[copy]
{
"type": "bundle",
"id": "bundle--b6c33ca3-b989-46e2-9080-eb7512eb2be7",
"objects": [
{
"type": "marking-definition",
"spec_version": "2.1",
"id": "marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"created": "2022-10-01T00:00:00.000Z",
"definition_type": "tlp:2.0",
"name": "TLP:CLEAR",
"definition": {
"tlp": "clear"
}
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--c6a73b9b-e7c2-4a05-a3f6-836b83bc513a",
"created": "2025-12-31T17:04:28.334Z",
"modified": "2025-12-31T17:04:28.334Z",
"name": "MikeGPT Intelligence Platform",
"description": "AI-powered threat intelligence collection and analysis platform providing automated cybersecurity intelligence feeds",
"identity_class": "organization",
"sectors": [
"technology",
"defense"
],
"contact_information": "Website: https://mikegptai.com | Email: intel@mikegptai.com",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"type": "report",
"spec_version": "2.1",
"id": "report--6c8c9cb3-d706-4767-8538-2f8384c370b6",
"created": "2025-12-31T17:04:28.334Z",
"modified": "2025-12-31T17:04:28.334Z",
"name": "Threat Intelligence Report - 2025-12-31",
"description": "Threat Intelligence Report - 2025-12-31\n\nThis report consolidates actionable cybersecurity intelligence from 94 sources, processed through automated threat analysis and relationship extraction.\n\nKEY FINDINGS:\n• Singapore CSA warns of maximun severity SmarterMail RCE flaw (Score: 100)\n• RondoDox botnet exploits React2Shell flaw to breach Next.js servers (Score: 100)\n• Best of 2025: News alert: SquareX research finds browser AI agents are proving riskier than human em (Score: 100)\n• IBM Warns of Critical API Connect Bug Allowing Remote Authentication Bypass (Score: 100)\n• Palo Alto Networks Allies with Google to Secure AI (Score: 100)\n\nEXTRACTED ENTITIES:\n• 35 Attack Pattern(s)\n• 12 File:Hashes.Md5(s)\n• 8 File:Hashes.Sha 1(s)\n• 1 Malware(s)\n• 1 Marking Definition(s)\n• 37 Relationship(s)\n• 4 Tool(s)\n• 8 Vulnerability(s)\n\nCONFIDENCE ASSESSMENT:\nVariable confidence scoring applied based on entity type and intelligence source reliability. Confidence ranges from 30-95% reflecting professional intelligence assessment practices.\n\nGENERATION METADATA:\n- Processing Time: Automated\n- Validation: Three-LLM consensus committee\n- Standards Compliance: STIX 2.1\n",
"published": "2025-12-31T17:04:28.334Z",
"object_refs": [
"identity--c6a73b9b-e7c2-4a05-a3f6-836b83bc513a",
"vulnerability--d95868d7-4f07-4d84-b742-07ee4cf4adbf",
"vulnerability--09cfd756-732a-426d-8c11-8d9ddb3e9e05",
"identity--ab826ff5-7115-490c-b135-f14a8800c4b8",
"identity--fb9c0def-15ea-4141-bcb8-aa8b6a6b268e",
"identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"tool--089ccf2c-8012-4fef-be51-58d0d9b30093",
"identity--b2a9a1d6-643a-4e4c-b7d8-1e16ef11056c",
"tool--d8cc8106-7bc1-4398-b9d4-73a132b0ee40",
"identity--b3a97109-7af0-4d53-8687-f9fbd15a98aa",
"identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"identity--4a0ea356-910b-4135-8390-c178705bb54c",
"identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"identity--5653d5fd-3625-41d2-b03e-b4bf2db2b5f8",
"vulnerability--529a846b-9748-411d-8c11-8180c182421c",
"vulnerability--81f0316c-e636-4b2b-99fc-5628dfe2c6dc",
"vulnerability--f2c42dbe-e16d-4283-9151-c7c085f96cb9",
"identity--dc1263f3-2308-479e-be5c-f6e47388fa29",
"tool--5710c74e-0f15-469a-802b-435fad89ebe9",
"identity--ab072da6-79f6-4bb8-b1b2-84174a100596",
"malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"identity--5ffaaae0-c3a4-49bb-bb57-38e94dbe7c19",
"tool--65ccf4fb-0919-4be6-9835-b712b1f056a5",
"identity--e7aaa346-3c47-410b-b7ac-2f53a69389c5",
"identity--a1d5fbd8-8b8c-4153-b138-39173f8f9967",
"attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"attack-pattern--06cf8802-38e4-4421-a699-33a0bae74d96",
"attack-pattern--2e52cc86-c2ef-43d7-9f1e-2fc59c4845ee",
"attack-pattern--943edc6f-c0f9-48f1-b8d4-4666aa0abae1",
"attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"attack-pattern--377974c7-bd54-4476-9f52-26c0fdd410e4",
"attack-pattern--d8c19aae-4529-4107-99a6-36dce8e073a4",
"attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"attack-pattern--b62ebbf0-ec9b-418e-a094-2c8fdd5234b7",
"attack-pattern--f4a2a757-99db-48e9-b04d-e17b178a8318",
"attack-pattern--239957f5-5ae1-4977-a451-144fae4a6361",
"attack-pattern--181753c8-21ea-4cce-a21e-fc6cfbaee56b",
"attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"attack-pattern--4b0a5199-2908-43a4-87bb-f021b55f6001",
"attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"attack-pattern--5cd42343-7b5a-4509-9e09-23572a60413a",
"attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"relationship--ebe694bd-cf3f-43e5-9af3-14c963cc8e3f",
"relationship--437c5c37-fcfc-40c2-91fd-6775deb5c368",
"relationship--74d68c96-8c5f-4ec2-be25-1a97309b6c08",
"relationship--e992b849-7dd9-4dd1-aaf4-166fefd7129f",
"relationship--9ec9fb3e-30fc-4f93-9ee4-58a441560b4f",
