[copy]
{
"type": "bundle",
"id": "bundle--4f77bdeb-2fe9-4105-9372-25b334725f11",
"objects": [
{
"type": "marking-definition",
"spec_version": "2.1",
"id": "marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"created": "2022-10-01T00:00:00.000Z",
"definition_type": "tlp:2.0",
"name": "TLP:CLEAR",
"definition": {
"tlp": "clear"
}
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--1b38ea2f-2a0f-413d-b3eb-1c1e3f737172",
"created": "2026-01-06T19:01:10.908Z",
"modified": "2026-01-06T19:01:10.908Z",
"name": "MikeGPT Intelligence Platform",
"description": "AI-powered threat intelligence collection and analysis platform providing automated cybersecurity intelligence feeds",
"identity_class": "organization",
"sectors": [
"technology",
"defense"
],
"contact_information": "Website: https://mikegptai.com | Email: intel@mikegptai.com",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"type": "report",
"spec_version": "2.1",
"id": "report--f094dad0-b755-4365-a732-7f4dcd65e7c4",
"created": "2026-01-06T19:01:10.908Z",
"modified": "2026-01-06T19:01:10.908Z",
"name": "Threat Intelligence Report - 2026-01-06",
"description": "Threat Intelligence Report - 2026-01-06\n\nThis report consolidates actionable cybersecurity intelligence from 85 sources, processed through automated threat analysis and relationship extraction.\n\nKEY FINDINGS:\n• Introducing the Microsoft Defender Experts Suite: Elevate your security with expert-led services (Score: 100)\n• Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover (Score: 100)\n• Google Security & Safety: Why Cloud Monitor is Worth the Investment at Morgan Local Schools (Score: 100)\n• VU#420440: Vulnerable Python version used in Forcepoint One DLP Client (Score: 100)\n• Trusted Google Notifications Used in Phishing Campaign Targeting 3,000+ Orgs (Score: 100)\n\nEXTRACTED ENTITIES:\n• 30 Attack Pattern(s)\n• 1 Marking Definition(s)\n• 2 Tool(s)\n• 7 Vulnerability(s)\n\nCONFIDENCE ASSESSMENT:\nVariable confidence scoring applied based on entity type and intelligence source reliability. Confidence ranges from 30-95% reflecting professional intelligence assessment practices.\n\nGENERATION METADATA:\n- Processing Time: Automated\n- Validation: Three-LLM consensus committee\n- Standards Compliance: STIX 2.1\n",
"published": "2026-01-06T19:01:10.908Z",
"object_refs": [
"identity--1b38ea2f-2a0f-413d-b3eb-1c1e3f737172",
"identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"identity--562e37e9-4a8b-4e03-bfb5-df3d48cdbac2",
"identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"identity--fd1e3790-7e3a-48a3-8684-16f17330c96f",
"identity--ae4d5f46-29c5-40ae-842b-378abf057c12",
"vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"identity--dc1263f3-2308-479e-be5c-f6e47388fa29",
"identity--6741006f-839c-40a5-9d6e-5c3499671c57",
"identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"tool--1c477a18-f48c-4db2-811d-30db0f2048c2",
"vulnerability--f2c42dbe-e16d-4283-9151-c7c085f96cb9",
"vulnerability--2c52f963-abfe-4465-a581-7ef4776df799",
"vulnerability--767e17cd-6df9-4135-8c74-6e68d953a523",
"vulnerability--b3f57762-597b-4de7-9a7c-7384c6571a3d",
"identity--d6d78394-a68a-4742-9c28-bc2485e0a1b5",
"identity--91e4f85a-d9b4-4262-82ee-85b29bb6ba1c",
"vulnerability--14a890fd-5d24-46d2-99f9-36f5a2ad8bda",
"tool--426bfb17-cff4-4d72-9a99-c94bd6712777",
"identity--0f9dfab5-c9f5-4fef-b687-02b16bd9cd44",
"identity--8d960ac4-0bb0-4028-b021-052be9c48439",
"identity--ae1b46f6-1764-46f4-a722-218ee5c1fba5",
"identity--2daf3eee-ee2d-4a01-b724-90e3ce3a3f4f",
"attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"attack-pattern--c3286059-b33e-4b64-9fda-22075baf9afa",
"attack-pattern--97050bed-0864-4e3c-9f82-facd1eb7fc63",
"attack-pattern--c1ff2266-1a4b-4292-80e6-f593eb2569a9",
"attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"attack-pattern--239957f5-5ae1-4977-a451-144fae4a6361",
"attack-pattern--a29578ca-547d-4c9a-acfd-6742cfae2f22",
"attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"attack-pattern--08294e9d-c1e2-46dc-9760-a3537ae37209",
