
Playbook for the Secure Enterprise



Thu, Jan 1, 2026 • 7-minute read
Heroes, Happy New Year! Here's a curated look at the current cybersecurity landscape for January 1, 2026.
Date & Time: 2025-12-31T13:37:00
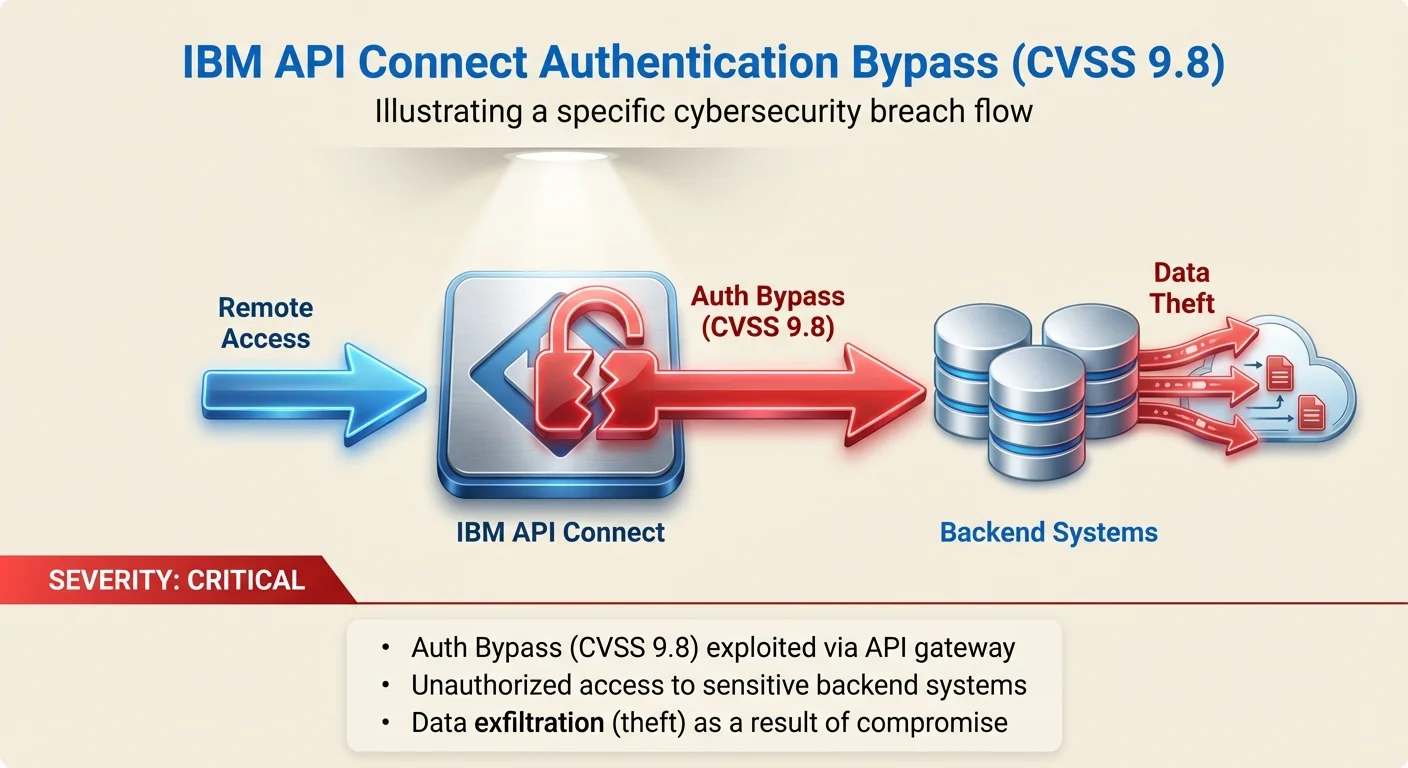
IBM has disclosed a critical 9.8 CVSS vulnerability in its API Connect platform that allows attackers to bypass authentication and gain remote access. This flaw undermines the security gateway managing your organization's APIs.
CVE: CVE-2025-13915 | Compliance: SOX | Source: The Hacker News ↗
Date & Time: 2025-12-31T14:23:11
Singapore's Cyber Security Agency has issued a warning for a perfect 10.0 CVSS severity vulnerability in SmarterMail that allows unauthenticated attackers to execute arbitrary code via file upload. This flaw permits complete server takeover without requiring any credentials.
CVE: CVE-2025-52691 | Compliance: SOX, FISMA | Source: Security Affairs ↗
Date & Time: 2025-12-31T14:58:51
The RondoDox botnet is actively exploiting the critical React2Shell vulnerability in Next.js servers to deploy malware and cryptominers. This campaign specifically targets unpatched web application infrastructure.
CVE: CVE-2025-55182 | Compliance: CMMC | Source: BleepingComputer ↗
Date & Time: 2025-12-31T07:22:40
Two former employees of cybersecurity incident response firms have pleaded guilty to conducting BlackCat ransomware attacks against U.S. companies. This highlights a critical insider threat risk where trusted security personnel leveraged their skills for cybercrime.
CVE: n/a | Compliance: SOX, FISMA | Source: Lifeboat ↗

Date & Time: 2026-01-01T03:10:22
A massive malicious browser extension campaign codenamed DarkSpectre (linked to ShadyPanda and GhostPoster) has compromised over 8.8 million users across Chrome, Edge, and Firefox. The extensions are used to steal data and track user activity.
CVE: n/a | Compliance: SOX | Source: Lifeboat ↗
Date & Time: 2025-12-31T15:00:01
Research from SquareX reveals that Browser AI Agents are now more susceptible to cyberattacks than human employees, becoming a new primary attack vector. These automated agents can be manipulated to perform unauthorized actions.
CVE: n/a | Compliance: SOX | Source: Security Boulevard ↗
Date & Time: 2025-12-31T14:00:24
A mysterious outage in China's Great Firewall blocked all HTTPS connections on port 443 for over an hour, preventing access to foreign websites. This suggests potential testing of new censorship or cyber-warfare capabilities.
CVE: n/a | Compliance: SOX | Source: Security Boulevard ↗
Date & Time: 2025-12-30T20:11:35
New data indicates that nearly 60% of enterprise firewalls fail at least one high-severity check during audits, primarily due to misconfigurations. This highlights a widespread failure in basic network security hygiene.
CVE: n/a | Compliance: SOX | Source: FireMon ↗
Date & Time: 2025-12-31T12:40:09
December 2025 concluded with significant breaches in retail, education, and healthcare, driven by misconfigurations and unpatched vulnerabilities. This summary serves as a retrospective on the month's threat landscape.
CVE: n/a | Compliance: HIPAA, SOX | Source: Strobes Security ↗
Date & Time: 2025-12-30T20:37:05
Palo Alto Networks is expanding its partnership with Google Cloud to integrate AI security technologies. This strategic move aims to bolster defenses against AI-driven threats and secure cloud infrastructure.
Source: Security Boulevard ↗
Spotlight Rationale: Selected due to the critical "DarkSpectre" browser extension campaign impacting 8.8M users and new research highlighting Browser AI Agents as a top risk vector.
Threat Context: DarkSpectre Browser Extension Campaigns
Platform Focus: SquareX Browser Security
SquareX specializes in securing the browser—the modern endpoint where employees spend most of their time. Their research identified that Browser AI Agents are now riskier than human employees. Their platform isolates malicious extensions and AI agents, preventing data exfiltration and drive-by downloads without hindering user productivity.
