[copy]
{
"type": "bundle",
"id": "bundle--7d9e0160-8f4f-405f-801c-278dba185fd9",
"objects": [
{
"type": "marking-definition",
"spec_version": "2.1",
"id": "marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"created": "2022-10-01T00:00:00.000Z",
"definition_type": "tlp:2.0",
"name": "TLP:CLEAR",
"definition": {
"tlp": "clear"
}
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--7b112455-7d99-4b76-9db9-0ec1469f8859",
"created": "2025-12-30T15:18:36.144Z",
"modified": "2025-12-30T15:18:36.144Z",
"name": "MikeGPT Intelligence Platform",
"description": "AI-powered threat intelligence collection and analysis platform providing automated cybersecurity intelligence feeds",
"identity_class": "organization",
"sectors": [
"technology",
"defense"
],
"contact_information": "Website: https://mikegptai.com | Email: intel@mikegptai.com",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"type": "report",
"spec_version": "2.1",
"id": "report--3f852966-8828-4f34-9e03-8c5daf4319f0",
"created": "2025-12-30T15:18:36.145Z",
"modified": "2025-12-30T15:18:36.145Z",
"name": "Threat Intelligence Report - 2025-12-30",
"description": "Threat Intelligence Report - 2025-12-30\n\nThis report consolidates actionable cybersecurity intelligence from 86 sources, processed through automated threat analysis and relationship extraction.\n\nKEY FINDINGS:\n• ZDI-25-1200: (0Day) Anritsu ShockLine SCPI Race Condition Remote Code Execution Vulnerability (Score: 100)\n• Best of 2025: Oracle Breach: The Impact is Bigger Than You Think | Grip (Score: 100)\n• Anton’s Security Blog Quarterly Q4 2025 (Score: 100)\n• U.S. CISA adds a flaw in MongoDB Server to its Known Exploited Vulnerabilities catalog (Score: 100)\n• MongoBleed defect swirls, stamping out hope of year-end respite (Score: 100)\n\nEXTRACTED ENTITIES:\n• 29 Attack Pattern(s)\n• 1 Marking Definition(s)\n• 3 Tool(s)\n• 8 Vulnerability(s)\n\nCONFIDENCE ASSESSMENT:\nVariable confidence scoring applied based on entity type and intelligence source reliability. Confidence ranges from 30-95% reflecting professional intelligence assessment practices.\n\nGENERATION METADATA:\n- Processing Time: Automated\n- Validation: Three-LLM consensus committee\n- Standards Compliance: STIX 2.1\n",
"published": "2025-12-30T15:18:36.145Z",
"object_refs": [
"identity--7b112455-7d99-4b76-9db9-0ec1469f8859",
"vulnerability--3429ba46-9d14-4bf2-94b3-b58e4cd7a269",
"vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"tool--4cc7aac6-53bb-4fd2-94f9-f2d3d05ad748",
"vulnerability--529a846b-9748-411d-8c11-8180c182421c",
"vulnerability--f657b609-daab-4236-9b1d-24e71a267d0e",
"vulnerability--993c9315-fd98-4117-b938-a977f0706975",
"tool--089ccf2c-8012-4fef-be51-58d0d9b30093",
"identity--b3a97109-7af0-4d53-8687-f9fbd15a98aa",
"identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"identity--b2a9a1d6-643a-4e4c-b7d8-1e16ef11056c",
"identity--fb9c0def-15ea-4141-bcb8-aa8b6a6b268e",
"tool--d8cc8106-7bc1-4398-b9d4-73a132b0ee40",
"identity--4e9b4c49-e9d4-4528-94d2-741592f6960c",
"identity--74882002-dc02-42bf-b7ed-70ab30033070",
"identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"attack-pattern--d8c19aae-4529-4107-99a6-36dce8e073a4",
"attack-pattern--612a21d0-9d6a-4d03-bd0e-ae31234d4cef",
"attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"attack-pattern--b62ebbf0-ec9b-418e-a094-2c8fdd5234b7",
"attack-pattern--f4a2a757-99db-48e9-b04d-e17b178a8318",
"attack-pattern--bc6ae8c8-5b72-4bf7-85f1-4477630885a4",
"attack-pattern--d09d4c99-d4cc-4ae4-aad9-7e6c32bfc732",
"attack-pattern--e1d88fb2-b905-48ed-a931-a5f20b548774",
"attack-pattern--a9b2b3d1-728e-47be-adb2-f74a7e4c4f94",
"attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"attack-pattern--13975792-7c14-4c1e-a11e-80b1ecbde971",
"attack-pattern--4e2f5b9a-cf3a-4ab7-9169-8362c52dd57d",
"attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"attack-pattern--5cd42343-7b5a-4509-9e09-23572a60413a",
"attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"attack-pattern--d76e0650-6edf-46e7-b957-362aa1c14d07"
],
"labels": [
"threat-report",
"threat-intelligence"
],
"created_by_ref": "identity--7b112455-7d99-4b76-9db9-0ec1469f8859",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.140Z",
"modified": "2025-12-30T15:18:36.140Z",
"confidence": 88,
"type": "vulnerability",
"id": "vulnerability--3429ba46-9d14-4bf2-94b3-b58e4cd7a269",
"name": "Known Exploited Vulnerabilities",
"description": "A catalog of vulnerabilities that are known to be actively exploited.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.141Z",
"modified": "2025-12-30T15:18:36.141Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"name": "CVE-2025-14847",
"description": "Mismatched length fields in Zlib compressed protocol headers may allow a read of uninitialized heap memory by an unauthenticated client. This issue affects all MongoDB Server v7.0 prior to 7.0.28 versions, MongoDB Server v8.0 versions prior to 8.0.17, MongoDB Server v8.2 versions prior to 8.2.3, MongoDB Server v6.0 versions prior to 6.0.27, MongoDB Server v5.0 versions prior to 5.0.32, MongoDB Server v4.4 versions prior to 4.4.30, MongoDB Server v4.2 versions greater than or equal to 4.2.0, Mong. CVSS Score: 7.5 (HIGH). CISA KEV: Active exploitation confirmed. EPSS: 58.3% exploitation probability",
"x_cvss_score": 7.5,
"x_cvss_severity": "HIGH",
"x_kev_status": true,
"x_epss_score": 0.58251,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-14847",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-14847"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-14847",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-14847"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"name": "MongoBleed",
"description": "An event where data is accessed without authorization.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 95,
"type": "identity",
"id": "identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"name": "Non-Human Identities",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 89,
"type": "vulnerability",
"id": "vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"name": "CVE-2025",
"description": "A high-severity security flaw in MongoDB",
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025"
},
{
"source_name": "nvd",
"external_id": "CVE-2025",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 87,
"type": "vulnerability",
"id": "vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"name": "SecurityWeek",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 95,
"type": "identity",
"id": "identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"name": "Cybersecurity",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Cybersecurity is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 95,
"type": "tool",
"id": "tool--4cc7aac6-53bb-4fd2-94f9-f2d3d05ad748",
"name": "LastPass",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A password manager",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 75,
"type": "vulnerability",
"id": "vulnerability--529a846b-9748-411d-8c11-8180c182421c",
"name": "CVE-2025-15349",
"description": "The following CVEs are assigned: CVE-2025-15349.",
"x_cvss_severity": "Unknown",
"x_kev_status": false,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-15349",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-15349"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-15349",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-15349"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--f657b609-daab-4236-9b1d-24e71a267d0e",
"name": "CVE-2020-12812",