"attack-pattern--48a7a9f8-a5c6-444a-8cfb-bd9602d2d34e",
"attack-pattern--5aff02b0-8030-4a6a-bc0c-3ddc61680683",
"attack-pattern--26d99677-799b-44ed-bc54-5fef76cbc72c",
"attack-pattern--4e2f5b9a-cf3a-4ab7-9169-8362c52dd57d",
"attack-pattern--b863fbfb-5683-4f21-8c51-9323c0303278",
"attack-pattern--3785d15d-1c0c-4464-9200-10b744888e29",
"attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"attack-pattern--92b3199d-f7ae-4a4b-8699-1d01a6761923",
"attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"attack-pattern--dd0edf90-8f96-4a15-852b-ba611cd81716"
],
"labels": [
"threat-report",
"threat-intelligence"
],
"created_by_ref": "identity--1b38ea2f-2a0f-413d-b3eb-1c1e3f737172",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.555Z",
"modified": "2026-01-06T19:01:09.555Z",
"confidence": 95,
"type": "identity",
"id": "identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"name": "Google",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Google is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.555Z",
"modified": "2026-01-06T19:01:09.555Z",
"confidence": 95,
"type": "identity",
"id": "identity--562e37e9-4a8b-4e03-bfb5-df3d48cdbac2",
"name": "TechRepublic",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Technology news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"name": "Sausalito",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--fd1e3790-7e3a-48a3-8684-16f17330c96f",
"name": "Palo Alto Networks",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity company.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--ae4d5f46-29c5-40ae-842b-378abf057c12",
"name": "Microsoft",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Microsoft is a multinational technology company that develops, manufactures, licenses, and supports a wide range of software products, services, and devices.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"name": "CVE-2025",
"description": "A high-severity security flaw in MongoDB",
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025"
},
{
"source_name": "nvd",
"external_id": "CVE-2025",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--dc1263f3-2308-479e-be5c-f6e47388fa29",
"name": "Singapore",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A country with a Cyber Security Agency",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--6741006f-839c-40a5-9d6e-5c3499671c57",
"name": "Cisco",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Cisco is a technology company.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"name": "Cybersecurity",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Cybersecurity is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"name": "Non-Human Identities",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 92,
"type": "vulnerability",
"id": "vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"name": "SecurityWeek",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"name": "Security Boulevard",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "tool",
"id": "tool--1c477a18-f48c-4db2-811d-30db0f2048c2",
"name": "Android",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Android is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--f2c42dbe-e16d-4283-9151-c7c085f96cb9",
"name": "CVE-2025-13915",
"description": "IBM API Connect 10.0.8.0 through 10.0.8.5, and 10.0.11.0 could allow a remote attacker to bypass authentication mechanisms and gain unauthorized access to the application.. CVSS Score: 9.8 (CRITICAL). EPSS: 0.4% exploitation probability",
"x_cvss_score": 9.8,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.00373,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-13915",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-13915"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-13915",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-13915"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 80,
"type": "vulnerability",
"id": "vulnerability--2c52f963-abfe-4465-a581-7ef4776df799",
"name": "CVE-2025-65606",