"relationship--c569956f-729a-43fd-80a2-3e9bfe36928f",
"relationship--28c123c4-ac81-44c7-b2a5-96c36eb4a0c4",
"relationship--a2ea6cfc-88d8-4712-8fab-089b6f788b90",
"relationship--062fd10f-a35b-4312-a3db-0660cbb38493",
"relationship--898d9582-be35-494f-b3ce-49da2a1d34d2",
"relationship--13382d3a-adcd-4361-95f7-78d5e2d8a0b5",
"relationship--102c4b4f-0347-49d2-83c1-732492f73579",
"relationship--b976a843-e5a8-48f5-9572-9c237955d400",
"relationship--97fb861c-c957-40ae-82dc-e1d0c3167f2c",
"relationship--742cc6c0-5228-4179-9a5f-f63e62c83fa5",
"relationship--5811087c-b226-4934-be7a-a4f5c11f0301",
"relationship--c7aa0899-bd5c-4d6b-9d95-b6ae5d64351e",
"relationship--61ae4d00-0c08-49f9-b5a3-67c6a9b03dac",
"relationship--d5fe93a0-1429-4390-b5d1-5cd3aa06ecb3",
"relationship--a32cbc42-e823-45b4-8b12-dbeb440c94e7",
"relationship--479e5bd1-6a72-4830-8799-04b3950b7110",
"relationship--ca8f7a92-fd4f-4b43-965c-74b8325d04d1",
"relationship--178fff0c-f4a8-4ab2-b235-e1d46aea2cbf",
"relationship--c864da7f-a2b0-43ea-8c26-86f0c0f1e530",
"relationship--6c9f3481-aef3-43d0-9a75-e029a17f6fe2",
"relationship--c90d5cfa-0add-4b29-8c02-5947d9d5a6c4",
"relationship--78c36f05-716c-417e-b086-6b34b8951f50",
"relationship--d4273d67-ba9e-4285-8a39-1d2e5dc9bef3",
"relationship--e9eb3d49-5300-44c4-8c48-33377d64ea58",
"relationship--4505ba00-d2f8-4fff-96e4-95cc1dea480e",
"relationship--a5c39fcd-4522-4c4a-8717-60b5f52402ff",
"relationship--674befbc-e62a-40ac-ae4f-0b037aedcd78",
"relationship--d7eca5eb-c36e-40a6-aa04-c1b668db6e4b",
"relationship--2a324885-4ea4-4c8e-ac9e-7cdf66248524",
"relationship--d29f5297-dfc0-40df-a21f-d519f7df79c5",
"relationship--963bc179-1c56-40b9-b836-94fa18c67f4f",
"relationship--142b1913-ca5c-415a-a93e-ba2f6dc7ff6d",
"file:hashes.MD5--a798e11c-0306-49f5-bf64-940cfdda1e70",
"file:hashes.MD5--847fdb8f-61b0-4680-ab2e-4a1581061b10",
"file:hashes.MD5--fe55d4a2-631e-4a19-9bdb-4a49fa6be005",
"file:hashes.MD5--aee8be26-b136-4999-ad8e-7fd1f0568443",
"file:hashes.MD5--fe900a02-fb8a-45bb-91dd-a56d144fd8f7",
"file:hashes.MD5--c3123029-e898-4817-9283-35f6f959363a",
"file:hashes.MD5--35686428-c752-4ba5-acdd-cf41a0b7abb5",
"file:hashes.MD5--37560631-e271-4d3b-8c91-dfce2aff1210",
"file:hashes.MD5--8d5ae97e-3b0a-4dff-b0b9-2470baa94fb7",
"file:hashes.MD5--97de01ae-0de5-4742-a44e-f6c86a481972",
"file:hashes.MD5--d3e124b8-20d7-4c8e-8c19-45dd248cc9af",
"file:hashes.MD5--2e266c9f-e764-495d-b4d4-0063ec51b72a",
"file:hashes.SHA-1--8897df2d-abde-410e-a23f-8f240f4131fe",
"file:hashes.SHA-1--af513657-ca96-4933-a99e-45b230136dbc",
"file:hashes.SHA-1--f071d991-0ac0-4241-bd59-ec7a1380bfa2",
"file:hashes.SHA-1--d3a928c7-dce3-4115-abca-af0df157efd8",
"file:hashes.SHA-1--0e06416a-4130-408e-b4f0-b2b143849b63",
"file:hashes.SHA-1--90963843-795a-40ae-9cbd-3736f1bc831e",
"file:hashes.SHA-1--2011bd08-22a9-4de7-947e-23ae0c847a52",
"file:hashes.SHA-1--77d268f9-a024-4171-b317-ef3e8d524ffe"
],
"labels": [
"threat-report",
"threat-intelligence"
],
"created_by_ref": "identity--c6a73b9b-e7c2-4a05-a3f6-836b83bc513a",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.328Z",
"modified": "2025-12-31T17:04:28.328Z",
"confidence": 89,
"type": "vulnerability",
"id": "vulnerability--d95868d7-4f07-4d84-b742-07ee4cf4adbf",
"name": "React2Shell",
"description": "React2Shell is a vulnerability in React Server Components that could lead to denial-of-service attacks or the exposure of source code. It is one of several recently discovered flaws in React Server Components, including CVE-2025-55183, CVE-2025-55184, and CVE-2025-67779. React2Shell is considered a dangerous vulnerability that requires immediate attention from security teams to prevent exploitation by threat actors.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.328Z",
"modified": "2025-12-31T17:04:28.328Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--09cfd756-732a-426d-8c11-8d9ddb3e9e05",
"name": "CVE-2025-55182",
"description": "A pre-authentication remote code execution vulnerability exists in React Server Components versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0 including the following packages: react-server-dom-parcel, react-server-dom-turbopack, and react-server-dom-webpack. The vulnerable code unsafely deserializes payloads from HTTP requests to Server Function endpoints.. CVSS Score: 10.0 (CRITICAL). CISA KEV: Active exploitation confirmed. EPSS: 48.7% exploitation probability",
"x_cvss_score": 10.0,
"x_cvss_severity": "CRITICAL",
"x_kev_status": true,
"x_epss_score": 0.48714,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-55182",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-55182"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-55182",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-55182"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.329Z",
"modified": "2025-12-31T17:04:28.329Z",
"confidence": 95,
"type": "identity",
"id": "identity--ab826ff5-7115-490c-b135-f14a8800c4b8",
