[copy]
{
"type": "bundle",
"id": "bundle--b99c5837-11f0-4125-a322-26808d2aef77",
"objects": [
{
"type": "marking-definition",
"spec_version": "2.1",
"id": "marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"created": "2022-10-01T00:00:00.000Z",
"definition_type": "tlp:2.0",
"name": "TLP:CLEAR",
"definition": {
"tlp": "clear"
}
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--7f69d815-4b7a-447f-9a08-4bcdb4993a9c",
"created": "2025-12-29T14:14:20.998Z",
"modified": "2025-12-29T14:14:20.998Z",
"name": "MikeGPT Intelligence Platform",
"description": "AI-powered threat intelligence collection and analysis platform providing automated cybersecurity intelligence feeds",
"identity_class": "organization",
"sectors": [
"technology",
"defense"
],
"contact_information": "Website: https://mikegptai.com | Email: intel@mikegptai.com",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"type": "report",
"spec_version": "2.1",
"id": "report--a6dd9ebd-d4f9-4aae-be3b-b464990e82d2",
"created": "2025-12-29T14:14:20.998Z",
"modified": "2025-12-29T14:14:20.998Z",
"name": "Threat Intelligence Report - 2025-12-29",
"description": "Threat Intelligence Report - 2025-12-29\n\nThis report consolidates actionable cybersecurity intelligence from 46 sources, processed through automated threat analysis and relationship extraction.\n\nKEY FINDINGS:\n• Fortinet warns of 5-year-old FortiOS 2FA bypass still exploited in attacks (Score: 100)\n• The HoneyMyte APT evolves with a kernel-mode rootkit and a ToneShell backdoor (Score: 100)\n• Condé Nast faces major data breach: 2.3M WIRED records leaked, 40M more at risk (Score: 100)\n• Exploited MongoBleed flaw leaks MongoDB secrets, 87K servers exposed (Score: 100)\n• MongoDB Vuln (Score: 94.4)\n\nEXTRACTED ENTITIES:\n• 19 Attack Pattern(s)\n• 18 Domain Name(s)\n• 1 File:Hashes.Md5(s)\n• 1 File:Hashes.Sha 1(s)\n• 18 Indicator(s)\n• 1 Malware(s)\n• 1 Marking Definition(s)\n• 37 Relationship(s)\n• 1 Tool(s)\n• 7 Vulnerability(s)\n\nCONFIDENCE ASSESSMENT:\nVariable confidence scoring applied based on entity type and intelligence source reliability. Confidence ranges from 30-95% reflecting professional intelligence assessment practices.\n\nGENERATION METADATA:\n- Processing Time: Automated\n- Validation: Three-LLM consensus committee\n- Standards Compliance: STIX 2.1\n",
"published": "2025-12-29T14:14:20.998Z",
"object_refs": [
"identity--7f69d815-4b7a-447f-9a08-4bcdb4993a9c",
"identity--161fc746-cd49-4615-ab48-81a93a1b16b4",
"vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"identity--e579f0b6-29fc-4f87-be26-0870951a61da",
"identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"tool--4cc7aac6-53bb-4fd2-94f9-f2d3d05ad748",
"identity--a8a416d7-3adc-4b50-8ceb-058398accecd",
"vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"identity--3cf91ae9-0a36-4c4f-aad7-9717e2e1a2cd",
"vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"vulnerability--8a04b2e2-62df-46c1-8ecc-373a1f0e90ce",
"vulnerability--ae5f3705-fe19-4e4b-8a9f-84b24b282fe1",
"vulnerability--42344d80-ab4f-401f-8745-d935e1d5ab90",
"vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"identity--a104157d-2858-45b7-af33-782cb8aa76f5",
"attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"relationship--3b8bfa40-b074-44a0-af40-a6d461b12c1d",
"relationship--4e10e30d-1634-4080-8c1b-dd59d5db0d01",
"relationship--146b208a-ce40-465a-8f90-69fe92bf0ded",
"relationship--ae1676bb-cd7b-496b-a189-6d86c399be90",
"relationship--5157a2e1-4513-4ff3-9713-fc0347c4fd09",
"relationship--ef7835be-ae5f-423c-bf69-8af713323607",