"description": "The flaw, CVE-2025-65606 (CVSS score: N/A), has been characterized as a fla...",
"x_cvss_severity": "Unknown",
"x_kev_status": false,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-65606",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-65606"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-65606",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-65606"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--767e17cd-6df9-4135-8c74-6e68d953a523",
"name": "CVE-2025-47987",
"description": "Heap-based buffer overflow in Windows Cred SSProvider Protocol allows an authorized attacker to elevate privileges locally.. CVSS Score: 7.8 (HIGH). EPSS: 0.1% exploitation probability",
"x_cvss_score": 7.8,
"x_cvss_severity": "HIGH",
"x_kev_status": false,
"x_epss_score": 0.00078,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-47987",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-47987"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-47987",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-47987"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--b3f57762-597b-4de7-9a7c-7384c6571a3d",
"name": "CVE-2026-21440",
"description": "AdonisJS is a TypeScript-first web framework. A Path Traversal vulnerability in AdonisJS multipart file handling may allow a remote attacker to write arbitrary files to arbitrary locations on the server filesystem. This impacts @adonisjs/bodyparser through version 10.1.1 and 11.x prerelease versions prior to 11.0.0-next.6. This issue has been patched in @adonisjs/bodyparser versions 10.1.2 and 11.0.0-next.6.. EPSS: 0.2% exploitation probability",
"x_kev_status": false,
"x_epss_score": 0.00241,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2026-21440",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2026-21440"
},
{
"source_name": "nvd",
"external_id": "CVE-2026-21440",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2026-21440"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--d6d78394-a68a-4742-9c28-bc2485e0a1b5",
"name": "the World Economic Forum",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "International organization focused on global economic issues",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "identity",
"id": "identity--91e4f85a-d9b4-4262-82ee-85b29bb6ba1c",
"name": "CERT/CC",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Computer Emergency Response Team Coordination Center",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 85,
"type": "vulnerability",
"id": "vulnerability--14a890fd-5d24-46d2-99f9-36f5a2ad8bda",
"name": "EX200",
"description": "A wireless range extender model affected by a security flaw.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.556Z",
"modified": "2026-01-06T19:01:09.556Z",
"confidence": 95,
"type": "tool",
"id": "tool--426bfb17-cff4-4d72-9a99-c94bd6712777",
"name": "Trusted Google Notifications Used",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A phishing campaign that abuses Google notifications.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.557Z",
"modified": "2026-01-06T19:01:09.557Z",
"confidence": 95,
"type": "identity",
"id": "identity--0f9dfab5-c9f5-4fef-b687-02b16bd9cd44",
"name": "Cybercrime Magazine",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Cybersecurity news and information website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.557Z",
"modified": "2026-01-06T19:01:09.557Z",
"confidence": 95,
"type": "identity",
"id": "identity--8d960ac4-0bb0-4028-b021-052be9c48439",
"name": "Nir Zuk",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Founder and CTO of Palo Alto Networks",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.557Z",
"modified": "2026-01-06T19:01:09.557Z",
"confidence": 95,
"type": "identity",
"id": "identity--ae1b46f6-1764-46f4-a722-218ee5c1fba5",
"name": "The Cyber Security Agency",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Cybersecurity agency",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.557Z",
"modified": "2026-01-06T19:01:09.557Z",