"name": "Palo Alto",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Palo Alto is a cybersecurity company.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.329Z",
"modified": "2025-12-31T17:04:28.329Z",
"confidence": 95,
"type": "identity",
"id": "identity--fb9c0def-15ea-4141-bcb8-aa8b6a6b268e",
"name": "Google Cloud",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cloud computing platform",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.329Z",
"modified": "2025-12-31T17:04:28.329Z",
"confidence": 95,
"type": "identity",
"id": "identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"name": "Google",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Google is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.329Z",
"modified": "2025-12-31T17:04:28.329Z",
"confidence": 95,
"type": "tool",
"id": "tool--089ccf2c-8012-4fef-be51-58d0d9b30093",
"name": "Anritsu ShockLine",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A network testing tool",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.329Z",
"modified": "2025-12-31T17:04:28.329Z",
"confidence": 95,
"type": "identity",
"id": "identity--b2a9a1d6-643a-4e4c-b7d8-1e16ef11056c",
"name": "Anton",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity professional",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "tool",
"id": "tool--d8cc8106-7bc1-4398-b9d4-73a132b0ee40",
"name": "Cloud Security Podcast",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A cybersecurity-focused podcast",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 88,
"type": "identity",
"id": "identity--b3a97109-7af0-4d53-8687-f9fbd15a98aa",
"name": "Oracle Breach",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A security breach in Oracle's systems",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"name": "Security Boulevard",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"name": "Non-Human Identities",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--4a0ea356-910b-4135-8390-c178705bb54c",
"name": "LinkedIn",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "LinkedIn is a social networking platform designed for professionals and businesses to connect and share information. As a major online platform, LinkedIn's data is a valuable target for threat actors seeking to exploit professional networks for social engineering attacks. The exposure of 4.3 billion professional records, including LinkedIn data, poses a significant risk to individuals and organizations, enabling large-scale AI-driven social engineering attacks.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"name": "Cybersecurity",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Cybersecurity is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"name": "Sausalito",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 87,
"type": "vulnerability",
"id": "vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"name": "SecurityWeek",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"name": "China",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "China is a country.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"name": "MongoBleed",
"description": "An event where data is accessed without authorization.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"name": "CVE-2025-14847",
"description": "Mismatched length fields in Zlib compressed protocol headers may allow a read of uninitialized heap memory by an unauthenticated client. This issue affects all MongoDB Server v7.0 prior to 7.0.28 versions, MongoDB Server v8.0 versions prior to 8.0.17, MongoDB Server v8.2 versions prior to 8.2.3, MongoDB Server v6.0 versions prior to 6.0.27, MongoDB Server v5.0 versions prior to 5.0.32, MongoDB Server v4.4 versions prior to 4.4.30, MongoDB Server v4.2 versions greater than or equal to 4.2.0, Mong. CVSS Score: 7.5 (HIGH). CISA KEV: Active exploitation confirmed. EPSS: 77.2% exploitation probability",
"x_cvss_score": 7.5,
"x_cvss_severity": "HIGH",
"x_kev_status": true,
"x_epss_score": 0.77171,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-14847",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-14847"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-14847",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-14847"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--5653d5fd-3625-41d2-b03e-b4bf2db2b5f8",
"name": "Amazon",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Amazon is a multinational technology company that focuses on e-commerce, cloud computing, digital streaming, and artificial intelligence.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 75,
"type": "vulnerability",
"id": "vulnerability--529a846b-9748-411d-8c11-8180c182421c",
"name": "CVE-2025-15349",
"description": "The following CVEs are assigned: CVE-2025-15349.",