Actionable Platform Guidance: Implement SquareX policies to restrict extension installation to an allowlist and monitor AI agent behavior for unauthorized data access. Use the platform to detect and block the "DarkSpectre" and "ShadyPanda" extension signatures.
Source: Security Boulevard ↗, Lifeboat ↗
⚠️ Disclaimer: Test all detection logic in non-production environments before deployment.
1. Vendor Platform Configuration - SquareX
{
"policy_name": "Block_DarkSpectre_Extensions",
"action": "BLOCK",
"target_type": "EXTENSION",
"indicators": [
"DarkSpectre",
"ShadyPanda",
"GhostPoster"
],
"ai_agent_controls": {
"restrict_data_access": true,
"require_human_approval": true
}
}2. YARA Rule for DarkSpectre/ShadyPanda Extensions
rule DarkSpectre_Browser_Extension {
meta:
description = "Detects artifacts related to DarkSpectre/ShadyPanda browser extensions"
author = "Threat Rundown"
date = "2026-01-01"
reference = "https://lifeboat.com/blog/2025/12/darkspectre-browser-extension-campaigns-exposed-after-impacting-8-8-million-users-worldwide"
severity = "high"
tlp = "white"
strings:
$s1 = "DarkSpectre" ascii wide
$s2 = "ShadyPanda" ascii wide
$s3 = "GhostPoster" ascii wide
$s4 = "Customized" ascii wide
condition:
any of ($s*)
}3. SIEM Query — IBM API Connect Exploitation (CVE-2025-13915)
index=security sourcetype="ibm:apiconnect"
(msg="authentication failed" OR msg="bypass attempt")
OR (malware_name="Readme" OR cve_id="CVE-2025-13915")
| eval risk_score=case(
match(_raw, "CVE-2025-13915"), 100,
match(_raw, "Readme"), 90,
1==1, 25)
| where risk_score >= 50
| table _time, src_ip, dest_ip, user, risk_score, msg
| sort -_time4. PowerShell Script — Detect Malicious Extension Artifacts
$computers = "localhost", "WKSTN01", "WKSTN02"
$threats = @("DarkSpectre", "ShadyPanda", "GhostPoster")
foreach ($computer in $computers) {
if (Test-Connection -ComputerName $computer -Count 1 -Quiet) {
Write-Host "Scanning $computer for malicious extension artifacts..."
# Search common browser extension directories for threat names in filenames or contents
$paths = @("C:\Users\*\AppData\Local\Google\Chrome\User Data\Default\Extensions")
foreach ($path in $paths) {
if (Test-Path $path) {
Get-ChildItem -Path $path -Recurse -ErrorAction SilentlyContinue |
Select-String -Pattern $threats -SimpleMatch |
ForEach-Object {
Write-Warning "Threat detected on $computer: $($_.Line)"
}
}
}
}
}This rundown should provide a solid overview of the current threat landscape. Thank you to all our cyberheroes for your diligence and hard work. Stay vigilant!
We use essential cookies to provide our cybersecurity newsletter service and analytics cookies to improve your experience. We respect your privacy and comply with GDPR requirements.
About STIX 2.1: Structured Threat Information eXpression (STIX) is the machine language of cybersecurity. This bundle contains validated threat objects, indicators, and relationships that can be directly imported into your SIEM, TIP, or security orchestration platform.
Usage: Download or copy the JSON below and import it directly into your threat intelligence platform, SIEM, or security orchestration tools for automated threat detection and response.
{
"type": "bundle",
"id": "bundle--38880716-fb5e-4dd0-bcc1-b4c11d40200d",
"objects": [
{
"type": "marking-definition",
"spec_version": "2.1",
"id": "marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"created": "2022-10-01T00:00:00.000Z",
"definition_type": "tlp:2.0",
"name": "TLP:CLEAR",
"definition": {
"tlp": "clear"
}
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--9e936072-663b-4414-8b3c-fdbc56f8aeca",
"created": "2026-01-01T14:40:10.598Z",
"modified": "2026-01-01T14:40:10.598Z",
"name": "MikeGPT Intelligence Platform",
"description": "AI-powered threat intelligence collection and analysis platform providing automated cybersecurity intelligence feeds",
"identity_class": "organization",
"sectors": [
"technology",
"defense"
],
"contact_information": "Website: https://mikegptai.com | Email: intel@mikegptai.com",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"type": "report",
"spec_version": "2.1",
"id": "report--f2fd7f08-eac5-49b7-a99e-6effd15413ee",
"created": "2026-01-01T14:40:10.598Z",
"modified": "2026-01-01T14:40:10.598Z",
"name": "Threat Intelligence Report - 2026-01-01",
"description": "Threat Intelligence Report - 2026-01-01\n\nThis report consolidates actionable cybersecurity intelligence from 74 sources, processed through automated threat analysis and relationship extraction.\n\nKEY FINDINGS:\n• Best of 2025: Google Gemini AI Flaw Could Lead to Gmail Compromise, Phishing (Score: 100)\n• DarkSpectre Browser Extension Campaigns Exposed After Impacting 8.8 Million Users Worldwide (Score: 100)\n• Critical CVSS 9.8 Flaw Found in IBM API Connect Authentication System (Score: 100)\n• Microsoft Makes Teams ‘Secure by Default’ Starting January 2026 (Score: 100)\n• DarkSpectre Browser Extension Campaigns Exposed After Impacting 8.8 Million Users Worldwide (Score: 100)\n\nEXTRACTED ENTITIES:\n• 28 Attack Pattern(s)\n• 3 Domain Name(s)\n• 12 File:Hashes.Md5(s)\n• 8 File:Hashes.Sha 1(s)\n• 3 Indicator(s)\n• 2 Malware(s)\n• 1 Marking Definition(s)\n• 94 Relationship(s)\n• 2 Threat Actor(s)\n• 7 Tool(s)\n• 7 Vulnerability(s)\n\nCONFIDENCE ASSESSMENT:\nVariable confidence scoring applied based on entity type and intelligence source reliability. Confidence ranges from 30-95% reflecting professional intelligence assessment practices.\n\nGENERATION METADATA:\n- Processing Time: Automated\n- Validation: Three-LLM consensus committee\n- Standards Compliance: STIX 2.1\n",
"published": "2026-01-01T14:40:10.598Z",
"object_refs": [
"identity--9e936072-663b-4414-8b3c-fdbc56f8aeca",
"identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"tool--eb33f5b9-a211-409d-ba91-a9b0d6b0f75e",
"tool--65ccf4fb-0919-4be6-9835-b712b1f056a5",
"vulnerability--f2c42dbe-e16d-4283-9151-c7c085f96cb9",
"identity--ae4d5f46-29c5-40ae-842b-378abf057c12",
"malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"vulnerability--d95868d7-4f07-4d84-b742-07ee4cf4adbf",
"vulnerability--09cfd756-732a-426d-8c11-8d9ddb3e9e05",
"identity--ab826ff5-7115-490c-b135-f14a8800c4b8",
"identity--5ffaaae0-c3a4-49bb-bb57-38e94dbe7c19",
"identity--dc1263f3-2308-479e-be5c-f6e47388fa29",
"vulnerability--81f0316c-e636-4b2b-99fc-5628dfe2c6dc",
"tool--5710c74e-0f15-469a-802b-435fad89ebe9",
"identity--ab072da6-79f6-4bb8-b1b2-84174a100596",
"identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"identity--e7aaa346-3c47-410b-b7ac-2f53a69389c5",
"identity--a1d5fbd8-8b8c-4153-b138-39173f8f9967",
"identity--4a0ea356-910b-4135-8390-c178705bb54c",
"vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"identity--3cf91ae9-0a36-4c4f-aad7-9717e2e1a2cd",
"vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"identity--5653d5fd-3625-41d2-b03e-b4bf2db2b5f8",
"identity--852f1ded-54a0-4678-8751-1aa05a63754e",
"tool--110bd33b-429b-4d56-bc0c-d65f82c89552",
"malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"threat-actor--eb542bb6-573d-4d93-81f9-21ecb17ff423",
"tool--c34a5a3d-44b4-445d-9d85-478167123542",
"tool--f2491320-0c6c-4b71-a50a-d287256ea95f",
"tool--8e24b090-d2a0-4230-bfaa-0323e11c3a83",
"identity--562e37e9-4a8b-4e03-bfb5-df3d48cdbac2",
"identity--98222075-ec71-475e-bc0b-49ede8b269bb",
"identity--61a250a2-ce41-4374-91c5-a69b7cd42103",
"identity--32a7e68a-7e04-4104-8158-4e983c6f71a4",
"attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"attack-pattern--88428b3c-f02f-45b8-a38a-0541b2287509",
"attack-pattern--0ec57ff0-0257-4287-888c-8f20c7e08c6b",
"attack-pattern--8dd2a740-fa1b-4f41-be82-018bed51553e",
"attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"relationship--09a90427-70fc-4466-8e53-08bc50f37681",
"relationship--1c125169-f15a-49e5-8f32-15157d5abd65",
"relationship--f9218aff-5ff7-483b-b505-2eaccbbf12d9",
"relationship--26f2f280-4adb-4005-b54f-bd2f77e64323",
"relationship--b6931527-04d0-4a3b-9121-271e194c573d",
"relationship--d401b032-d772-4562-b675-e0a9fefbf65e",
"relationship--c0518b3c-412a-4f64-8b64-004742beb826",
"relationship--2f4f00ae-7954-40c5-8613-7ee1bb691a38",
"relationship--5a2dc473-5429-4b46-b82c-006be4ef031d",
"relationship--73fd3e69-f1eb-4bf9-92c5-4220272c1b6e",
"relationship--22bea30e-6507-474c-baec-32993acb0d94",
"relationship--7c6af7b7-0e4b-42f0-9a83-9f27b111e15e",
"relationship--104fda2e-cb05-4755-9a6e-274e3bdc4b6b",
