[copy]
{
"type": "bundle",
"id": "bundle--3a1ab1c0-da26-4b57-8892-9209d188b63a",
"objects": [
{
"type": "marking-definition",
"spec_version": "2.1",
"id": "marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"created": "2022-10-01T00:00:00.000Z",
"definition_type": "tlp:2.0",
"name": "TLP:CLEAR",
"definition": {
"tlp": "clear"
}
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--eb427775-4952-4eb1-9f29-06e6974d9b57",
"created": "2026-01-05T14:06:45.011Z",
"modified": "2026-01-05T14:06:45.011Z",
"name": "MikeGPT Intelligence Platform",
"description": "AI-powered threat intelligence collection and analysis platform providing automated cybersecurity intelligence feeds",
"identity_class": "organization",
"sectors": [
"technology",
"defense"
],
"contact_information": "Website: https://mikegptai.com | Email: intel@mikegptai.com",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"type": "report",
"spec_version": "2.1",
"id": "report--63234706-a062-43a8-9055-e0c5330b8e74",
"created": "2026-01-05T14:06:45.011Z",
"modified": "2026-01-05T14:06:45.011Z",
"name": "Threat Intelligence Report - 2026-01-05",
"description": "Threat Intelligence Report - 2026-01-05\n\nThis report consolidates actionable cybersecurity intelligence from 58 sources, processed through automated threat analysis and relationship extraction.\n\nKEY FINDINGS:\n• VVS Stealer, a new python malware steals Discord credentials (Score: 100)\n• The State of Cybersecurity in 2025: Key Segments, Insights, and Innovations (Score: 92.5)\n• How much freedom do companies have in choosing NHIs (Score: 92.3)\n• Resecurity Caught ShinyHunters in Honeypot (Score: 91.6)\n• Inside 2025’s Top Threat Groups: Why Familiar Actors Still Have the Upper Hand (Score: 91.5)\n\nEXTRACTED ENTITIES:\n• 19 Attack Pattern(s)\n• 20 Domain Name(s)\n• 19 Indicator(s)\n• 1 Malware(s)\n• 1 Marking Definition(s)\n• 59 Relationship(s)\n• 1 Threat Actor(s)\n• 1 Vulnerability(s)\n\nCONFIDENCE ASSESSMENT:\nVariable confidence scoring applied based on entity type and intelligence source reliability. Confidence ranges from 30-95% reflecting professional intelligence assessment practices.\n\nGENERATION METADATA:\n- Processing Time: Automated\n- Validation: Three-LLM consensus committee\n- Standards Compliance: STIX 2.1\n",
"published": "2026-01-05T14:06:45.011Z",
"object_refs": [
"identity--eb427775-4952-4eb1-9f29-06e6974d9b57",
"identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"identity--4a0ea356-910b-4135-8390-c178705bb54c",
"identity--e835485c-2204-4cf2-a5fa-2b610e6ad752",
"malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"identity--fd1e3790-7e3a-48a3-8684-16f17330c96f",
"threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"identity--f35768f3-134e-41ca-8abb-c57ad1c94b2e",
"identity--2951f191-6f69-42b3-aa1c-698a9b4eb9ed",
"attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"attack-pattern--4a2578d4-fdf6-48d3-b66a-93c681e1e21e",
"attack-pattern--68a5c7b8-09b4-49b1-8149-bc23ed0260c9",
"attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"attack-pattern--3785d15d-1c0c-4464-9200-10b744888e29",
"attack-pattern--dd0edf90-8f96-4a15-852b-ba611cd81716",
"attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"relationship--7e28e104-ca43-475b-aa16-4d11e105bfda",
"relationship--840ba5ce-6972-4c28-a3ce-ebb4ae7b3f55",
"relationship--63e6eb91-3569-43f0-be34-fa6866093965",
"relationship--e47652a4-388f-405b-b222-f1927ff73fda",
"relationship--a111006d-a1de-4c37-bddc-31746eb726de",
"relationship--851d57a8-e0c8-4a3a-8906-383476bb8ee8",
"relationship--8c5594e2-ddab-438a-ab65-98d287cb93f8",
"relationship--8ebcf622-092d-4f7c-b962-c864a8990f99",
"relationship--f7429361-9be1-4143-9661-b67e7b66ee56",
"relationship--dfb01f2d-fb9b-451d-a493-4672e41b5689",
"relationship--8f91c2f5-56a5-4148-83ad-7acf168eadc1",
"relationship--3475f0ae-1da2-499c-977e-25024f8945f4",
"relationship--a04d6b32-dd8f-40f8-afa2-94f201bb7cab",
"relationship--1bd57009-db14-4cae-905a-033f485a9f7d",
"relationship--ab675ad6-aa08-442e-bea5-cdb9faa2baa2",
"relationship--1e7c2d3e-afa3-4cfe-82b7-6a7b03456a46",
"relationship--880cf3b7-1d63-410e-a7ea-2eaec54cddac",
"relationship--781e3d51-0ed0-4fe8-bf62-eb815884ffd3",
"relationship--71da13c5-f17c-4ef5-97ae-9f9a526fdeba",
"relationship--1153c337-8b48-4d09-9b98-ec8210b0f33e",
"relationship--a1acae6a-61dd-449d-8d48-749666722783",
"relationship--200987bf-ade3-4cb8-8aa0-eeebb54ae84e",
"relationship--dd28e102-45ab-4f85-9425-a88f348ff777",
"relationship--7a886373-79af-49ed-b49e-b819895bc7d7",
"relationship--c14654ff-308a-4374-abe5-da35bf9c4ed9",
"relationship--295be3e6-feea-409a-898b-22e5d826c94b",
"relationship--acf92195-329a-42c8-a715-aecf7ca2ca9b",
"relationship--0bd8ee24-1c83-40d1-91c6-36f31fb8d0b7",
"relationship--6cc82ff8-807a-4e65-ad4e-ffd60102a84b",
"relationship--4c56e261-03e6-4e9f-9eb6-3ff0f271ec34",
"relationship--4c8ef359-66a1-4922-a878-34d16bcb6a8d",
"relationship--2b5f4538-3787-4db2-956a-c324ec0b96d4",