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-15349",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-15349"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-15349",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-15349"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--81f0316c-e636-4b2b-99fc-5628dfe2c6dc",
"name": "CVE-2025-52691",
"description": "Successful exploitation of the vulnerability could allow an unauthenticated attacker to upload arbitrary files to any location on the mail server, potentially enabling remote code execution.. CVSS Score: 10.0 (CRITICAL). EPSS: 0.2% exploitation probability",
"x_cvss_score": 10.0,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.00177,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-52691",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-52691"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-52691",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-52691"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--f2c42dbe-e16d-4283-9151-c7c085f96cb9",
"name": "CVE-2025-13915",
"description": "IBM API Connect 10.0.8.0 through 10.0.8.5, and 10.0.11.0 could allow a remote attacker to bypass authentication mechanisms and gain unauthorized access to the application.. CVSS Score: 9.8 (CRITICAL). EPSS: 0.3% exploitation probability",
"x_cvss_score": 9.8,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.00312,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-13915",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-13915"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-13915",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-13915"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--dc1263f3-2308-479e-be5c-f6e47388fa29",
"name": "Singapore",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A country with a Cyber Security Agency",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "tool",
"id": "tool--5710c74e-0f15-469a-802b-435fad89ebe9",
"name": "SmarterMail",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Email server software with a known vulnerability",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--ab072da6-79f6-4bb8-b1b2-84174a100596",
"name": "Cyber Security Agency",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A government agency responsible for cybersecurity",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "malware",
"id": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"name": "RondoDox",
"is_family": true,
"malware_types": [
"bot"
],
"labels": [
"malicious-activity"
],
"description": "A botnet exploiting a vulnerability",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--5ffaaae0-c3a4-49bb-bb57-38e94dbe7c19",
"name": "SquareX",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A company researching cybersecurity",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "tool",
"id": "tool--65ccf4fb-0919-4be6-9835-b712b1f056a5",
"name": "API Connect",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "Software with a known vulnerability",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--e7aaa346-3c47-410b-b7ac-2f53a69389c5",
"name": "Strobes Security",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A company providing cybersecurity services",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 95,
"type": "identity",
"id": "identity--a1d5fbd8-8b8c-4153-b138-39173f8f9967",
"name": "Sygnia",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A company providing cybersecurity services",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.330Z",
"modified": "2025-12-31T17:04:28.330Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"name": "Command and Scripting Interpreter",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/",
"external_id": "T1059"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"name": "Exploitation for Client Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1203",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1203/",
"external_id": "T1203"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"name": "Exploit Public-Facing Application",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1190",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1190/",
"external_id": "T1190"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"name": "Remote Services",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "lateral-movement"
}
],
"x_mitre_id": "T1021",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1021/",
"external_id": "T1021"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"name": "Spearphishing Attachment",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/001/",
"external_id": "T1566.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"name": "Spearphishing Link",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/002/",
"external_id": "T1566.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"name": "Spearphishing via Service",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/003/",