"relationship--be8a1fd9-6d8d-4a78-b737-ac76219c7fda",
"relationship--fb5fc1fd-8da3-421d-9792-f84bd253dca2",
"relationship--d826394b-9c02-4c20-9443-dd6593692229",
"relationship--ba10c50f-d03d-4996-b750-5d755990173b",
"relationship--ab60023f-12d9-4186-9426-1fd6ac500967",
"relationship--5d03b8ef-65f5-440d-82fa-c779e07cfd33",
"relationship--b29bda0e-740b-4372-a017-2619bc370d19",
"relationship--4affef98-2dff-43ea-8004-f69ba02ae154",
"relationship--0552daff-d21e-4449-b056-b8b93e0d0a11",
"relationship--eac001b7-4e67-4050-afbc-9dab240c885c",
"relationship--64853f7c-da09-4102-aff8-ba995efb7286",
"relationship--d29075ff-badd-4378-9581-bfe62e627ccf",
"relationship--f453a0ed-8f7d-4b4d-9d1b-627185d219f0",
"relationship--11bf4062-20c5-4c30-afac-ac8b45c4e366",
"relationship--c4028f39-385a-4d8a-abe5-2f86b19b2331",
"relationship--67808a2b-2c4a-46d7-83ab-791c306b5fae",
"relationship--1d6aab90-b19f-401f-a2c7-4b4b68a0804c",
"relationship--d7b97179-0d35-4b76-9421-c5cd044455be",
"relationship--dbec9500-741d-4efa-af7c-4bd9578098ba",
"relationship--dcf7fb97-db7f-4826-94c8-a4f15637e14c",
"relationship--7a32d866-bcd9-4e2a-abff-7aa193beac2d",
"relationship--7750eb41-2d61-4a2a-8e5b-d3a2284c0980",
"relationship--1f9b75e9-c77d-474e-b850-80a024ff1c72",
"relationship--4b0deb7d-18a1-4833-b219-62ef17b34435",
"relationship--49d61365-2837-4975-835a-bc060a251ec9",
"relationship--07e0492d-3926-49d4-9f52-df4f42d521c3",
"relationship--41209e8f-957b-4980-a160-ee849fdbb74d",
"relationship--a53d531f-7303-4b20-ab7b-c46005933ef6",
"relationship--0515258c-f967-4179-9ca5-cf5dcbc74e55",
"relationship--fe8d0628-d8e4-44d9-945e-e09935211b9f",
"relationship--f69c10d1-0d61-40ff-9226-113a19691ec7",
"relationship--e962d504-c825-4aec-9949-03fd98707402",
"relationship--4b335dce-1185-4167-804e-3c07a7c58f55",
"relationship--b154ecf5-8ad3-4674-82e9-14874becc334",
"relationship--1ebfe5cc-ac00-4846-b6f5-06f50de4d6eb",
"relationship--b09966ab-fbd1-46ee-b437-77b4d4d37522",
"relationship--3be54220-1d64-4a20-aa03-299817e01ac7",
"relationship--e5e5bc55-7e7e-4eee-bf69-e8cb3fb35480",
"relationship--c8ad4a0a-0210-40ad-ad7e-2b5c03f6457f",
"relationship--16f55279-1397-488f-b413-5dbbcc00a3e1",
"relationship--607aa57f-a233-481e-bacf-952de747b362",
"relationship--cab6fdf0-5b45-4754-a9c8-99009db45a0b",
"relationship--ecc7e5e9-1020-4dee-8f02-5ff4874b53f6",
"relationship--cfefef30-93f6-490d-b243-6e77f66df296",
"relationship--73904bb3-9224-4450-bbeb-0aba137cd243",
"relationship--009fee0d-ea7f-42db-b7b4-37ee59727c5d",
"relationship--b17fe67e-c639-49a9-9cb0-f33f293e13fa",
"relationship--975cb493-057f-46bf-9860-8db0ffd4526e",
"relationship--5a0a1b3e-d163-40a0-beb2-9aabed3b005a",
"relationship--2422f319-a2b1-4399-b376-bcee214d8c77",
"relationship--be0f3706-69bf-41cf-95b8-f032d2591736",
"relationship--c58da3ea-5dff-4a02-b29c-a5584c09d812",
"relationship--703e519a-e2b8-42e0-9cdd-ef752d1c0df1",
"relationship--5029b6c4-6b8c-4a02-9bf5-6054517feec7",
"relationship--fa0dccc0-07c4-4e22-95ec-75c88bf82174",
"relationship--a10cada5-7083-4e11-9e20-4fea815dcb11",
"relationship--8f68f003-4e14-40d2-8beb-7948a81d4fda",
"relationship--33c79a25-bb27-4f12-af01-fea08f5b5c80",
"relationship--be0d2e7b-5251-4926-adf9-5de374be32c7",
"relationship--11139382-1d72-4e01-9c3b-6790e8ebee5b",
"relationship--2a065ab8-01cb-4dc3-93e5-6b580a1a8bde",
"relationship--d969410c-e1aa-4334-bd9b-6fe28e621c91",
"relationship--1635352e-860c-45cb-8374-79016ed2e4d1",
"relationship--85f8f017-06eb-4217-bcd7-8e7f75188e94",
"relationship--a6532b81-931e-46cf-920d-95cc9fd55533",
"relationship--3c2e627b-a97a-4e7a-afe1-427954736134",
"relationship--91986d4e-f0da-4ed3-bee9-dc8606d76c82",
"relationship--2abd5839-155a-4140-957a-31a0f9f16b08",
"relationship--6dbdf932-9329-4013-9a41-3f9f4aa67456",
"relationship--22703260-6858-4c04-aa8c-8f72021ebd07",
"relationship--613d5935-1979-4bda-82e1-e5a22b0570d4",
"relationship--9ff34725-2361-448d-85ac-426ae9b0e5bb",
"relationship--71b30f3f-ad0f-4986-94fa-b339fa61ffcf",
"relationship--ea540849-1c0c-4317-93c8-494ecef4592f",
"relationship--bf7a4394-a187-4088-8d11-b22b280129c7",
"relationship--1d0ef4fa-ca9f-4d89-a1a3-07889a1dd818",
"relationship--3f822c4a-e607-49a7-873e-28962fb5e6b0",
"relationship--234b9eb5-02c1-4762-89ff-8638f6a55985",
"file:hashes.MD5--e5cac07a-dd1a-4434-87cc-cedaefefb3f2",
"file:hashes.MD5--04115bc3-9956-4a99-b71f-a21b8d09e7be",
"file:hashes.MD5--6cc296ab-daf2-4c14-9b92-c3e47478e5dc",
"file:hashes.MD5--0637a6e3-dcdd-4651-97e1-2c9f9faf0724",
"file:hashes.MD5--b1869241-214a-4d21-a891-6d899fa41129",
"file:hashes.MD5--d5cfce9c-d8bc-47dc-a17a-cf3a4b1e7fb5",
"file:hashes.MD5--b5799aa6-9180-4cfe-aa25-14549b924c1d",
"file:hashes.MD5--ccdee563-3e34-4fbe-bb3a-f7acc80604f2",
"file:hashes.MD5--20ce9ee2-990d-4574-a663-d0d7eebeb947",
"file:hashes.MD5--bb387ed4-335b-40f2-92db-a63953e7ac0b",
"file:hashes.MD5--95b7150e-8fe6-42b3-9a6c-40507bd8a2c0",
"file:hashes.MD5--855eed71-51dd-40ca-8847-96aab1520d51",
"file:hashes.SHA-1--f5ea65dd-02e4-4956-8210-97e8155dd999",
"file:hashes.SHA-1--2ab8ba63-0186-4aa5-a394-279c8903cfaa",
"file:hashes.SHA-1--7099aa9d-92fe-47c7-8c44-64b6b3e14f0e",
"file:hashes.SHA-1--42539da2-7fea-4eda-8080-85eb681f2b58",
"file:hashes.SHA-1--20fbbe42-37c5-49e0-ac70-ad699d493e9b",
"file:hashes.SHA-1--debac52a-27b1-4f83-8f77-bc8a161cbb1b",
"file:hashes.SHA-1--f5d550f5-07b4-4045-9f63-a6da61d79fca",
"file:hashes.SHA-1--174abab6-0965-4209-af9e-9de5761805e6",
"domain-name--2b349432-a454-4043-9b5c-83ca7ead2ad5",
"domain-name--d3c35010-338f-4085-8c75-abac163b2ebd",
"domain-name--9761b8ae-0967-489c-ad1f-852893085ac7",
"indicator--e953cb7f-a3e6-43ea-a9bc-8cbdc22831f8",
"relationship--22f50398-07ee-403a-b861-6253c575c6fe",
"indicator--f023d728-6ffc-4254-af30-028e5e8d4e7a",
"relationship--6dc5f652-4a70-456f-be20-9c0e61b62f16",
"indicator--d8a3958d-0d66-4ff5-8bb7-09efbc930888",
"relationship--608b286c-51ec-49b1-a296-122d54587e9d"
],
"labels": [
"threat-report",
"threat-intelligence"
],
"created_by_ref": "identity--9e936072-663b-4414-8b3c-fdbc56f8aeca",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.680Z",
"modified": "2026-01-01T14:40:09.680Z",
"confidence": 95,
"type": "identity",
"id": "identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"name": "Google",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Google is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.680Z",
"modified": "2026-01-01T14:40:09.680Z",
"confidence": 95,
"type": "threat-actor",
"id": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"name": "ShadyPanda",
"threat_actor_types": [
"hacker"
],
"labels": [
"threat-actor"
],
"description": "ShadyPanda is a threat group that has been operating for at least seven years, using a unique approach to compromise targets. They publish or acquire harmless extensions, allowing them to establish a foothold and gather intelligence before striking. This group's tactics demonstrate a high level of sophistication and patience, making them a significant threat to organizations. Their ability to blend in and avoid detection for extended periods makes them a challenging adversary to detect and mitigate.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.680Z",
"modified": "2026-01-01T14:40:09.680Z",
"confidence": 95,
"type": "tool",
"id": "tool--eb33f5b9-a211-409d-ba91-a9b0d6b0f75e",
"name": "Google Chrome",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A popular web browser developed by Google.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.680Z",
"modified": "2026-01-01T14:40:09.680Z",
"confidence": 95,
"type": "tool",
"id": "tool--65ccf4fb-0919-4be6-9835-b712b1f056a5",
"name": "API Connect",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Software with a known vulnerability",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.680Z",
"modified": "2026-01-01T14:40:09.680Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--f2c42dbe-e16d-4283-9151-c7c085f96cb9",
"name": "CVE-2025-13915",
"description": "IBM API Connect 10.0.8.0 through 10.0.8.5, and 10.0.11.0 could allow a remote attacker to bypass authentication mechanisms and gain unauthorized access to the application.. CVSS Score: 9.8 (CRITICAL). EPSS: 0.4% exploitation probability",
"x_cvss_score": 9.8,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.00373,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-13915",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-13915"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-13915",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-13915"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.680Z",
