32-6528b09d05b5",
"name": "VMware",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "VMware is a company that produces virtualization software.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 80,
"type": "tool",
"id": "tool--e25006a6-ff66-430c-9799-5eba4b395058",
"name": "Exploit",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A method or technique used to take advantage of a vulnerability in software.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "tool",
"id": "tool--c03eb907-e48e-4969-99d1-e8fa5b77ad95",
"name": "Apex Central for Windows",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Apex Central for Windows is a security software.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "identity",
"id": "identity--0186ae1b-86aa-44d7-b12e-8dd8db99009b",
"name": "SonicWall",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "SonicWall is a company that produces network security products.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "identity",
"id": "identity--6e4095b9-c779-46d7-b6a4-7d192e9e340a",
"name": "Vercel",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Vercel is a company that maintains Next.js.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "tool",
"id": "tool--b9a8e822-a324-4724-aec8-c0829e3991f4",
"name": "ISE-PIC",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "ISE-PIC is a software component.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "tool",
"id": "tool--fdd26621-04c4-49df-8347-1cdfddcaa78b",
"name": "Identity Services Engine",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Identity Services Engine is a software product.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 95,
"type": "tool",
"id": "tool--f4264dbc-7c8f-4b58-b01d-5563efb59bb8",
"name": "Passive Identity Connector",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Passive Identity Connector is a software component.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.363Z",
"modified": "2026-01-09T16:58:51.363Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"name": "Exploit Public-Facing Application",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1190",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1190/",
"external_id": "T1190"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"name": "Exploitation for Client Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1203",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1203/",
"external_id": "T1203"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"name": "Command and Scripting Interpreter",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/",
"external_id": "T1059"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"name": "Remote Services",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "lateral-movement"
}
],
"x_mitre_id": "T1021",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1021/",
"external_id": "T1021"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2c821981-fda2-4cb8-926c-6edd4905d65c",
"name": "Lateral Tool Transfer",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "lateral-movement"
}
],
"x_mitre_id": "T1570",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1570/",
"external_id": "T1570"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"name": "Abuse Elevation Control Mechanism",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1548",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1548/",
"external_id": "T1548"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"name": "Access Token Manipulation",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1134",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1134/",
"external_id": "T1134"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"name": "Spearphishing Attachment",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/001/",
"external_id": "T1566.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"name": "Spearphishing Link",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/002/",
"external_id": "T1566.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"name": "Spearphishing via Service",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/003/",
"external_id": "T1566.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--01df90e4-619d-4268-90c9-6e2aa84079d9",
"name": "PowerShell",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/001/",
"external_id": "T1059.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--06cf8802-38e4-4421-a699-33a0bae74d96",
"name": "System Information Discovery",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "discovery"
}
],
"x_mitre_id": "T1082",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1082/",
"external_id": "T1082"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2e52cc86-c2ef-43d7-9f1e-2fc59c4845ee",
"name": "File and Directory Discovery",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "discovery"
}
],
"x_mitre_id": "T1083",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1083/",
"external_id": "T1083"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--943edc6f-c0f9-48f1-b8d4-4666aa0abae1",
"name": "Process Discovery",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "discovery"
}
],
"x_mitre_id": "T1057",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1057/",
"external_id": "T1057"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 78,
"type": "attack-pattern",
"id": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"name": "Vulnerabilities",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/006/",
"external_id": "T1588.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 76,
"type": "attack-pattern",
"id": "attack-pattern--8dd2a740-fa1b-4f41-be82-018bed51553e",
"name": "Safe Mode Boot",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1562.009",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1562/009/",
"external_id": "T1562.009"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"name": "Scheduled Task",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1053.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1053/005/",
"external_id": "T1053.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"name": "Socket Filters",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1205.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1205/002/",
"external_id": "T1205.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"name": "Boot or Logon Initialization Scripts",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1037",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1037/",
"external_id": "T1037"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"name": "Archive via Utility",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1560.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1560/001/",
"external_id": "T1560.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"name": "Screen Capture",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1113",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1113/",
"external_id": "T1113"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"name": "Adversary-in-the-Middle",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/",
"external_id": "T1557"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 68,
"type": "attack-pattern",
"id": "attack-pattern--171b894d-4a95-4d61-a038-093eaef8dc9e",
"name": "System Firmware",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1542.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1542/001/",
"external_id": "T1542.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-09T16:58:51.950Z",
"modified": "2026-01-09T16:58:51.950Z",
"confidence": 65,
"type": "attack-pattern",
"id": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"name": "Artificial Intelligence",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.007",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/007/",
"external_id": "T1588.007"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
}
]
}


 CRITICAL ITEMS
CRITICAL ITEMS

 HIGH SEVERITY ITEMS
HIGH SEVERITY ITEMS


 EXECUTIVE INSIGHTS
EXECUTIVE INSIGHTS VENDOR SPOTLIGHT
VENDOR SPOTLIGHT DETECTION & RESPONSE KIT
DETECTION & RESPONSE KIT