"description": "An improper authentication vulnerability in SSL VPN in FortiOS 6.4.0, 6.2.0 to 6.2.3, 6.0.9 and below may result in a user being able to log in successfully without being prompted for the second factor of authentication (FortiToken) if they changed the case of their username.. CVSS Score: 9.8 (CRITICAL). CISA KEV: Active exploitation confirmed. EPSS: 50.3% exploitation probability",
"x_cvss_score": 9.8,
"x_cvss_severity": "CRITICAL",
"x_kev_status": true,
"x_epss_score": 0.50292,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2020-12812",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-12812"
},
{
"source_name": "nvd",
"external_id": "CVE-2020-12812",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2020-12812"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--993c9315-fd98-4117-b938-a977f0706975",
"name": "CVE-2025-54322",
"description": "Xspeeder SXZOS through 2025-12-26 allows root remote code execution via base64-encoded Python code in the chkid parameter to vLogin.py. The title and oIP parameters are also used.. CVSS Score: 10.0 (CRITICAL). EPSS: 0.3% exploitation probability",
"x_cvss_score": 10.0,
"x_cvss_severity": "CRITICAL",
"x_kev_status": false,
"x_epss_score": 0.00287,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-54322",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-54322"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-54322",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-54322"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.142Z",
"modified": "2025-12-30T15:18:36.142Z",
"confidence": 95,
"type": "tool",
"id": "tool--089ccf2c-8012-4fef-be51-58d0d9b30093",
"name": "Anritsu ShockLine",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A network testing tool",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 88,
"type": "identity",
"id": "identity--b3a97109-7af0-4d53-8687-f9fbd15a98aa",
"name": "Oracle Breach",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A security breach in Oracle's systems",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 95,
"type": "identity",
"id": "identity--84cc9f98-37d8-4790-bdcd-597ce6a2e6ac",
"name": "Security Boulevard",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 95,
"type": "identity",
"id": "identity--b2a9a1d6-643a-4e4c-b7d8-1e16ef11056c",
"name": "Anton",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity professional",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 95,
"type": "identity",
"id": "identity--fb9c0def-15ea-4141-bcb8-aa8b6a6b268e",
"name": "Google Cloud",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cloud computing platform",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 95,
"type": "tool",
"id": "tool--d8cc8106-7bc1-4398-b9d4-73a132b0ee40",
"name": "Cloud Security Podcast",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A cybersecurity-focused podcast",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 95,
"type": "identity",
"id": "identity--4e9b4c49-e9d4-4528-94d2-741592f6960c",
"name": "Infrastructure Security Agency",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A US government agency focused on cybersecurity",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "identity",
"id": "identity--74882002-dc02-42bf-b7ed-70ab30033070",
"name": "Cyberattack",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity professional",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 95,
"type": "identity",
"id": "identity--06b70d7b-8838-4176-9d1c-742c3c4155df",
"name": "Sausalito",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity-focused online publication",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"name": "Exploit Public-Facing Application",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1190",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1190/",