"external_id": "T1566.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"name": "Modify Registry",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1112",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1112/",
"external_id": "T1112"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"name": "Registry Run Keys / Startup Folder",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/001/",
"external_id": "T1547.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--06cf8802-38e4-4421-a699-33a0bae74d96",
"name": "System Information Discovery",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "discovery"
}
],
"x_mitre_id": "T1082",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1082/",
"external_id": "T1082"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2e52cc86-c2ef-43d7-9f1e-2fc59c4845ee",
"name": "File and Directory Discovery",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "discovery"
}
],
"x_mitre_id": "T1083",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1083/",
"external_id": "T1083"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--943edc6f-c0f9-48f1-b8d4-4666aa0abae1",
"name": "Process Discovery",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "discovery"
}
],
"x_mitre_id": "T1057",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1057/",
"external_id": "T1057"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"name": "Create or Modify System Process",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1543",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1543/",
"external_id": "T1543"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"name": "Boot or Logon Autostart Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/",
"external_id": "T1547"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"name": "Supply Chain Compromise",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1195",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1195/",
"external_id": "T1195"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--377974c7-bd54-4476-9f52-26c0fdd410e4",
"name": "Credential Stuffing",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
}
],
"x_mitre_id": "T1110.004",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1110/004/",
"external_id": "T1110.004"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--d8c19aae-4529-4107-99a6-36dce8e073a4",
"name": "ARP Cache Poisoning",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/002/",
"external_id": "T1557.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"name": "Abuse Elevation Control Mechanism",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1548",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1548/",
"external_id": "T1548"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"name": "Access Token Manipulation",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1134",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1134/",
"external_id": "T1134"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"name": "Browser Extensions",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1176.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1176/001/",
"external_id": "T1176.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--b62ebbf0-ec9b-418e-a094-2c8fdd5234b7",
"name": "Clipboard Data",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1115",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1115/",
"external_id": "T1115"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--f4a2a757-99db-48e9-b04d-e17b178a8318",
"name": "Credentials from Web Browsers",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
}
],
"x_mitre_id": "T1555.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1555/003/",
"external_id": "T1555.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 79,
"type": "attack-pattern",
"id": "attack-pattern--239957f5-5ae1-4977-a451-144fae4a6361",
"name": "Software Extensions",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1176",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1176/",
"external_id": "T1176"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 75,
"type": "attack-pattern",
"id": "attack-pattern--181753c8-21ea-4cce-a21e-fc6cfbaee56b",
"name": "Kernel Modules and Extensions",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/006/",
"external_id": "T1547.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 73,
"type": "attack-pattern",
"id": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"name": "Vulnerabilities",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/006/",
"external_id": "T1588.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.331Z",
"modified": "2025-12-31T17:04:28.331Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"name": "Spearphishing Voice",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "reconnaissance"
}
],
"x_mitre_id": "T1598.004",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1598/004/",
"external_id": "T1598.004"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--4b0a5199-2908-43a4-87bb-f021b55f6001",