"modified": "2026-01-01T14:40:09.680Z",
"confidence": 95,
"type": "identity",
"id": "identity--ae4d5f46-29c5-40ae-842b-378abf057c12",
"name": "Microsoft",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Microsoft is a multinational technology company that develops, manufactures, licenses, and supports a wide range of software products, services, and devices.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.680Z",
"modified": "2026-01-01T14:40:09.680Z",
"confidence": 95,
"type": "malware",
"id": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"name": "RondoDox",
"is_family": true,
"malware_types": [
"bot"
],
"labels": [
"malicious-activity"
],
"description": "A botnet exploiting a vulnerability",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--d95868d7-4f07-4d84-b742-07ee4cf4adbf",
"name": "React2Shell",
"description": "React2Shell is a vulnerability in React Server Components that could lead to denial-of-service attacks or the exposure of source code. It is one of several recently discovered flaws in React Server Components, including CVE-2025-55183, CVE-2025-55184, and CVE-2025-67779. React2Shell is considered a dangerous vulnerability that requires immediate attention from security teams to prevent exploitation by threat actors.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--09cfd756-732a-426d-8c11-8d9ddb3e9e05",
"name": "CVE-2025-55182",
"description": "A pre-authentication remote code execution vulnerability exists in React Server Components versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0 including the following packages: react-server-dom-parcel, react-server-dom-turbopack, and react-server-dom-webpack. The vulnerable code unsafely deserializes payloads from HTTP requests to Server Function endpoints.. CVSS Score: 10.0 (CRITICAL). CISA KEV: Active exploitation confirmed. EPSS: 47.4% exploitation probability",
"x_cvss_score": 10.0,
"x_cvss_severity": "CRITICAL",
"x_kev_status": true,
"x_epss_score": 0.47368,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-55182",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-55182"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-55182",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-55182"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--ab826ff5-7115-490c-b135-f14a8800c4b8",
"name": "Palo Alto",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Palo Alto is a cybersecurity company.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--5ffaaae0-c3a4-49bb-bb57-38e94dbe7c19",
"name": "SquareX",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A company researching cybersecurity",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--dc1263f3-2308-479e-be5c-f6e47388fa29",
"name": "Singapore",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A country with a Cyber Security Agency",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--81f0316c-e636-4b2b-99fc-5628dfe2c6dc",
"name": "CVE-2025-52691",
"description": "Successful exploitation of the vulnerability could allow an unauthenticated attacker to upload arbitrary files to any location on the mail server, potentially enabling remote code execution.. CVSS Score: 10.0 (CRITICAL). EPSS: 0.2% exploitation probability",
"x_cvss_score": 10.0,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.00177,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-52691",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-52691"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-52691",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-52691"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "tool",
"id": "tool--5710c74e-0f15-469a-802b-435fad89ebe9",
"name": "SmarterMail",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Email server software with a known vulnerability",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--ab072da6-79f6-4bb8-b1b2-84174a100596",
"name": "Cyber Security Agency",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A government agency responsible for cybersecurity",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"name": "Non-Human Identities",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--e7aaa346-3c47-410b-b7ac-2f53a69389c5",
"name": "Strobes Security",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A company providing cybersecurity services",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--a1d5fbd8-8b8c-4153-b138-39173f8f9967",
"name": "Sygnia",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A company providing cybersecurity services",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--4a0ea356-910b-4135-8390-c178705bb54c",
"name": "LinkedIn",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "LinkedIn is a social networking platform designed for professionals and businesses to connect and share information. As a major online platform, LinkedIn's data is a valuable target for threat actors seeking to exploit professional networks for social engineering attacks. The exposure of 4.3 billion professional records, including LinkedIn data, poses a significant risk to individuals and organizations, enabling large-scale AI-driven social engineering attacks.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 92,
"type": "vulnerability",
"id": "vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"name": "SecurityWeek",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"name": "China",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "China is a country.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--3cf91ae9-0a36-4c4f-aad7-9717e2e1a2cd",
"name": "Condé Nast",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A global media company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"name": "MongoBleed",
"description": "An event where data is accessed without authorization.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"name": "CVE-2025-14847",
"description": "Mismatched length fields in Zlib compressed protocol headers may allow a read of uninitialized heap memory by an unauthenticated client. This issue affects all MongoDB Server v7.0 prior to 7.0.28 versions, MongoDB Server v8.0 versions prior to 8.0.17, MongoDB Server v8.2 versions prior to 8.2.3, MongoDB Server v6.0 versions prior to 6.0.27, MongoDB Server v5.0 versions prior to 5.0.32, MongoDB Server v4.4 versions prior to 4.4.30, MongoDB Server v4.2 versions greater than or equal to 4.2.0, Mong. CVSS Score: 7.5 (HIGH). CISA KEV: Active exploitation confirmed. EPSS: 68.7% exploitation probability",
"x_cvss_score": 7.5,
"x_cvss_severity": "HIGH",
"x_kev_status": true,
"x_epss_score": 0.68682,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-14847",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-14847"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-14847",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-14847"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--5653d5fd-3625-41d2-b03e-b4bf2db2b5f8",
"name": "Amazon",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Amazon is a multinational technology company that focuses on e-commerce, cloud computing, digital streaming, and artificial intelligence.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--852f1ded-54a0-4678-8751-1aa05a63754e",
"name": "Gmail",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Email service",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "tool",
"id": "tool--110bd33b-429b-4d56-bc0c-d65f82c89552",
"name": "Google Gemini AI",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "AI chatbot",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "malware",
"id": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"name": "GhostPoster",
"is_family": true,
"malware_types": [
"trojan"
],
"labels": [
"malicious-activity"
],
"description": "Malicious browser extension",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "threat-actor",
"id": "threat-actor--eb542bb6-573d-4d93-81f9-21ecb17ff423",
"name": "DarkSpectre",
"threat_actor_types": [
"hacker"
],
"labels": [
"threat-actor"
],
"description": "Malicious campaign",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "tool",
"id": "tool--c34a5a3d-44b4-445d-9d85-478167123542",
"name": "Microsoft Edge",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Web browser",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "tool",