"relationship--6bc00c7f-1804-4d1d-8f9d-49ecd13a0cbe",
"relationship--b4eceb1d-b918-459a-94a9-dbf0cd176e43",
"relationship--385326f4-c903-48b8-943e-f88a675fcdf4",
"relationship--17498b2e-9571-440c-909e-354d9f360dde",
"relationship--24579ec1-7ad5-47ec-863d-23caff81f818",
"relationship--25db9670-941b-43af-a1e3-5353798df46a",
"relationship--29c88a29-0628-4d5f-a897-6b7509fbb0be",
"relationship--2e1c1442-c80d-4db4-85b1-8b5257b0aece",
"relationship--e3a57dee-5156-434f-ab6f-6c2c4ea615d7",
"relationship--f6f64112-cc29-442a-9629-99b6055d2b00",
"relationship--eec15416-38c4-41e5-a677-1d4750f355b1",
"relationship--db9fafc9-f375-4ba0-b312-5840540b40d3",
"relationship--00702047-c898-4adf-ab0f-30c4d04b1ec2",
"domain-name--873a7760-75e5-4091-8162-384b2ee7f8c9",
"domain-name--b6f4ce85-04c1-4766-8b32-920df5510f37",
"file:hashes.SHA-1--6a49a819-a2ed-476c-8c4d-298683bf4aa1",
"domain-name--29c753b0-3feb-4c7e-9a92-8f2c8c9fb24e",
"domain-name--88b3d244-3c66-46a5-bae9-8ede217c69dc",
"file:hashes.MD5--ecbd40d9-ee16-4c1b-a816-bfd172356f24",
"domain-name--b4af47a4-307a-4660-8a7f-5fec7db5ce8f",
"domain-name--77c38474-b68f-4fe8-b583-22621d3809c0",
"domain-name--61083450-53f9-4839-8bb0-9e9e94562d5d",
"domain-name--9e54c80d-6418-4957-a529-996e711e3e5b",
"domain-name--907c5a78-86bc-48f8-b2b4-388ae2f5f068",
"domain-name--44aa8286-6d7d-4433-820f-41049ad6237f",
"domain-name--18b76748-246e-4829-ae42-1d5ba38f6d69",
"domain-name--492a43b7-80f2-436e-bde4-4641fc572c27",
"domain-name--c2e2bc46-1714-4a1b-8c84-69cea9eb1de0",
"domain-name--e591389f-ae51-4f25-a6c2-cc90916f7697",
"domain-name--f963ad67-318d-4bf4-88c6-e5ec6ceeb375",
"domain-name--4bd36506-1306-4963-b6e8-553d41246a6a",
"domain-name--3d248234-ba1b-4562-8c29-287cd044b600",
"domain-name--2ef63a72-ad0e-4818-a98f-201e2ee49934",
"indicator--92bf41a8-9b78-4cdc-8c0a-de27bd80e460",
"relationship--39ccfbd9-7801-4cc0-9032-649d2b43d0b5",
"indicator--e334b704-a7ba-4724-abac-2b2fabe46e3d",
"relationship--4627939b-8717-428f-bc72-de914957a9d1",
"indicator--c683af5a-14da-4554-ae80-c541e1f8a0de",
"relationship--96b0df48-2bc5-4638-8259-930948f13593",
"indicator--fa01565d-40fa-402c-97fc-3de873664dad",
"relationship--0fdd0ef7-6d0b-4643-9013-e8a252ff4622",
"indicator--69c89b39-2813-40e5-8406-af3807744a3c",
"relationship--bf53efcd-bea2-4b86-8191-4a336ee561d2",
"indicator--b97a5d3b-2d06-413e-8273-b0bd69174a24",
"relationship--8b45807f-cc98-435b-893e-86c4509167c5",
"indicator--ef1c7ecc-d636-4e2a-839f-c3e5137d5cc3",
"relationship--e7d6bfa4-e1ff-4bcd-a7bd-92e64a0a1166",
"indicator--549cb055-f6f4-4480-aa8d-e9c435e8fa58",
"relationship--c6b8f8a9-7b9e-4a15-a580-37c25eb5ae24",
"indicator--90d542f9-511c-437d-8373-d8f1415029fd",
"relationship--e95e833d-bfea-4fbe-a4ca-2af4da5db4d0",
"indicator--b606e853-d967-4985-a601-e01782d90127",
"relationship--13edaa20-3a5b-4a07-9e53-b0713d9c5757",
"indicator--8b5e18cc-0497-4595-a13b-2fff334e3511",
"relationship--5d8c3137-c71b-43e5-8062-d30b78806c6f",
"indicator--1c36448b-f2d0-4232-9117-be3adb45c755",
"relationship--c260d4e2-69ec-40c7-8869-d0452b13ac44",
"indicator--1911bb55-2cf5-41fc-86dc-227270861959",
"relationship--a59caa10-5127-4967-9cdd-eea587892a47",
"indicator--67f2bc27-4140-4725-a44d-ffbed0cd8046",
"relationship--c6a62d26-d8b7-4331-8180-1bef83dfd867",
"indicator--74dcaa0e-3ac8-43ed-86e6-ed61fd7a87fd",
"relationship--dc17c1da-db4c-44ad-8f7c-656d24ae2ce5",
"indicator--f4c3126a-008f-4a3f-ab60-845f9cc2b02d",
"relationship--9e67b24c-c422-42aa-95f9-5f2dd5230c27",
"indicator--1c5c8931-26b1-404a-895c-c230ff21a647",
"relationship--470668bf-98d3-49bf-90d6-02d29c60288f",
"indicator--4585efd3-2efa-46e2-bda4-f44884385a54",