"name": "Cloud Services",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "lateral-movement"
}
],
"x_mitre_id": "T1021.007",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1021/007/",
"external_id": "T1021.007"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"name": "Archive via Utility",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1560.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1560/001/",
"external_id": "T1560.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"name": "Screen Capture",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1113",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1113/",
"external_id": "T1113"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"name": "Adversary-in-the-Middle",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/",
"external_id": "T1557"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"name": "Scheduled Task",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1053.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1053/005/",
"external_id": "T1053.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"name": "Socket Filters",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1205.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1205/002/",
"external_id": "T1205.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 69,
"type": "attack-pattern",
"id": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"name": "Botnet",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1584.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1584/005/",
"external_id": "T1584.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 67,
"type": "attack-pattern",
"id": "attack-pattern--5cd42343-7b5a-4509-9e09-23572a60413a",
"name": "Domain or Tenant Policy Modification",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1484",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1484/",
"external_id": "T1484"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"confidence": 66,
"type": "attack-pattern",
"id": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"name": "Artificial Intelligence",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.007",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/007/",
"external_id": "T1588.007"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ebe694bd-cf3f-43e5-9af3-14c963cc8e3f",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "exploits",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "vulnerability--09cfd756-732a-426d-8c11-8d9ddb3e9e05",
"confidence": 85,
"description": "Co-occurrence in intelligence context",
"x_validation_method": "three-llm-consensus"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--437c5c37-fcfc-40c2-91fd-6775deb5c368",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Command and Scripting Interpreter (T1059) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--74d68c96-8c5f-4ec2-be25-1a97309b6c08",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Exploitation for Client Execution (T1203) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e992b849-7dd9-4dd1-aaf4-166fefd7129f",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Exploit Public-Facing Application (T1190) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--9ec9fb3e-30fc-4f93-9ee4-58a441560b4f",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Remote Services (T1021) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c569956f-729a-43fd-80a2-3e9bfe36928f",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Attachment (T1566.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--28c123c4-ac81-44c7-b2a5-96c36eb4a0c4",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Link (T1566.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a2ea6cfc-88d8-4712-8fab-089b6f788b90",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing via Service (T1566.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--062fd10f-a35b-4312-a3db-0660cbb38493",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Modify Registry (T1112) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--898d9582-be35-494f-b3ce-49da2a1d34d2",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Registry Run Keys / Startup Folder (T1547.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--13382d3a-adcd-4361-95f7-78d5e2d8a0b5",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--06cf8802-38e4-4421-a699-33a0bae74d96",
"confidence": 55,
"description": "Co-occurrence: RondoDox and System Information Discovery (T1082) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--102c4b4f-0347-49d2-83c1-732492f73579",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--2e52cc86-c2ef-43d7-9f1e-2fc59c4845ee",
"confidence": 55,