"relationship--926d006a-477a-4c7d-9e0f-662c219d2603",
"relationship--c850ca01-99f9-42b3-915b-90e58f7084c1",
"relationship--5ecd41cd-c283-4a01-a172-1e78516ffd42",
"relationship--a1b4549b-54c8-430a-98d3-2994df32493e",
"relationship--9cfc839a-8858-4a5e-8426-864662f5541f",
"relationship--af24cb56-a872-4ae8-a5dc-59b9ed26bbc7",
"relationship--22873d1c-30d5-4d9f-b48b-bea7f7149836",
"relationship--a52cccf5-6cda-4544-ab91-3fa2eede818d",
"domain-name--f44a3e7d-f587-4cdd-9949-283c5cd1335e",
"domain-name--2fdcc0fd-b725-43f9-b5b4-99240751fcff",
"domain-name--ef7854c7-9539-4262-8290-5bcbf50ab775",
"domain-name--03af35ad-7e7c-4d40-a8a2-5067bcfb00e0",
"domain-name--c58f7fd3-9580-4b12-aebc-54594561001c",
"domain-name--60a81ccb-4c79-4592-bc88-4e0639e9e4cc",
"domain-name--f97fb410-27e7-4075-bb76-a7ad537992f8",
"domain-name--ea2675b0-770e-4bb8-9abe-ee2f6be369d2",
"domain-name--d4b5aa1a-fada-48f7-8d8c-f3e70123172d",
"domain-name--e618702b-a9e5-47b8-b6a5-76d950f66160",
"domain-name--59a2fa3a-3251-4111-b92b-72abb5dbdf73",
"domain-name--0cecfccc-c1c8-4a76-911f-f5014ed8d5ed",
"domain-name--2289ca05-9f5e-499f-adaf-7f45b42f3d3c",
"domain-name--ae0848e5-e1b1-4a79-ac31-ed99c772219a",
"domain-name--78595c4b-49e3-4afd-903b-896e42be32a7",
"domain-name--0bca8a93-ee54-47d1-aaf9-feea58aeea08",
"domain-name--41da804e-4fce-4ad4-9d23-a3b3020aade1",
"domain-name--2637af3e-22f0-403f-8082-510b4da08f29",
"domain-name--5ecf1d8c-3453-402e-b831-ac23ffc53e44",
"domain-name--a343d34f-218b-42e9-a41d-d2f15f147373",
"indicator--16ca63a1-20b9-485a-a52d-6165558fcdc7",
"relationship--4dd371f0-bcff-49de-bafe-d3e2c3a663dc",
"indicator--47d2ab3a-5024-41df-8978-8afd670048da",
"relationship--6f6313f5-6e44-4bc8-a3f2-262466ba7b36",
"indicator--71d5fc2b-cbd4-4c1c-90f9-aeaf729e534b",
"relationship--ed8b1606-7583-4aa7-9253-a7a779808f72",
"indicator--c5c5dd73-50a2-4b9e-97f3-c0bcd0d6e0fc",
"relationship--3f385395-9a4d-4067-b23e-b2aae1e32d5d",
"indicator--300b4d35-4015-4dce-bb0e-1e3b3692b2f1",
"relationship--e0a23bf6-c745-4dcd-87af-89739a207bc4",
"indicator--424a1b88-8cd4-4dca-b94a-ad7deeb7bfe6",
"relationship--2a03d184-1635-47bf-bff3-c3ef72f108d4",
"indicator--7aabdbcb-6347-4e30-b754-857317deab05",
"relationship--c733dd07-3dd7-4f0f-adf6-1fa1b20c132a",
"indicator--3f8e75ca-0d33-46ca-af36-af2fbec8fade",
"relationship--2c864e5c-33b9-42ea-aed2-21247e947119",
"indicator--b545b177-8725-4513-91c8-2b4770a4da0b",
"relationship--e20edb50-de0a-4193-a47c-cd4f220db0bb",
"indicator--b0581143-624a-41b0-b12b-1047da0440ee",
"relationship--a999e2be-79c7-4de9-81c3-faff25360b72",
"indicator--e7e82a1c-b4a9-4b0c-9eed-45f330ef3c9a",
"relationship--7a03c15b-7911-4297-945a-e6ff5fcb6e31",
"indicator--e14688ce-d548-4a82-9f27-a6d3c0065ec3",
"relationship--854f306e-e7cb-4953-bf30-ef155ee99fb0",
"indicator--22774028-d761-46d0-b44c-5e6e4265298a",
"relationship--f5e29adc-906e-47a7-8a40-e2f078b8dcb3",
"indicator--1c8bca62-116b-4bad-8707-874ae76fa57b",
"relationship--edf804f3-e18c-4164-bba7-d80636734c29",
"indicator--c83e88dc-6d99-48ce-8c83-89daffc7f385",
"relationship--c0f666b4-fac3-4fd4-8035-c5ad8480e058",
"indicator--937de08c-0378-438f-a30f-f0fa44456d6e",
"relationship--3f4f3193-31c7-4e81-8344-b27d21ddd56b",
"indicator--0005d72e-dba8-491f-8486-dbabc3cbaeb4",
"relationship--d4b4c8ae-c6f8-47d3-8931-106c8b2afcc3",
"indicator--4bb2bacb-7ab8-46fa-8244-09836e1d6513",
"relationship--eef44fa2-5708-4e3d-9380-8681b049a1b8",
"indicator--6fad657f-97d4-4547-b518-9f6902d50bf2",
"relationship--0f06e52e-aab5-4899-b263-a9615912ce8f"
],
"labels": [
"threat-report",
"threat-intelligence"
],
"created_by_ref": "identity--eb427775-4952-4eb1-9f29-06e6974d9b57",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.844Z",
"modified": "2026-01-05T14:06:43.844Z",
"confidence": 95,
"type": "identity",
"id": "identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"name": "Non-Human Identities",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "identity",
"id": "identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"name": "Security Boulevard",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "identity",
"id": "identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"name": "China",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "China is a country.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"name": "SecurityWeek",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "identity",
"id": "identity--4a0ea356-910b-4135-8390-c178705bb54c",
"name": "LinkedIn",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "LinkedIn is a social networking platform designed for professionals and businesses to connect and share information. As a major online platform, LinkedIn's data is a valuable target for threat actors seeking to exploit professional networks for social engineering attacks. The exposure of 4.3 billion professional records, including LinkedIn data, poses a significant risk to individuals and organizations, enabling large-scale AI-driven social engineering attacks.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "identity",