"id": "tool--f2491320-0c6c-4b71-a50a-d287256ea95f",
"name": "Mozilla Firefox",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Web browser",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "tool",
"id": "tool--8e24b090-d2a0-4230-bfaa-0323e11c3a83",
"name": "Teams",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Communication platform",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--562e37e9-4a8b-4e03-bfb5-df3d48cdbac2",
"name": "TechRepublic",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Technology news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--98222075-ec71-475e-bc0b-49ede8b269bb",
"name": "Zhongming Wang",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Person's name",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.681Z",
"modified": "2026-01-01T14:40:09.681Z",
"confidence": 95,
"type": "identity",
"id": "identity--61a250a2-ce41-4374-91c5-a69b7cd42103",
"name": "Chongqing University",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "University",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.682Z",
"modified": "2026-01-01T14:40:09.682Z",
"confidence": 95,
"type": "identity",
"id": "identity--32a7e68a-7e04-4104-8158-4e983c6f71a4",
"name": "Tao Xiang",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Person's name",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:09.682Z",
"modified": "2026-01-01T14:40:09.682Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"name": "Spearphishing Attachment",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/001/",
"external_id": "T1566.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.592Z",
"modified": "2026-01-01T14:40:10.592Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"name": "Spearphishing Link",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/002/",
"external_id": "T1566.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.592Z",
"modified": "2026-01-01T14:40:10.592Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"name": "Spearphishing via Service",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/003/",
"external_id": "T1566.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.592Z",
"modified": "2026-01-01T14:40:10.592Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"name": "Remote Services",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "lateral-movement"
}
],
"x_mitre_id": "T1021",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1021/",
"external_id": "T1021"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.592Z",
"modified": "2026-01-01T14:40:10.592Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"name": "Exploit Public-Facing Application",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1190",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1190/",
"external_id": "T1190"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.592Z",
"modified": "2026-01-01T14:40:10.592Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"name": "Exploitation for Client Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1203",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1203/",
"external_id": "T1203"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.592Z",
"modified": "2026-01-01T14:40:10.592Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"name": "Command and Scripting Interpreter",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/",
"external_id": "T1059"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.592Z",
"modified": "2026-01-01T14:40:10.592Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"name": "Modify Registry",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1112",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1112/",
"external_id": "T1112"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"name": "Registry Run Keys / Startup Folder",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/001/",
"external_id": "T1547.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"name": "Create or Modify System Process",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1543",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1543/",
"external_id": "T1543"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"name": "Boot or Logon Autostart Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/",
"external_id": "T1547"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"name": "Supply Chain Compromise",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1195",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1195/",
"external_id": "T1195"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"name": "Abuse Elevation Control Mechanism",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1548",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1548/",
"external_id": "T1548"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"name": "Access Token Manipulation",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1134",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1134/",
"external_id": "T1134"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--88428b3c-f02f-45b8-a38a-0541b2287509",
"name": "LSA Secrets",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
}
],
"x_mitre_id": "T1003.004",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1003/004/",
"external_id": "T1003.004"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--0ec57ff0-0257-4287-888c-8f20c7e08c6b",
"name": "Cloud Secrets Management Stores",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
}
],
"x_mitre_id": "T1555.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1555/006/",
"external_id": "T1555.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 78,
"type": "attack-pattern",
"id": "attack-pattern--8dd2a740-fa1b-4f41-be82-018bed51553e",
"name": "Safe Mode Boot",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1562.009",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1562/009/",
"external_id": "T1562.009"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"name": "Spearphishing Voice",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "reconnaissance"
}
],
"x_mitre_id": "T1598.004",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1598/004/",
"external_id": "T1598.004"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"name": "Browser Extensions",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1176.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1176/001/",
"external_id": "T1176.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"name": "Scheduled Task",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1053.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1053/005/",
"external_id": "T1053.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"name": "Socket Filters",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1205.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1205/002/",
"external_id": "T1205.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"name": "Boot or Logon Initialization Scripts",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1037",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1037/",
"external_id": "T1037"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"name": "Archive via Utility",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1560.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1560/001/",
"external_id": "T1560.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"name": "Screen Capture",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1113",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1113/",
"external_id": "T1113"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"name": "Adversary-in-the-Middle",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/",
"external_id": "T1557"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 69,
"type": "attack-pattern",
"id": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"name": "Botnet",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1584.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1584/005/",
"external_id": "T1584.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 66,
"type": "attack-pattern",
"id": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"name": "Artificial Intelligence",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.007",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/007/",
"external_id": "T1588.007"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2026-01-01T14:40:10.593Z",