"description": "Co-occurrence: RondoDox and File and Directory Discovery (T1083) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b976a843-e5a8-48f5-9572-9c237955d400",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--943edc6f-c0f9-48f1-b8d4-4666aa0abae1",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Process Discovery (T1057) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--97fb861c-c957-40ae-82dc-e1d0c3167f2c",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Create or Modify System Process (T1543) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--742cc6c0-5228-4179-9a5f-f63e62c83fa5",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Boot or Logon Autostart Execution (T1547) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5811087c-b226-4934-be7a-a4f5c11f0301",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--13fc9cbe-9444-4eba-872b-a44565ae3ab7",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Supply Chain Compromise (T1195) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c7aa0899-bd5c-4d6b-9d95-b6ae5d64351e",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--377974c7-bd54-4476-9f52-26c0fdd410e4",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Credential Stuffing (T1110.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--61ae4d00-0c08-49f9-b5a3-67c6a9b03dac",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--d8c19aae-4529-4107-99a6-36dce8e073a4",
"confidence": 55,
"description": "Co-occurrence: RondoDox and ARP Cache Poisoning (T1557.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d5fe93a0-1429-4390-b5d1-5cd3aa06ecb3",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--f33f5834-6a9a-4727-88a5-9d35eeba1cff",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Abuse Elevation Control Mechanism (T1548) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a32cbc42-e823-45b4-8b12-dbeb440c94e7",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Access Token Manipulation (T1134) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--479e5bd1-6a72-4830-8799-04b3950b7110",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Browser Extensions (T1176.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ca8f7a92-fd4f-4b43-965c-74b8325d04d1",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--b62ebbf0-ec9b-418e-a094-2c8fdd5234b7",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Clipboard Data (T1115) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--178fff0c-f4a8-4ab2-b235-e1d46aea2cbf",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--f4a2a757-99db-48e9-b04d-e17b178a8318",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Credentials from Web Browsers (T1555.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c864da7f-a2b0-43ea-8c26-86f0c0f1e530",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--239957f5-5ae1-4977-a451-144fae4a6361",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Software Extensions (T1176) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--6c9f3481-aef3-43d0-9a75-e029a17f6fe2",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--181753c8-21ea-4cce-a21e-fc6cfbaee56b",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Kernel Modules and Extensions (T1547.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c90d5cfa-0add-4b29-8c02-5947d9d5a6c4",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Vulnerabilities (T1588.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--78c36f05-716c-417e-b086-6b34b8951f50",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Voice (T1598.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d4273d67-ba9e-4285-8a39-1d2e5dc9bef3",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--4b0a5199-2908-43a4-87bb-f021b55f6001",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Cloud Services (T1021.007) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e9eb3d49-5300-44c4-8c48-33377d64ea58",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Archive via Utility (T1560.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4505ba00-d2f8-4fff-96e4-95cc1dea480e",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Screen Capture (T1113) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a5c39fcd-4522-4c4a-8717-60b5f52402ff",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Adversary-in-the-Middle (T1557) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--674befbc-e62a-40ac-ae4f-0b037aedcd78",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Scheduled Task (T1053.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d7eca5eb-c36e-40a6-aa04-c1b668db6e4b",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.332Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Socket Filters (T1205.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2a324885-4ea4-4c8e-ac9e-7cdf66248524",
"created": "2025-12-31T17:04:28.332Z",
"modified": "2025-12-31T17:04:28.333Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--624fa034-c944-4489-a990-1f1111e2e237",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Botnet (T1584.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d29f5297-dfc0-40df-a21f-d519f7df79c5",