"external_id": "T1190"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"name": "Exploitation for Client Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1203",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1203/",
"external_id": "T1203"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"name": "Command and Scripting Interpreter",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/",
"external_id": "T1059"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"name": "Create or Modify System Process",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1543",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1543/",
"external_id": "T1543"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"name": "Boot or Logon Autostart Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/",
"external_id": "T1547"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--d8c19aae-4529-4107-99a6-36dce8e073a4",
"name": "ARP Cache Poisoning",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/002/",
"external_id": "T1557.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--612a21d0-9d6a-4d03-bd0e-ae31234d4cef",
"name": "Brute Force",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
}
],
"x_mitre_id": "T1110",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1110/",
"external_id": "T1110"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"name": "Spearphishing Attachment",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/001/",
"external_id": "T1566.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"name": "Spearphishing Link",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/002/",
"external_id": "T1566.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"name": "Spearphishing via Service",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/003/",
"external_id": "T1566.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--b62ebbf0-ec9b-418e-a094-2c8fdd5234b7",
"name": "Clipboard Data",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1115",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1115/",
"external_id": "T1115"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--f4a2a757-99db-48e9-b04d-e17b178a8318",
"name": "Credentials from Web Browsers",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
}
],
"x_mitre_id": "T1555.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1555/003/",
"external_id": "T1555.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--bc6ae8c8-5b72-4bf7-85f1-4477630885a4",
"name": "Escape to Host",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1611",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1611/",
"external_id": "T1611"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--d09d4c99-d4cc-4ae4-aad9-7e6c32bfc732",
"name": "Data from Cloud Storage",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1530",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1530/",
"external_id": "T1530"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--e1d88fb2-b905-48ed-a931-a5f20b548774",
"name": "Cloud Storage Object Discovery",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "discovery"
}
],
"x_mitre_id": "T1619",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1619/",
"external_id": "T1619"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 85,
"type": "attack-pattern",
"id": "attack-pattern--a9b2b3d1-728e-47be-adb2-f74a7e4c4f94",
"name": "Exfiltration to Cloud Storage",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "exfiltration"
}
],
"x_mitre_id": "T1567.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1567/002/",
"external_id": "T1567.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 84,
"type": "attack-pattern",
"id": "attack-pattern--172f3845-7870-4c1c-80bd-251e10ce9f1e",