"modified": "2026-01-01T14:40:10.593Z",
"confidence": 66,
"type": "attack-pattern",
"id": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"name": "Vulnerabilities",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/006/",
"external_id": "T1588.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--09a90427-70fc-4466-8e53-08bc50f37681",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "targets",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "threat-actor--eb542bb6-573d-4d93-81f9-21ecb17ff423",
"confidence": 85,
"description": "[ARTICLE_BOUNDARY]\n\nThe threat actor behind two malicious browser extension campaigns, ShadyPanda and GhostPoster , has been attributed to a third attack campaign codenamed DarkSpectre that has impacted 2.2 million users of Google Chrome, Microsoft Edge, and Mozilla Firefox.",
"x_validation_method": "three-llm-consensus"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1c125169-f15a-49e5-8f32-15157d5abd65",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "targets",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "threat-actor--eb542bb6-573d-4d93-81f9-21ecb17ff423",
"confidence": 85,
"description": "[ARTICLE_BOUNDARY]\n\nThe threat actor behind two malicious browser extension campaigns, ShadyPanda and GhostPoster , has been attributed to a third attack campaign codenamed DarkSpectre that has impacted 2.2 million users of Google Chrome, Microsoft Edge, and Mozilla Firefox.",
"x_validation_method": "three-llm-consensus"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--f9218aff-5ff7-483b-b505-2eaccbbf12d9",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "tool--f2491320-0c6c-4b71-a50a-d287256ea95f",
"confidence": 85,
"description": "[ARTICLE_BOUNDARY]\n\nThe threat actor behind two malicious browser extension campaigns, ShadyPanda and GhostPoster , has been attributed to a third attack campaign codenamed DarkSpectre that has impacted 2.2 million users of Google Chrome, Microsoft Edge, and Mozilla Firefox.",
"x_validation_method": "three-llm-consensus"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--26f2f280-4adb-4005-b54f-bd2f77e64323",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"confidence": 85,
"description": "Co-occurrence in intelligence context",
"x_validation_method": "three-llm-consensus"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b6931527-04d0-4a3b-9121-271e194c573d",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Spearphishing Attachment (T1566.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d401b032-d772-4562-b675-e0a9fefbf65e",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Spearphishing Link (T1566.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c0518b3c-412a-4f64-8b64-004742beb826",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Spearphishing via Service (T1566.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2f4f00ae-7954-40c5-8613-7ee1bb691a38",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Remote Services (T1021) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5a2dc473-5429-4b46-b82c-006be4ef031d",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Exploit Public-Facing Application (T1190) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--73fd3e69-f1eb-4bf9-92c5-4220272c1b6e",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Exploitation for Client Execution (T1203) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--22bea30e-6507-474c-baec-32993acb0d94",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Command and Scripting Interpreter (T1059) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--7c6af7b7-0e4b-42f0-9a83-9f27b111e15e",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Modify Registry (T1112) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--104fda2e-cb05-4755-9a6e-274e3bdc4b6b",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Registry Run Keys / Startup Folder (T1547.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--be8a1fd9-6d8d-4a78-b737-ac76219c7fda",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Create or Modify System Process (T1543) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--fb5fc1fd-8da3-421d-9792-f84bd253dca2",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Boot or Logon Autostart Execution (T1547) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d826394b-9c02-4c20-9443-dd6593692229",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Supply Chain Compromise (T1195) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ba10c50f-d03d-4996-b750-5d755990173b",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Abuse Elevation Control Mechanism (T1548) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ab60023f-12d9-4186-9426-1fd6ac500967",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Access Token Manipulation (T1134) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5d03b8ef-65f5-440d-82fa-c779e07cfd33",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--88428b3c-f02f-45b8-a38a-0541b2287509",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and LSA Secrets (T1003.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b29bda0e-740b-4372-a017-2619bc370d19",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--0ec57ff0-0257-4287-888c-8f20c7e08c6b",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Cloud Secrets Management Stores (T1555.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4affef98-2dff-43ea-8004-f69ba02ae154",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--8dd2a740-fa1b-4f41-be82-018bed51553e",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Safe Mode Boot (T1562.009) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--0552daff-d21e-4449-b056-b8b93e0d0a11",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Spearphishing Voice (T1598.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--eac001b7-4e67-4050-afbc-9dab240c885c",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Browser Extensions (T1176.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--64853f7c-da09-4102-aff8-ba995efb7286",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Scheduled Task (T1053.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d29075ff-badd-4378-9581-bfe62e627ccf",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Socket Filters (T1205.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--f453a0ed-8f7d-4b4d-9d1b-627185d219f0",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Boot or Logon Initialization Scripts (T1037) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--11bf4062-20c5-4c30-afac-ac8b45c4e366",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Archive via Utility (T1560.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c4028f39-385a-4d8a-abe5-2f86b19b2331",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Screen Capture (T1113) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--67808a2b-2c4a-46d7-83ab-791c306b5fae",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Adversary-in-the-Middle (T1557) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1d6aab90-b19f-401f-a2c7-4b4b68a0804c",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Botnet (T1584.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d7b97179-0d35-4b76-9421-c5cd044455be",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Spearphishing Voice (T1566.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--dbec9500-741d-4efa-af7c-4bd9578098ba",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Artificial Intelligence (T1588.007) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--dcf7fb97-db7f-4826-94c8-a4f15637e14c",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "threat-actor--ed70a1ea-0748-4318-9623-4105653cb15f",
"target_ref": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"confidence": 60,
"description": "Co-occurrence: ShadyPanda and Vulnerabilities (T1588.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--7a32d866-bcd9-4e2a-abff-7aa193beac2d",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Attachment (T1566.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--7750eb41-2d61-4a2a-8e5b-d3a2284c0980",
"created": "2026-01-01T14:40:10.594Z",