"id": "identity--e835485c-2204-4cf2-a5fa-2b610e6ad752",
"name": "Mandiant",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Mandiant is a leading cybersecurity firm specializing in incident response, threat intelligence, and security consulting services, helping organizations protect themselves against advanced cyber threats and cyber attacks.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "malware",
"id": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"name": "VVS Stealer",
"is_family": true,
"malware_types": [
"stealer"
],
"labels": [
"malicious-activity"
],
"description": "A Python-based malware that steals Discord credentials and tokens.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "identity",
"id": "identity--fd1e3790-7e3a-48a3-8684-16f17330c96f",
"name": "Palo Alto Networks",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity company.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "threat-actor",
"id": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"name": "ShinyHunters",
"threat_actor_types": [
"hacker"
],
"labels": [
"threat-actor"
],
"description": "A threat actor group.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 95,
"type": "identity",
"id": "identity--f35768f3-134e-41ca-8abb-c57ad1c94b2e",
"name": "Resecurity",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity company.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 90,
"type": "identity",
"id": "identity--2951f191-6f69-42b3-aa1c-698a9b4eb9ed",
"name": "Tianpei Lu",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A person.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:43.845Z",
"modified": "2026-01-05T14:06:43.845Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"name": "Supply Chain Compromise",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1195",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1195/",
"external_id": "T1195"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"name": "Exploit Public-Facing Application",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1190",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1190/",
"external_id": "T1190"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"name": "Exploitation for Client Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1203",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1203/",
"external_id": "T1203"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"name": "Spearphishing Attachment",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/001/",
"external_id": "T1566.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"name": "Spearphishing Link",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/002/",
"external_id": "T1566.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"name": "Spearphishing via Service",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/003/",
"external_id": "T1566.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"name": "Modify Registry",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1112",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1112/",
"external_id": "T1112"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"name": "Registry Run Keys / Startup Folder",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/001/",
"external_id": "T1547.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--4a2578d4-fdf6-48d3-b66a-93c681e1e21e",
"name": "Application Layer Protocol",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1071",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1071/",
"external_id": "T1071"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--68a5c7b8-09b4-49b1-8149-bc23ed0260c9",
"name": "Non-Application Layer Protocol",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1095",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1095/",
"external_id": "T1095"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"name": "Botnet",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1583.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1583/005/",
"external_id": "T1583.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 79,
"type": "attack-pattern",
"id": "attack-pattern--3785d15d-1c0c-4464-9200-10b744888e29",
"name": "Python Startup Hooks",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1546.018",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1546/018/",
"external_id": "T1546.018"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 78,
"type": "attack-pattern",
"id": "attack-pattern--dd0edf90-8f96-4a15-852b-ba611cd81716",
"name": "Python",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/006/",
"external_id": "T1059.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"name": "Archive via Utility",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1560.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1560/001/",