"created": "2025-12-31T17:04:28.333Z",
"modified": "2025-12-31T17:04:28.333Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--8a0e81d0-0fa8-4d20-949d-13759bec09a7",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Spearphishing Voice (T1566.004) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--963bc179-1c56-40b9-b836-94fa18c67f4f",
"created": "2025-12-31T17:04:28.333Z",
"modified": "2025-12-31T17:04:28.333Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--5cd42343-7b5a-4509-9e09-23572a60413a",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Domain or Tenant Policy Modification (T1484) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--142b1913-ca5c-415a-a93e-ba2f6dc7ff6d",
"created": "2025-12-31T17:04:28.333Z",
"modified": "2025-12-31T17:04:28.333Z",
"relationship_type": "uses",
"source_ref": "malware--f0ecd81c-a5a3-471e-813d-242ae1d86322",
"target_ref": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"confidence": 55,
"description": "Co-occurrence: RondoDox and Artificial Intelligence (T1588.007) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "file:hashes.MD5",
"value": "210600be82239d3cc845b993ef7713e2",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--a798e11c-0306-49f5-bf64-940cfdda1e70"
},
{
"type": "file:hashes.MD5",
"value": "242bc60a43eabeed6410fdb3e2428a3a",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--847fdb8f-61b0-4680-ab2e-4a1581061b10"
},
{
"type": "file:hashes.MD5",
"value": "297bec80a7bee340d10d4ea429909796",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--fe55d4a2-631e-4a19-9bdb-4a49fa6be005"
},
{
"type": "file:hashes.MD5",
"value": "3ba7a49934b2f5fdb01e5ba157a66c98",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--aee8be26-b136-4999-ad8e-7fd1f0568443"
},
{
"type": "file:hashes.MD5",
"value": "50608632718649bc00ab1edf5724a9af",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--fe900a02-fb8a-45bb-91dd-a56d144fd8f7"
},
{
"type": "file:hashes.MD5",
"value": "6536ebe330f403aa8d574f45cb8e72cb",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--c3123029-e898-4817-9283-35f6f959363a"
},
{
"type": "file:hashes.MD5",
"value": "73a19307b88c0e9468b49ee3135be5f4",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--35686428-c752-4ba5-acdd-cf41a0b7abb5"
},
{
"type": "file:hashes.MD5",
"value": "7a0c180b3fdc7fe574aaf9f6502d8496",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--37560631-e271-4d3b-8c91-dfce2aff1210"
},
{
"type": "file:hashes.MD5",
"value": "a98f4242a2281e1f32e51f0cfed391b0",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--8d5ae97e-3b0a-4dff-b0b9-2470baa94fb7"
},
{
"type": "file:hashes.MD5",
"value": "b9719cea1bf4f95c7632975b82876f96",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--97de01ae-0de5-4742-a44e-f6c86a481972"
},
{
"type": "file:hashes.MD5",
"value": "c0df8197455bae7b8a6ca2e835867a6a",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--d3e124b8-20d7-4c8e-8c19-45dd248cc9af"
},
{
"type": "file:hashes.MD5",
"value": "f022baae5f1873b46aaf2c5cc03e1e21",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.MD5--2e266c9f-e764-495d-b4d4-0063ec51b72a"
},
{
"type": "file:hashes.SHA-1",
"value": "0287d785d44bb1cab51a6c3278a90c84de5f6a02",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--8897df2d-abde-410e-a23f-8f240f4131fe"
},
{
"type": "file:hashes.SHA-1",
"value": "0ba9196a71259d3a2ca0b5b92dba196d82fde0fc",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--af513657-ca96-4933-a99e-45b230136dbc"
},
{
"type": "file:hashes.SHA-1",
"value": "10a96be58694716d36b3f18835aa24dc2e964967",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--f071d991-0ac0-4241-bd59-ec7a1380bfa2"
},
{
"type": "file:hashes.SHA-1",
"value": "2f42087269ba4138acddbab8537c9d80c4f8bea8",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--d3a928c7-dce3-4115-abca-af0df157efd8"
},
{
"type": "file:hashes.SHA-1",
"value": "4b19500185e82a7454a046caba1c20678b2f6fad",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--0e06416a-4130-408e-b4f0-b2b143849b63"
},
{
"type": "file:hashes.SHA-1",
"value": "b8f3ff1cb8c1eb350767d07e2d88e329e5ff0807",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--90963843-795a-40ae-9cbd-3736f1bc831e"
},
{
"type": "file:hashes.SHA-1",
"value": "bd289ef73d5604939e6f157fba4a3f601ac22a93",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--2011bd08-22a9-4de7-947e-23ae0c847a52"
},
{
"type": "file:hashes.SHA-1",
"value": "c1cb2cb474cd2b5b9054e1fcfb6996a9d156e49e",
"source": "OTX",
"malware_families": [
"RondoDox"
],
"pulse_names": [
"RondoDox Unveiled: Breaking Down a New Botnet Threat"
],
"id": "file:hashes.SHA-1--77d268f9-a024-4171-b317-ef3e8d524ffe"
}
]
}


 CRITICAL ITEMS
CRITICAL ITEMS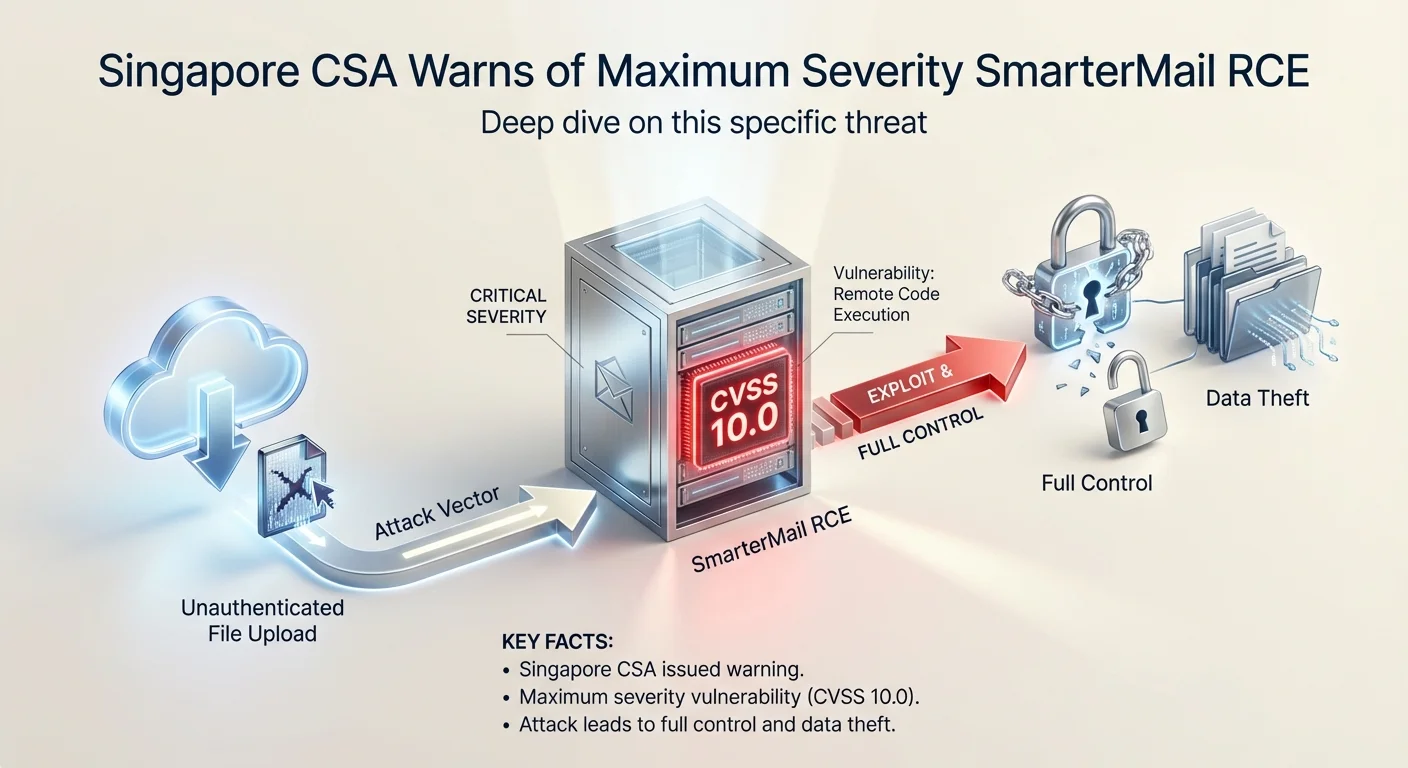
 HIGH SEVERITY ITEMS
HIGH SEVERITY ITEMS
 EXECUTIVE INSIGHTS
EXECUTIVE INSIGHTS VENDOR SPOTLIGHT
VENDOR SPOTLIGHT DETECTION & RESPONSE KIT
DETECTION & RESPONSE KIT