"modified": "2026-01-01T14:40:10.594Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Link (T1566.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1f9b75e9-c77d-474e-b850-80a024ff1c72",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing via Service (T1566.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4b0deb7d-18a1-4833-b219-62ef17b34435",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Remote Services (T1021) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--49d61365-2837-4975-835a-bc060a251ec9",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Exploit Public-Facing Application (T1190) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--07e0492d-3926-49d4-9f52-df4f42d521c3",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Exploitation for Client Execution (T1203) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--41209e8f-957b-4980-a160-ee849fdbb74d",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Command and Scripting Interpreter (T1059) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a53d531f-7303-4b20-ab7b-c46005933ef6",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Modify Registry (T1112) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--0515258c-f967-4179-9ca5-cf5dcbc74e55",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Registry Run Keys / Startup Folder (T1547.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--fe8d0628-d8e4-44d9-945e-e09935211b9f",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Create or Modify System Process (T1543) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--f69c10d1-0d61-40ff-9226-113a19691ec7",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Boot or Logon Autostart Execution (T1547) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e962d504-c825-4aec-9949-03fd98707402",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Supply Chain Compromise (T1195) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4b335dce-1185-4167-804e-3c07a7c58f55",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Abuse Elevation Control Mechanism (T1548) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b154ecf5-8ad3-4674-82e9-14874becc334",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Access Token Manipulation (T1134) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1ebfe5cc-ac00-4846-b6f5-06f50de4d6eb",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--88428b3c-f02f-45b8-a38a-0541b2287509",
"confidence": 55,
"description": "Co-occurrence: RondoDox and LSA Secrets (T1003.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b09966ab-fbd1-46ee-b437-77b4d4d37522",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--0ec57ff0-0257-4287-888c-8f20c7e08c6b",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Cloud Secrets Management Stores (T1555.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3be54220-1d64-4a20-aa03-299817e01ac7",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--8dd2a740-fa1b-4f41-be82-018bed51553e",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Safe Mode Boot (T1562.009) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e5e5bc55-7e7e-4eee-bf69-e8cb3fb35480",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Voice (T1598.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c8ad4a0a-0210-40ad-ad7e-2b5c03f6457f",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Browser Extensions (T1176.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--16f55279-1397-488f-b413-5dbbcc00a3e1",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Scheduled Task (T1053.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--607aa57f-a233-481e-bacf-952de747b362",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Socket Filters (T1205.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--cab6fdf0-5b45-4754-a9c8-99009db45a0b",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Boot or Logon Initialization Scripts (T1037) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ecc7e5e9-1020-4dee-8f02-5ff4874b53f6",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Archive via Utility (T1560.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--cfefef30-93f6-490d-b243-6e77f66df296",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Screen Capture (T1113) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--73904bb3-9224-4450-bbeb-0aba137cd243",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Adversary-in-the-Middle (T1557) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--009fee0d-ea7f-42db-b7b4-37ee59727c5d",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Botnet (T1584.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b17fe67e-c639-49a9-9cb0-f33f293e13fa",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Voice (T1566.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--975cb493-057f-46bf-9860-8db0ffd4526e",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Artificial Intelligence (T1588.007) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5a0a1b3e-d163-40a0-beb2-9aabed3b005a",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Vulnerabilities (T1588.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2422f319-a2b1-4399-b376-bcee214d8c77",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Spearphishing Attachment (T1566.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--be0f3706-69bf-41cf-95b8-f032d2591736",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Spearphishing Link (T1566.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c58da3ea-5dff-4a02-b29c-a5584c09d812",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Spearphishing via Service (T1566.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--703e519a-e2b8-42e0-9cdd-ef752d1c0df1",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Remote Services (T1021) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5029b6c4-6b8c-4a02-9bf5-6054517feec7",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Exploit Public-Facing Application (T1190) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--fa0dccc0-07c4-4e22-95ec-75c88bf82174",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Exploitation for Client Execution (T1203) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a10cada5-7083-4e11-9e20-4fea815dcb11",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Command and Scripting Interpreter (T1059) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--8f68f003-4e14-40d2-8beb-7948a81d4fda",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Modify Registry (T1112) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--33c79a25-bb27-4f12-af01-fea08f5b5c80",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Registry Run Keys / Startup Folder (T1547.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--be0d2e7b-5251-4926-adf9-5de374be32c7",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Create or Modify System Process (T1543) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--11139382-1d72-4e01-9c3b-6790e8ebee5b",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Boot or Logon Autostart Execution (T1547) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2a065ab8-01cb-4dc3-93e5-6b580a1a8bde",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Supply Chain Compromise (T1195) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d969410c-e1aa-4334-bd9b-6fe28e621c91",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Abuse Elevation Control Mechanism (T1548) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1635352e-860c-45cb-8374-79016ed2e4d1",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Access Token Manipulation (T1134) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--85f8f017-06eb-4217-bcd7-8e7f75188e94",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--88428b3c-f02f-45b8-a38a-0541b2287509",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and LSA Secrets (T1003.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a6532b81-931e-46cf-920d-95cc9fd55533",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--0ec57ff0-0257-4287-888c-8f20c7e08c6b",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Cloud Secrets Management Stores (T1555.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3c2e627b-a97a-4e7a-afe1-427954736134",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--8dd2a740-fa1b-4f41-be82-018bed51553e",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Safe Mode Boot (T1562.009) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--91986d4e-f0da-4ed3-bee9-dc8606d76c82",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Spearphishing Voice (T1598.