"external_id": "T1560.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"name": "Screen Capture",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1113",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1113/",
"external_id": "T1113"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"name": "Adversary-in-the-Middle",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/",
"external_id": "T1557"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"name": "Scheduled Task",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1053.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1053/005/",
"external_id": "T1053.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"name": "Socket Filters",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1205.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1205/002/",
"external_id": "T1205.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"name": "Boot or Logon Initialization Scripts",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1037",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1037/",
"external_id": "T1037"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--7e28e104-ca43-475b-aa16-4d11e105bfda",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Supply Chain Compromise (T1195) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--840ba5ce-6972-4c28-a3ce-ebb4ae7b3f55",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Exploit Public-Facing Application (T1190) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--63e6eb91-3569-43f0-be34-fa6866093965",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Exploitation for Client Execution (T1203) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e47652a4-388f-405b-b222-f1927ff73fda",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Spearphishing Attachment (T1566.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a111006d-a1de-4c37-bddc-31746eb726de",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Spearphishing Link (T1566.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--851d57a8-e0c8-4a3a-8906-383476bb8ee8",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Spearphishing via Service (T1566.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--8c5594e2-ddab-438a-ab65-98d287cb93f8",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Modify Registry (T1112) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--8ebcf622-092d-4f7c-b962-c864a8990f99",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Registry Run Keys / Startup Folder (T1547.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--f7429361-9be1-4143-9661-b67e7b66ee56",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--4a2578d4-fdf6-48d3-b66a-93c681e1e21e",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Application Layer Protocol (T1071) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--dfb01f2d-fb9b-451d-a493-4672e41b5689",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--68a5c7b8-09b4-49b1-8149-bc23ed0260c9",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Non-Application Layer Protocol (T1095) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--8f91c2f5-56a5-4148-83ad-7acf168eadc1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Botnet (T1583.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3475f0ae-1da2-499c-977e-25024f8945f4",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Botnet (T1584.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a04d6b32-dd8f-40f8-afa2-94f201bb7cab",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--3785d15d-1c0c-4464-9200-10b744888e29",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Python Startup Hooks (T1546.018) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1bd57009-db14-4cae-905a-033f485a9f7d",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--dd0edf90-8f96-4a15-852b-ba611cd81716",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Python (T1059.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ab675ad6-aa08-442e-bea5-cdb9faa2baa2",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Archive via Utility (T1560.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1e7c2d3e-afa3-4cfe-82b7-6a7b03456a46",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Screen Capture (T1113) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--880cf3b7-1d63-410e-a7ea-2eaec54cddac",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Adversary-in-the-Middle (T1557) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--781e3d51-0ed0-4fe8-bf62-eb815884ffd3",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Scheduled Task (T1053.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--71da13c5-f17c-4ef5-97ae-9f9a526fdeba",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Socket Filters (T1205.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1153c337-8b48-4d09-9b98-ec8210b0f33e",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "threat-actor--1c24883b-5440-48be-89b4-b0c9d2b0646b",