"confidence": 95,
"type": "identity",
"id": "identity--2daf3eee-ee2d-4a01-b724-90e3ce3a3f4f",
"name": "Thales",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Multinational company that provides cybersecurity solutions",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:09.557Z",
"modified": "2026-01-06T19:01:09.557Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"name": "Exploit Public-Facing Application",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1190",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1190/",
"external_id": "T1190"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"name": "Exploitation for Client Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1203",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1203/",
"external_id": "T1203"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"name": "Command and Scripting Interpreter",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/",
"external_id": "T1059"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"name": "Spearphishing Attachment",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/001/",
"external_id": "T1566.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"name": "Spearphishing Link",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/002/",
"external_id": "T1566.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"name": "Spearphishing via Service",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/003/",
"external_id": "T1566.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"name": "Abuse Elevation Control Mechanism",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1548",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1548/",
"external_id": "T1548"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"name": "Access Token Manipulation",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1134",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1134/",
"external_id": "T1134"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c3286059-b33e-4b64-9fda-22075baf9afa",
"name": "Ingress Tool Transfer",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1105",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1105/",
"external_id": "T1105"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.906Z",
"modified": "2026-01-06T19:01:10.906Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--97050bed-0864-4e3c-9f82-facd1eb7fc63",
"name": "Code Signing",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1553.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1553/002/",
"external_id": "T1553.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--c1ff2266-1a4b-4292-80e6-f593eb2569a9",
"name": "Code Signing Certificates",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1587.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1587/002/",
"external_id": "T1587.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"name": "Browser Extensions",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1176.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1176/001/",
"external_id": "T1176.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--239957f5-5ae1-4977-a451-144fae4a6361",
"name": "Software Extensions",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1176",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1176/",
"external_id": "T1176"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--a29578ca-547d-4c9a-acfd-6742cfae2f22",
"name": "Trap",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1546.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1546/005/",
"external_id": "T1546.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"name": "Botnet",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1583.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1583/005/",
"external_id": "T1583.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--08294e9d-c1e2-46dc-9760-a3537ae37209",
"name": "Local Email Collection",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1114.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1114/001/",