"name": "Browser Extensions",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1176.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1176/001/",
"external_id": "T1176.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 77,
"type": "attack-pattern",
"id": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"name": "Vulnerabilities",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/006/",
"external_id": "T1588.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 74,
"type": "attack-pattern",
"id": "attack-pattern--13975792-7c14-4c1e-a11e-80b1ecbde971",
"name": "Disable or Modify Linux Audit System",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
}
],
"x_mitre_id": "T1562.012",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1562/012/",
"external_id": "T1562.012"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--4e2f5b9a-cf3a-4ab7-9169-8362c52dd57d",
"name": "Search Threat Vendor Data",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "reconnaissance"
}
],
"x_mitre_id": "T1681",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1681/",
"external_id": "T1681"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"name": "Scheduled Task",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1053.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1053/005/",
"external_id": "T1053.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"name": "Socket Filters",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1205.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1205/002/",
"external_id": "T1205.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"name": "Boot or Logon Initialization Scripts",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1037",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1037/",
"external_id": "T1037"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"name": "Archive via Utility",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1560.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1560/001/",
"external_id": "T1560.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"name": "Screen Capture",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1113",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1113/",
"external_id": "T1113"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"name": "Adversary-in-the-Middle",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/",
"external_id": "T1557"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 67,
"type": "attack-pattern",
"id": "attack-pattern--5cd42343-7b5a-4509-9e09-23572a60413a",
"name": "Domain or Tenant Policy Modification",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1484",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1484/",
"external_id": "T1484"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 67,
"type": "attack-pattern",
"id": "attack-pattern--648fba01-e867-4fc6-96df-cc8f6217bee6",
"name": "Artificial Intelligence",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.007",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/007/",
"external_id": "T1588.007"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-30T15:18:36.143Z",
"modified": "2025-12-30T15:18:36.143Z",
"confidence": 66,
"type": "attack-pattern",
"id": "attack-pattern--d76e0650-6edf-46e7-b957-362aa1c14d07",
"name": "Lifecycle-Triggered Deletion",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "impact"
}
],
"x_mitre_id": "T1485.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1485/001/",
"external_id": "T1485.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
}
]
}

 CRITICAL ITEMS
CRITICAL ITEMS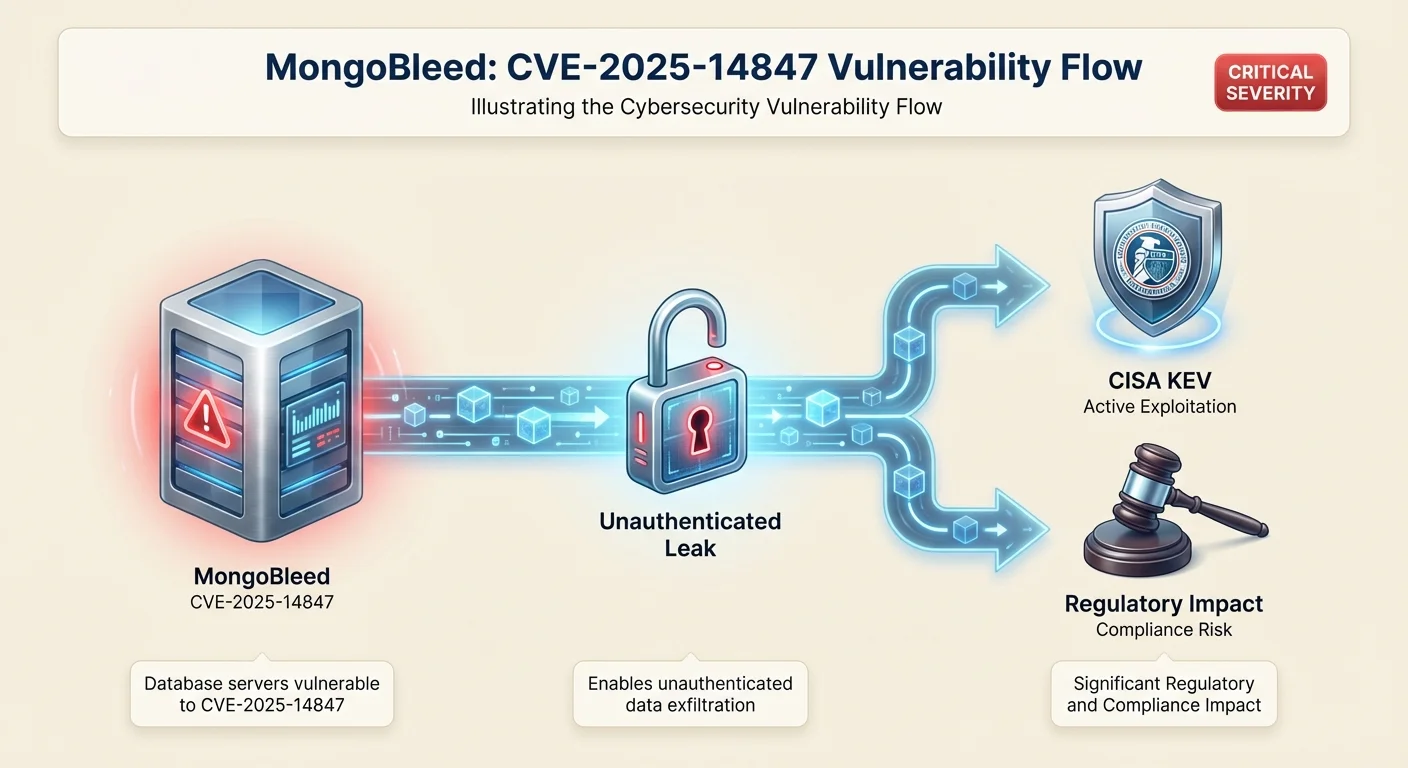
 HIGH SEVERITY ITEMS
HIGH SEVERITY ITEMS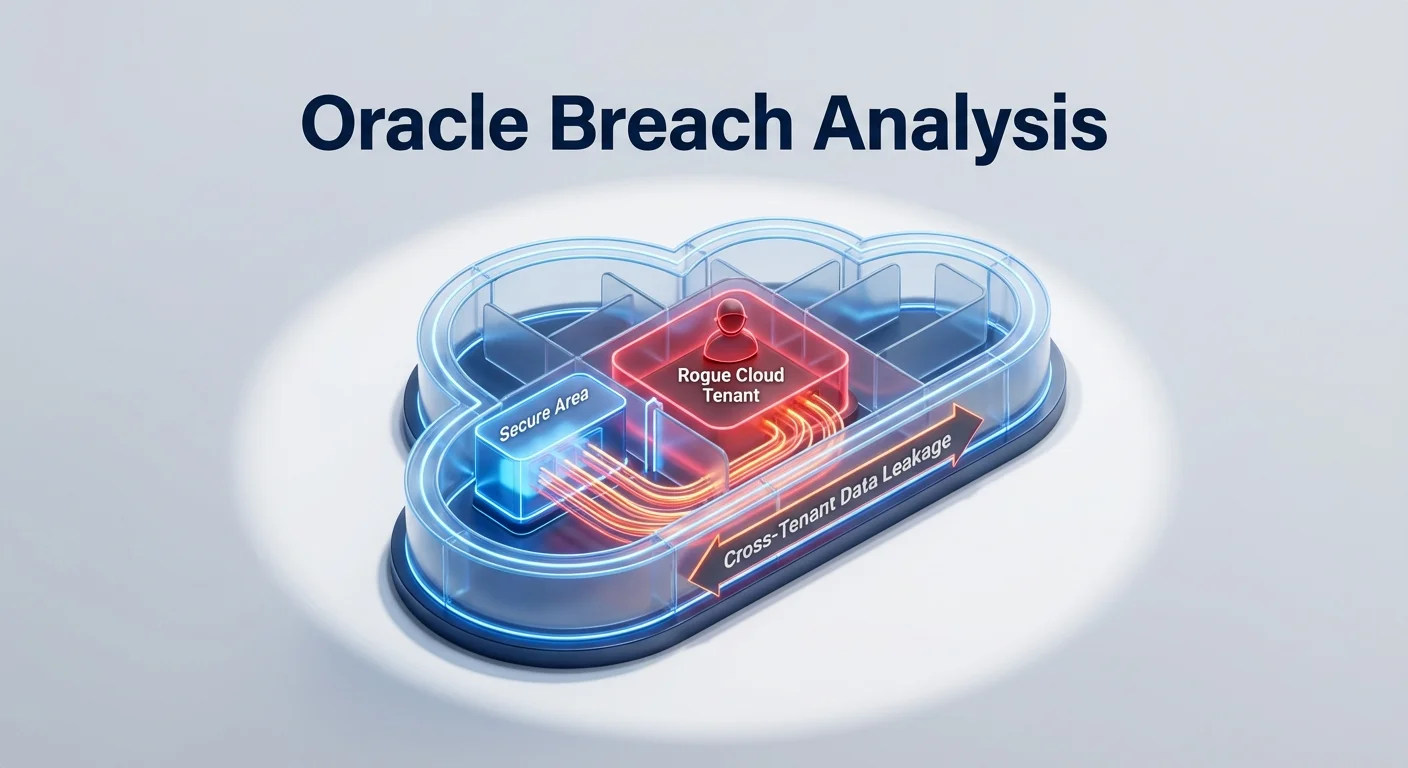
 MEDIUM SEVERITY ITEMS
MEDIUM SEVERITY ITEMS EXECUTIVE INSIGHTS
EXECUTIVE INSIGHTS VENDOR SPOTLIGHT
VENDOR SPOTLIGHT