"target_ref": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"confidence": 60,
"description": "Co-occurrence: ShinyHunters and Boot or Logon Initialization Scripts (T1037) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a1acae6a-61dd-449d-8d48-749666722783",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Supply Chain Compromise (T1195) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--200987bf-ade3-4cb8-8aa0-eeebb54ae84e",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Exploit Public-Facing Application (T1190) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--dd28e102-45ab-4f85-9425-a88f348ff777",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Exploitation for Client Execution (T1203) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--7a886373-79af-49ed-b49e-b819895bc7d7",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Spearphishing Attachment (T1566.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c14654ff-308a-4374-abe5-da35bf9c4ed9",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Spearphishing Link (T1566.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--295be3e6-feea-409a-898b-22e5d826c94b",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Spearphishing via Service (T1566.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--acf92195-329a-42c8-a715-aecf7ca2ca9b",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Modify Registry (T1112) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--0bd8ee24-1c83-40d1-91c6-36f31fb8d0b7",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Registry Run Keys / Startup Folder (T1547.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--6cc82ff8-807a-4e65-ad4e-ffd60102a84b",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--4a2578d4-fdf6-48d3-b66a-93c681e1e21e",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Application Layer Protocol (T1071) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4c56e261-03e6-4e9f-9eb6-3ff0f271ec34",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--68a5c7b8-09b4-49b1-8149-bc23ed0260c9",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Non-Application Layer Protocol (T1095) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4c8ef359-66a1-4922-a878-34d16bcb6a8d",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Botnet (T1583.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2b5f4538-3787-4db2-956a-c324ec0b96d4",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Botnet (T1584.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--926d006a-477a-4c7d-9e0f-662c219d2603",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--3785d15d-1c0c-4464-9200-10b744888e29",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Python Startup Hooks (T1546.018) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c850ca01-99f9-42b3-915b-90e58f7084c1",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--dd0edf90-8f96-4a15-852b-ba611cd81716",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Python (T1059.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5ecd41cd-c283-4a01-a172-1e78516ffd42",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Archive via Utility (T1560.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a1b4549b-54c8-430a-98d3-2994df32493e",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Screen Capture (T1113) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--9cfc839a-8858-4a5e-8426-864662f5541f",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Adversary-in-the-Middle (T1557) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--af24cb56-a872-4ae8-a5dc-59b9ed26bbc7",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Scheduled Task (T1053.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--22873d1c-30d5-4d9f-b48b-bea7f7149836",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Socket Filters (T1205.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a52cccf5-6cda-4544-ab91-3fa2eede818d",
"created": "2026-01-05T14:06:45.010Z",
"modified": "2026-01-05T14:06:45.010Z",
"relationship_type": "uses",
"source_ref": "malware--d926775c-3968-4c2f-b643-f7b66cd67894",
"target_ref": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"confidence": 55,
"description": "Co-occurrence: VVS Stealer and Boot or Logon Initialization Scripts (T1037) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "domain-name",
"value": "0paypal.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--f44a3e7d-f587-4cdd-9949-283c5cd1335e"
},
{
"type": "domain-name",
"value": "account-page-recovery-process.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--2fdcc0fd-b725-43f9-b5b4-99240751fcff"
},
{
"type": "domain-name",
"value": "accountingsure.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--ef7854c7-9539-4262-8290-5bcbf50ab775"
},
{
"type": "domain-name",
"value": "alamatpaypal.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--03af35ad-7e7c-4d40-a8a2-5067bcfb00e0"