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2abd5839-155a-4140-957a-31a0f9f16b08",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Browser Extensions (T1176.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--6dbdf932-9329-4013-9a41-3f9f4aa67456",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Scheduled Task (T1053.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--22703260-6858-4c04-aa8c-8f72021ebd07",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Socket Filters (T1205.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--613d5935-1979-4bda-82e1-e5a22b0570d4",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Boot or Logon Initialization Scripts (T1037) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--9ff34725-2361-448d-85ac-426ae9b0e5bb",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Archive via Utility (T1560.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--71b30f3f-ad0f-4986-94fa-b339fa61ffcf",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Screen Capture (T1113) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ea540849-1c0c-4317-93c8-494ecef4592f",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Adversary-in-the-Middle (T1557) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--bf7a4394-a187-4088-8d11-b22b280129c7",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Botnet (T1584.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1d0ef4fa-ca9f-4d89-a1a3-07889a1dd818",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Spearphishing Voice (T1566.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3f822c4a-e607-49a7-873e-28962fb5e6b0",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Artificial Intelligence (T1588.007) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--234b9eb5-02c1-4762-89ff-8638f6a55985",
"created": "2026-01-01T14:40:10.595Z",
"modified": "2026-01-01T14:40:10.595Z",
"relationship_type": "uses",
"source_ref": "malware--e2aede3e-6d44-40bb-ba8a-a4c4cbf31bd1",
"target_ref": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"confidence": 55,
"description": "Co-occurrence: GhostPoster and Vulnerabilities (T1588.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "file:hashes.MD5",
"value": "210600be82239d3cc845b993ef7713e2",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--e5cac07a-dd1a-4434-87cc-cedaefefb3f2"
},
{
"type": "file:hashes.MD5",
"value": "242bc60a43eabeed6410fdb3e2428a3a",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--04115bc3-9956-4a99-b71f-a21b8d09e7be"
},
{
"type": "file:hashes.MD5",
"value": "297bec80a7bee340d10d4ea429909796",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--6cc296ab-daf2-4c14-9b92-c3e47478e5dc"
},
{
"type": "file:hashes.MD5",
"value": "3ba7a49934b2f5fdb01e5ba157a66c98",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--0637a6e3-dcdd-4651-97e1-2c9f9faf0724"
},
{
"type": "file:hashes.MD5",
"value": "50608632718649bc00ab1edf5724a9af",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--b1869241-214a-4d21-a891-6d899fa41129"
},
{
"type": "file:hashes.MD5",
"value": "6536ebe330f403aa8d574f45cb8e72cb",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--d5cfce9c-d8bc-47dc-a17a-cf3a4b1e7fb5"
},
{
"type": "file:hashes.MD5",
"value": "73a19307b88c0e9468b49ee3135be5f4",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--b5799aa6-9180-4cfe-aa25-14549b924c1d"
},
{
"type": "file:hashes.MD5",
"value": "7a0c180b3fdc7fe574aaf9f6502d8496",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--ccdee563-3e34-4fbe-bb3a-f7acc80604f2"
},
{
"type": "file:hashes.MD5",
"value": "a98f4242a2281e1f32e51f0cfed391b0",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--20ce9ee2-990d-4574-a663-d0d7eebeb947"
},
{
"type": "file:hashes.MD5",
"value": "b9719cea1bf4f95c7632975b82876f96",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--bb387ed4-335b-40f2-92db-a63953e7ac0b"
},
{
"type": "file:hashes.MD5",
"value": "c0df8197455bae7b8a6ca2e835867a6a",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--95b7150e-8fe6-42b3-9a6c-40507bd8a2c0"
},
{
"type": "file:hashes.MD5",
"value": "f022baae5f1873b46aaf2c5cc03e1e21",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--855eed71-51dd-40ca-8847-96aab1520d51"
},
{
"type": "file:hashes.SHA-1",
"value": "0287d785d44bb1cab51a6c3278a90c84de5f6a02",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--f5ea65dd-02e4-4956-8210-97e8155dd999"
},
{
"type": "file:hashes.SHA-1",
"value": "0ba9196a71259d3a2ca0b5b92dba196d82fde0fc",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--2ab8ba63-0186-4aa5-a394-279c8903cfaa"
},
{
"type": "file:hashes.SHA-1",
"value": "10a96be58694716d36b3f18835aa24dc2e964967",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--7099aa9d-92fe-47c7-8c44-64b6b3e14f0e"
},
{
"type": "file:hashes.SHA-1",
"value": "2f42087269ba4138acddbab8537c9d80c4f8bea8",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--42539da2-7fea-4eda-8080-85eb681f2b58"
},
{
"type": "file:hashes.SHA-1",
"value": "4b19500185e82a7454a046caba1c20678b2f6fad",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--20fbbe42-37c5-49e0-ac70-ad699d493e9b"
},
{
"type": "file:hashes.SHA-1",
"value": "b8f3ff1cb8c1eb350767d07e2d88e329e5ff0807",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--debac52a-27b1-4f83-8f77-bc8a161cbb1b"
},
{
"type": "file:hashes.SHA-1",
"value": "bd289ef73d5604939e6f157fba4a3f601ac22a93",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--f5d550f5-07b4-4045-9f63-a6da61d79fca"
},
{
"type": "file:hashes.SHA-1",
"value": "c1cb2cb474cd2b5b9054e1fcfb6996a9d156e49e",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--174abab6-0965-4209-af9e-9de5761805e6"
},
{
"type": "domain-name",
"value": "mitarchive.info",
"source": "OTX",
"malware_families": [
"GhostPoster"
],
"pulse_names": [
"IOC - Inside GhostPoster: How a PNG Icon Infected 50,000 Firefox Users"
],
"id": "domain-name--2b349432-a454-4043-9b5c-83ca7ead2ad5"
},
{
"type": "domain-name",
"value": "www.dealctr.com",
"source": "OTX",
"malware_families": [
"GhostPoster"
],
"pulse_names": [
"IOC - Inside GhostPoster: How a PNG Icon Infected 50,000 Firefox Users"
],
"id": "domain-name--d3c35010-338f-4085-8c75-abac163b2ebd"
},
{
"type": "domain-name",
"value": "www.liveupdt.com",
"source": "OTX",
"malware_families": [
"GhostPoster"
],
"pulse_names": [
"IOC - Inside GhostPoster: How a PNG Icon Infected 50,000 Firefox Users"
],
"id": "domain-name--9761b8ae-0967-489c-ad1f-852893085ac7"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--e953cb7f-a3e6-43ea-a9bc-8cbdc22831f8",
"created": "2026-01-01T14:39:38.323Z",
"modified": "2026-01-01T14:39:38.323Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'mitarchive.info']",
"pattern_type": "stix",
"valid_from": "2026-01-01T14:39:38.323Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--22f50398-07ee-403a-b861-6253c575c6fe",
"created": "2026-01-01T14:39:38.323Z",
"modified": "2026-01-01T14:39:38.323Z",
"relationship_type": "based-on",
"source_ref": "indicator--e953cb7f-a3e6-43ea-a9bc-8cbdc22831f8",
"target_ref": "domain-name--2b349432-a454-4043-9b5c-83ca7ead2ad5"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--f023d728-6ffc-4254-af30-028e5e8d4e7a",
"created": "2026-01-01T14:39:38.334Z",
"modified": "2026-01-01T14:39:38.334Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'www.dealctr.com']",
"pattern_type": "stix",
"valid_from": "2026-01-01T14:39:38.334Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--6dc5f652-4a70-456f-be20-9c0e61b62f16",
"created": "2026-01-01T14:39:38.334Z",
"modified": "2026-01-01T14:39:38.334Z",
"relationship_type": "based-on",
"source_ref": "indicator--f023d728-6ffc-4254-af30-028e5e8d4e7a",
"target_ref": "domain-name--d3c35010-338f-4085-8c75-abac163b2ebd"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--d8a3958d-0d66-4ff5-8bb7-09efbc930888",
"created": "2026-01-01T14:39:38.348Z",
"modified": "2026-01-01T14:39:38.348Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'www.liveupdt.com']",
"pattern_type": "stix",
"valid_from": "2026-01-01T14:39:38.348Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--608b286c-51ec-49b1-a296-122d54587e9d",
"created": "2026-01-01T14:39:38.348Z",
"modified": "2026-01-01T14:39:38.348Z",
"relationship_type": "based-on",
"source_ref": "indicator--d8a3958d-0d66-4ff5-8bb7-09efbc930888",
"target_ref": "domain-name--9761b8ae-0967-489c-ad1f-852893085ac7"
}
]
}Download: Download 2026-01-01-stix.json
Sharing options coming soon