"external_id": "T1114.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--48a7a9f8-a5c6-444a-8cfb-bd9602d2d34e",
"name": "Outlook Rules",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1137.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1137/005/",
"external_id": "T1137.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--5aff02b0-8030-4a6a-bc0c-3ddc61680683",
"name": "Outlook Forms",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1137.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1137/003/",
"external_id": "T1137.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--26d99677-799b-44ed-bc54-5fef76cbc72c",
"name": "Outlook Home Page",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1137.004",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1137/004/",
"external_id": "T1137.004"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 84,
"type": "attack-pattern",
"id": "attack-pattern--4e2f5b9a-cf3a-4ab7-9169-8362c52dd57d",
"name": "Search Threat Vendor Data",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "reconnaissance"
}
],
"x_mitre_id": "T1681",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1681/",
"external_id": "T1681"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 83,
"type": "attack-pattern",
"id": "attack-pattern--b863fbfb-5683-4f21-8c51-9323c0303278",
"name": "Exclusive Control",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1668",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1668/",
"external_id": "T1668"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 74,
"type": "attack-pattern",
"id": "attack-pattern--3785d15d-1c0c-4464-9200-10b744888e29",
"name": "Python Startup Hooks",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1546.018",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1546/018/",
"external_id": "T1546.018"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"name": "Vulnerabilities",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/006/",
"external_id": "T1588.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--92b3199d-f7ae-4a4b-8699-1d01a6761923",
"name": "Office Application Startup",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1137",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1137/",
"external_id": "T1137"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"name": "Scheduled Task",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1053.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1053/005/",
"external_id": "T1053.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"name": "Socket Filters",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1205.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1205/002/",
"external_id": "T1205.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"name": "Archive via Utility",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1560.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1560/001/",
"external_id": "T1560.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"name": "Screen Capture",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1113",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1113/",
"external_id": "T1113"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"name": "Adversary-in-the-Middle",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/",
"external_id": "T1557"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-06T19:01:10.907Z",
"modified": "2026-01-06T19:01:10.907Z",
"confidence": 69,
"type": "attack-pattern",
"id": "attack-pattern--dd0edf90-8f96-4a15-852b-ba611cd81716",
"name": "Python",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/006/",
"external_id": "T1059.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
}
]
}


 CRITICAL ITEMS
CRITICAL ITEMS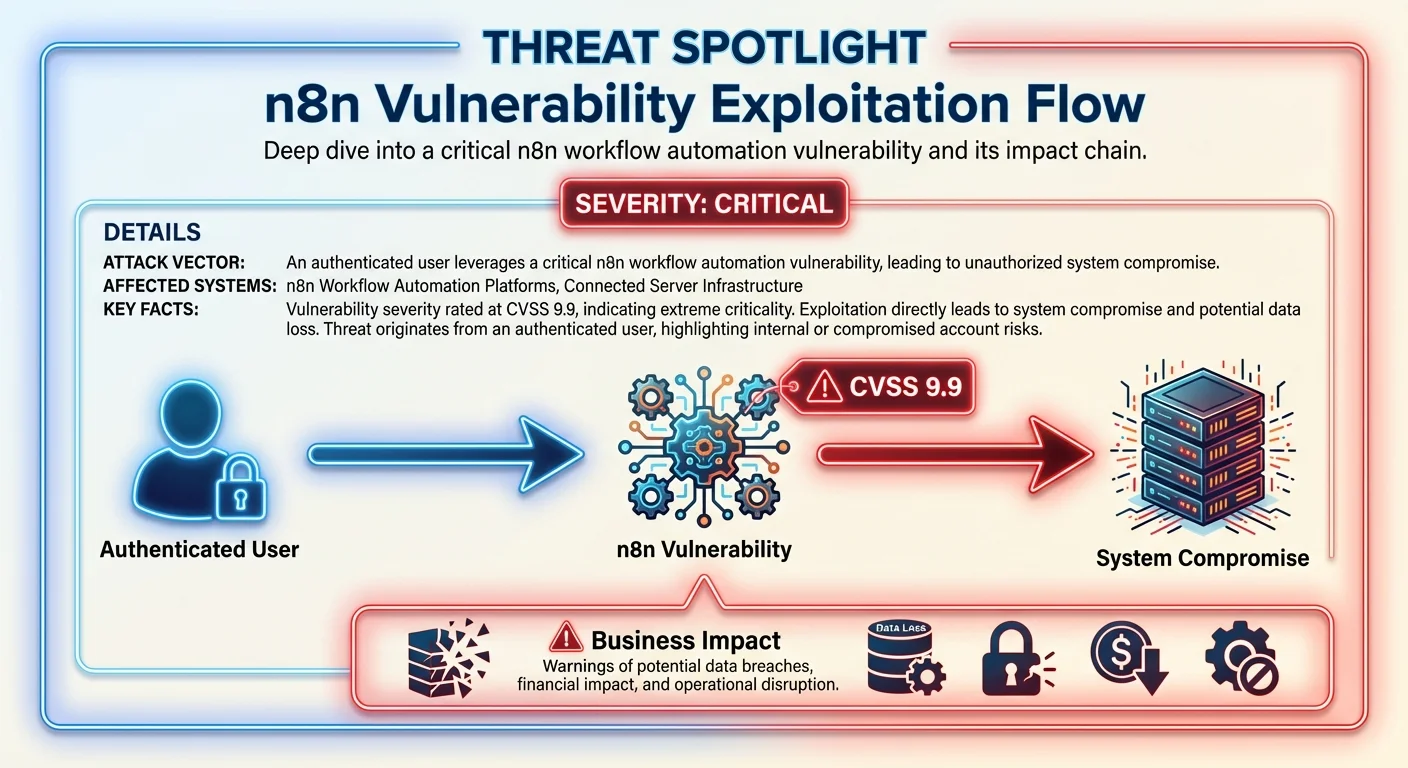
 HIGH SEVERITY ITEMS
HIGH SEVERITY ITEMS
 MEDIUM SEVERITY ITEMS
MEDIUM SEVERITY ITEMS EXECUTIVE INSIGHTS
EXECUTIVE INSIGHTS VENDOR SPOTLIGHT
VENDOR SPOTLIGHT DETECTION & RESPONSE KIT
DETECTION & RESPONSE KIT