},
{
"type": "domain-name",
"value": "amazon-update.xyz",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--c58f7fd3-9580-4b12-aebc-54594561001c"
},
{
"type": "domain-name",
"value": "appleid-fmi.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--60a81ccb-4c79-4592-bc88-4e0639e9e4cc"
},
{
"type": "domain-name",
"value": "appleid-manageids.info",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--f97fb410-27e7-4075-bb76-a7ad537992f8"
},
{
"type": "domain-name",
"value": "applessecure.site",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--ea2675b0-770e-4bb8-9abe-ee2f6be369d2"
},
{
"type": "domain-name",
"value": "auth-03chase.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--d4b5aa1a-fada-48f7-8d8c-f3e70123172d"
},
{
"type": "domain-name",
"value": "banking-commbank.support",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--e618702b-a9e5-47b8-b6a5-76d950f66160"
},
{
"type": "domain-name",
"value": "citi-securelogin.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--59a2fa3a-3251-4111-b92b-72abb5dbdf73"
},
{
"type": "domain-name",
"value": "claireapplewhite.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--0cecfccc-c1c8-4a76-911f-f5014ed8d5ed"
},
{
"type": "domain-name",
"value": "cvwwwe9851.xyz",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--2289ca05-9f5e-499f-adaf-7f45b42f3d3c"
},
{
"type": "domain-name",
"value": "docsaccount.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--ae0848e5-e1b1-4a79-ac31-ed99c772219a"
},
{
"type": "domain-name",
"value": "ebankingcode.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--78595c4b-49e3-4afd-903b-896e42be32a7"
},
{
"type": "domain-name",
"value": "hbsc-payment.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--0bca8a93-ee54-47d1-aaf9-feea58aeea08"
},
{
"type": "domain-name",
"value": "hotelesanticrisis.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--41da804e-4fce-4ad4-9d23-a3b3020aade1"
},
{
"type": "domain-name",
"value": "https8xmao.xyz",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--2637af3e-22f0-403f-8082-510b4da08f29"
},
{
"type": "domain-name",
"value": "icloudfindsimap.com",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--5ecf1d8c-3453-402e-b831-ac23ffc53e44"
},
{
"type": "domain-name",
"value": "imap-support.info",
"source": "OTX",
"malware_families": [
"VVS Stealer"
],
"pulse_names": [
"Phishing & scam domain names"
],
"id": "domain-name--a343d34f-218b-42e9-a41d-d2f15f147373"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--16ca63a1-20b9-485a-a52d-6165558fcdc7",
"created": "2026-01-05T14:06:32.766Z",
"modified": "2026-01-05T14:06:32.766Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = '0paypal.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.767Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4dd371f0-bcff-49de-bafe-d3e2c3a663dc",
"created": "2026-01-05T14:06:32.767Z",
"modified": "2026-01-05T14:06:32.767Z",
"relationship_type": "based-on",
"source_ref": "indicator--16ca63a1-20b9-485a-a52d-6165558fcdc7",
"target_ref": "domain-name--f44a3e7d-f587-4cdd-9949-283c5cd1335e"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--47d2ab3a-5024-41df-8978-8afd670048da",
"created": "2026-01-05T14:06:32.778Z",
"modified": "2026-01-05T14:06:32.778Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'account-page-recovery-process.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.778Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--6f6313f5-6e44-4bc8-a3f2-262466ba7b36",
"created": "2026-01-05T14:06:32.778Z",
"modified": "2026-01-05T14:06:32.778Z",
"relationship_type": "based-on",
"source_ref": "indicator--47d2ab3a-5024-41df-8978-8afd670048da",
"target_ref": "domain-name--2fdcc0fd-b725-43f9-b5b4-99240751fcff"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--71d5fc2b-cbd4-4c1c-90f9-aeaf729e534b",
"created": "2026-01-05T14:06:32.786Z",
"modified": "2026-01-05T14:06:32.786Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'accountingsure.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.786Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ed8b1606-7583-4aa7-9253-a7a779808f72",
"created": "2026-01-05T14:06:32.786Z",
"modified": "2026-01-05T14:06:32.786Z",
"relationship_type": "based-on",
"source_ref": "indicator--71d5fc2b-cbd4-4c1c-90f9-aeaf729e534b",
"target_ref": "domain-name--ef7854c7-9539-4262-8290-5bcbf50ab775"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--c5c5dd73-50a2-4b9e-97f3-c0bcd0d6e0fc",
"created": "2026-01-05T14:06:32.796Z",
"modified": "2026-01-05T14:06:32.796Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'alamatpaypal.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.796Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3f385395-9a4d-4067-b23e-b2aae1e32d5d",
"created": "2026-01-05T14:06:32.796Z",
"modified": "2026-01-05T14:06:32.796Z",
"relationship_type": "based-on",
"source_ref": "indicator--c5c5dd73-50a2-4b9e-97f3-c0bcd0d6e0fc",
"target_ref": "domain-name--03af35ad-7e7c-4d40-a8a2-5067bcfb00e0"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--300b4d35-4015-4dce-bb0e-1e3b3692b2f1",
"created": "2026-01-05T14:06:32.805Z",
"modified": "2026-01-05T14:06:32.805Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'amazon-update.xyz']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.805Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e0a23bf6-c745-4dcd-87af-89739a207bc4",
"created": "2026-01-05T14:06:32.805Z",
"modified": "2026-01-05T14:06:32.805Z",
"relationship_type": "based-on",
"source_ref": "indicator--300b4d35-4015-4dce-bb0e-1e3b3692b2f1",
"target_ref": "domain-name--c58f7fd3-9580-4b12-aebc-54594561001c"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--424a1b88-8cd4-4dca-b94a-ad7deeb7bfe6",
"created": "2026-01-05T14:06:32.813Z",
"modified": "2026-01-05T14:06:32.813Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'appleid-fmi.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.813Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2a03d184-1635-47bf-bff3-c3ef72f108d4",
"created": "2026-01-05T14:06:32.813Z",
"modified": "2026-01-05T14:06:32.813Z",
"relationship_type": "based-on",
"source_ref": "indicator--424a1b88-8cd4-4dca-b94a-ad7deeb7bfe6",
"target_ref": "domain-name--60a81ccb-4c79-4592-bc88-4e0639e9e4cc"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--7aabdbcb-6347-4e30-b754-857317deab05",
"created": "2026-01-05T14:06:32.822Z",
"modified": "2026-01-05T14:06:32.822Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'appleid-manageids.info']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.822Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c733dd07-3dd7-4f0f-adf6-1fa1b20c132a",
"created": "2026-01-05T14:06:32.822Z",
"modified": "2026-01-05T14:06:32.822Z",
"relationship_type": "based-on",
"source_ref": "indicator--7aabdbcb-6347-4e30-b754-857317deab05",
"target_ref": "domain-name--f97fb410-27e7-4075-bb76-a7ad537992f8"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--3f8e75ca-0d33-46ca-af36-af2fbec8fade",
"created": "2026-01-05T14:06:32.830Z",
"modified": "2026-01-05T14:06:32.830Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'applessecure.site']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.830Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2c864e5c-33b9-42ea-aed2-21247e947119",
"created": "2026-01-05T14:06:32.830Z",
"modified": "2026-01-05T14:06:32.830Z",
"relationship_type": "based-on",
"source_ref": "indicator--3f8e75ca-0d33-46ca-af36-af2fbec8fade",
"target_ref": "domain-name--ea2675b0-770e-4bb8-9abe-ee2f6be369d2"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--b545b177-8725-4513-91c8-2b4770a4da0b",
"created": "2026-01-05T14:06:32.839Z",
"modified": "2026-01-05T14:06:32.839Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'auth-03chase.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.839Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e20edb50-de0a-4193-a47c-cd4f220db0bb",
"created": "2026-01-05T14:06:32.839Z",
"modified": "2026-01-05T14:06:32.839Z",
"relationship_type": "based-on",
"source_ref": "indicator--b545b177-8725-4513-91c8-2b4770a4da0b",
"target_ref": "domain-name--d4b5aa1a-fada-48f7-8d8c-f3e70123172d"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--b0581143-624a-41b0-b12b-1047da0440ee",
"created": "2026-01-05T14:06:32.848Z",
"modified": "2026-01-05T14:06:32.848Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'banking-commbank.support']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.848Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a999e2be-79c7-4de9-81c3-faff25360b72",
"created": "2026-01-05T14:06:32.848Z",
"modified": "2026-01-05T14:06:32.848Z",
"relationship_type": "based-on",
"source_ref": "indicator--b0581143-624a-41b0-b12b-1047da0440ee",
"target_ref": "domain-name--e618702b-a9e5-47b8-b6a5-76d950f66160"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--e7e82a1c-b4a9-4b0c-9eed-45f330ef3c9a",
"created": "2026-01-05T14:06:32.855Z",
"modified": "2026-01-05T14:06:32.855Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'citi-securelogin.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.855Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--7a03c15b-7911-4297-945a-e6ff5fcb6e31",
"created": "2026-01-05T14:06:32.855Z",
"modified": "2026-01-05T14:06:32.855Z",
"relationship_type": "based-on",
"source_ref": "indicator--e7e82a1c-b4a9-4b0c-9eed-45f330ef3c9a",
"target_ref": "domain-name--59a2fa3a-3251-4111-b92b-72abb5dbdf73"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--e14688ce-d548-4a82-9f27-a6d3c0065ec3",
"created": "2026-01-05T14:06:32.864Z",
"modified": "2026-01-05T14:06:32.864Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'claireapplewhite.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.864Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--854f306e-e7cb-4953-bf30-ef155ee99fb0",
"created": "2026-01-05T14:06:32.864Z",
"modified": "2026-01-05T14:06:32.864Z",
"relationship_type": "based-on",
"source_ref": "indicator--e14688ce-d548-4a82-9f27-a6d3c0065ec3",
"target_ref": "domain-name--0cecfccc-c1c8-4a76-911f-f5014ed8d5ed"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--22774028-d761-46d0-b44c-5e6e4265298a",
"created": "2026-01-05T14:06:32.872Z",
"modified": "2026-01-05T14:06:32.872Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'cvwwwe9851.xyz']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.872Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--f5e29adc-906e-47a7-8a40-e2f078b8dcb3",
"created": "2026-01-05T14:06:32.872Z",
"modified": "2026-01-05T14:06:32.872Z",
"relationship_type": "based-on",
"source_ref": "indicator--22774028-d761-46d0-b44c-5e6e4265298a",
"target_ref": "domain-name--2289ca05-9f5e-499f-adaf-7f45b42f3d3c"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--1c8bca62-116b-4bad-8707-874ae76fa57b",
"created": "2026-01-05T14:06:32.880Z",
"modified": "2026-01-05T14:06:32.880Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'docsaccount.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.880Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--edf804f3-e18c-4164-bba7-d80636734c29",
"created": "2026-01-05T14:06:32.880Z",
"modified": "2026-01-05T14:06:32.880Z",
"relationship_type": "based-on",
"source_ref": "indicator--1c8bca62-116b-4bad-8707-874ae76fa57b",
"target_ref": "domain-name--ae0848e5-e1b1-4a79-ac31-ed99c772219a"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--c83e88dc-6d99-48ce-8c83-89daffc7f385",
"created": "2026-01-05T14:06:32.889Z",
"modified": "2026-01-05T14:06:32.889Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'ebankingcode.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.889Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c0f666b4-fac3-4fd4-8035-c5ad8480e058",
"created": "2026-01-05T14:06:32.889Z",
"modified": "2026-01-05T14:06:32.889Z",
"relationship_type": "based-on",
"source_ref": "indicator--c83e88dc-6d99-48ce-8c83-89daffc7f385",
"target_ref": "domain-name--78595c4b-49e3-4afd-903b-896e42be32a7"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--937de08c-0378-438f-a30f-f0fa44456d6e",
"created": "2026-01-05T14:06:32.897Z",
"modified": "2026-01-05T14:06:32.897Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'hbsc-payment.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.897Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3f4f3193-31c7-4e81-8344-b27d21ddd56b",
"created": "2026-01-05T14:06:32.897Z",
"modified": "2026-01-05T14:06:32.897Z",
"relationship_type": "based-on",
"source_ref": "indicator--937de08c-0378-438f-a30f-f0fa44456d6e",
"target_ref": "domain-name--0bca8a93-ee54-47d1-aaf9-feea58aeea08"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--0005d72e-dba8-491f-8486-dbabc3cbaeb4",
"created": "2026-01-05T14:06:32.905Z",
"modified": "2026-01-05T14:06:32.905Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'hotelesanticrisis.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.905Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d4b4c8ae-c6f8-47d3-8931-106c8b2afcc3",
"created": "2026-01-05T14:06:32.905Z",
"modified": "2026-01-05T14:06:32.905Z",
"relationship_type": "based-on",
"source_ref": "indicator--0005d72e-dba8-491f-8486-dbabc3cbaeb4",
"target_ref": "domain-name--41da804e-4fce-4ad4-9d23-a3b3020aade1"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--4bb2bacb-7ab8-46fa-8244-09836e1d6513",
"created": "2026-01-05T14:06:32.922Z",
"modified": "2026-01-05T14:06:32.922Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'icloudfindsimap.com']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.922Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--eef44fa2-5708-4e3d-9380-8681b049a1b8",
"created": "2026-01-05T14:06:32.922Z",
"modified": "2026-01-05T14:06:32.922Z",
"relationship_type": "based-on",
"source_ref": "indicator--4bb2bacb-7ab8-46fa-8244-09836e1d6513",
"target_ref": "domain-name--5ecf1d8c-3453-402e-b831-ac23ffc53e44"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--6fad657f-97d4-4547-b518-9f6902d50bf2",
"created": "2026-01-05T14:06:32.931Z",
"modified": "2026-01-05T14:06:32.931Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'imap-support.info']",
"pattern_type": "stix",
"valid_from": "2026-01-05T14:06:32.931Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--0f06e52e-aab5-4899-b263-a9615912ce8f",
"created": "2026-01-05T14:06:32.931Z",
"modified": "2026-01-05T14:06:32.931Z",
"relationship_type": "based-on",
"source_ref": "indicator--6fad657f-97d4-4547-b518-9f6902d50bf2",
"target_ref": "domain-name--a343d34f-218b-42e9-a41d-d2f15f147373"
}
]
}

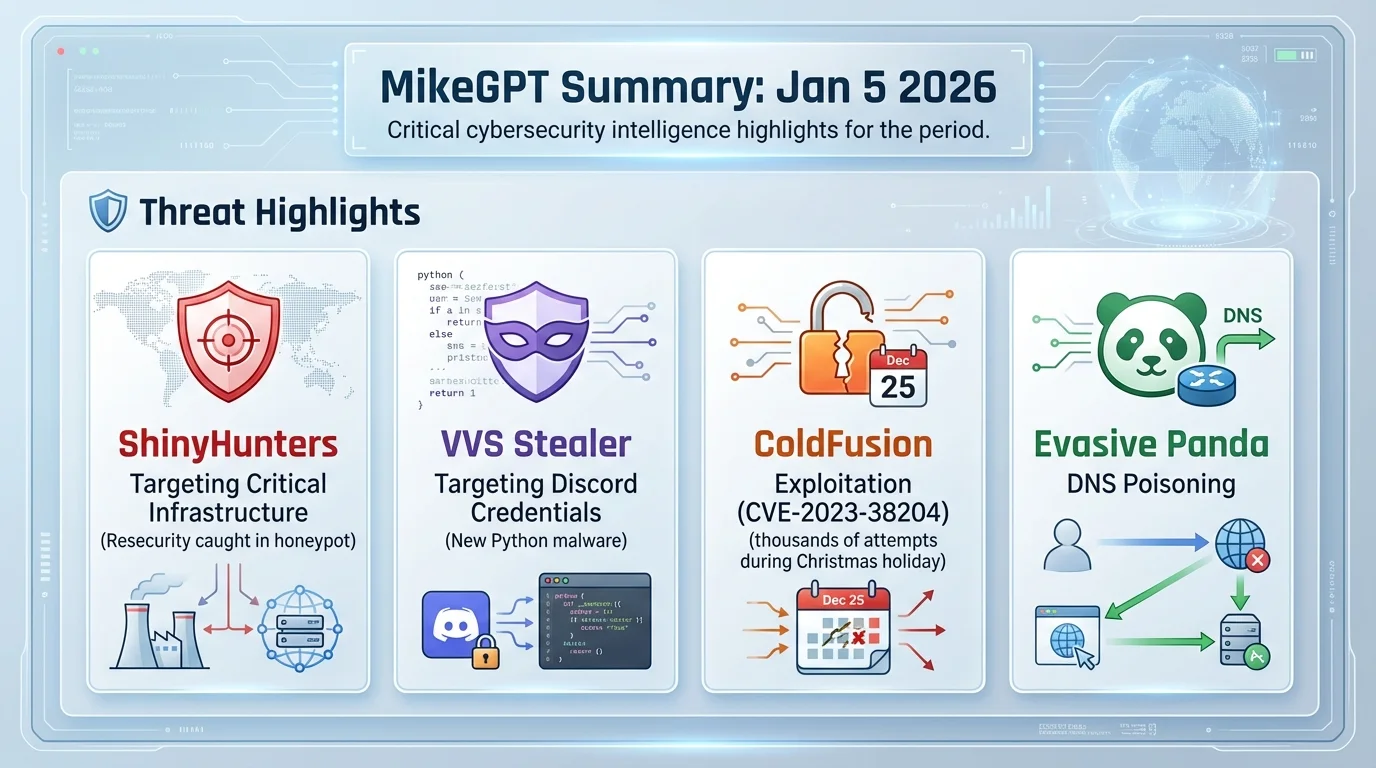
 CRITICAL ITEMS
CRITICAL ITEMS
 HIGH SEVERITY ITEMS
HIGH SEVERITY ITEMS MEDIUM SEVERITY ITEMS
MEDIUM SEVERITY ITEMS EXECUTIVE INSIGHTS
EXECUTIVE INSIGHTS VENDOR SPOTLIGHT
VENDOR SPOTLIGHT DETECTION & RESPONSE KIT
DETECTION & RESPONSE KIT