"relationship--f3ea0ae5-ce8d-4f9f-abaf-6ac7b323e3a3"
],
"labels": [
"threat-report",
"threat-intelligence"
],
"created_by_ref": "identity--7f69d815-4b7a-447f-9a08-4bcdb4993a9c",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.947Z",
"modified": "2025-12-29T14:14:19.947Z",
"confidence": 95,
"type": "identity",
"id": "identity--161fc746-cd49-4615-ab48-81a93a1b16b4",
"name": "GitHub",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "GitHub is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.947Z",
"modified": "2025-12-29T14:14:19.947Z",
"confidence": 85,
"type": "vulnerability",
"id": "vulnerability--9fbd3570-7d2f-42cc-8d4a-9d186d7f4749",
"name": "CVE-2025",
"description": "A high-severity security flaw in MongoDB",
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025"
},
{
"source_name": "nvd",
"external_id": "CVE-2025",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 95,
"type": "identity",
"id": "identity--8a7ca088-fae7-4645-8f55-5f28dd9b1396",
"name": "Google",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Google is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 95,
"type": "identity",
"id": "identity--e579f0b6-29fc-4f87-be26-0870951a61da",
"name": "Android",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "Android is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 95,
"type": "identity",
"id": "identity--6a693eb5-52d0-4a9c-9407-96e3ba6cdfad",
"name": "China",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "China is a country.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 95,
"type": "tool",
"id": "tool--4cc7aac6-53bb-4fd2-94f9-f2d3d05ad748",
"name": "LastPass",
"tool_types": [
"unknown"
],
"labels": [
"tool"
],
"description": "A password manager",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 95,
"type": "identity",
"id": "identity--a8a416d7-3adc-4b50-8ceb-058398accecd",
"name": "TRM Labs",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 90,
"type": "vulnerability",
"id": "vulnerability--0eeed38c-ad53-4d03-91b9-68adce80181b",
"name": "CVE-2025-14847",
"description": "Mismatched length fields in Zlib compressed protocol headers may allow a read of uninitialized heap memory by an unauthenticated client. This issue affects all MongoDB Server v7.0 prior to 7.0.28 versions, MongoDB Server v8.0 versions prior to 8.0.17, MongoDB Server v8.2 versions prior to 8.2.3, MongoDB Server v6.0 versions prior to 6.0.27, MongoDB Server v5.0 versions prior to 5.0.32, MongoDB Server v4.4 versions prior to 4.4.30, MongoDB Server v4.2 versions greater than or equal to 4.2.0, Mong. CVSS Score: 7.5 (HIGH). EPSS: 0.0% exploitation probability",
"x_cvss_score": 7.5,
"x_cvss_severity": "HIGH",
"x_kev_status": false,
"x_epss_score": 0.00041,
"external_references": [
{
"source_name": "cve",
"external_id": "CVE-2025-14847",
"url": "https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-14847"
},
{
"source_name": "nvd",
"external_id": "CVE-2025-14847",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2025-14847"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 95,
"type": "identity",
"id": "identity--9bafa8cc-056c-4e34-bb2d-61e718a0438b",
"name": "Cybersecurity",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "Cybersecurity is a company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.948Z",
"modified": "2025-12-29T14:14:19.948Z",
"confidence": 95,
"type": "malware",
"id": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"name": "Trojan",
"is_family": true,
"malware_types": [
"trojan"
],
"labels": [
"malicious-activity"
],
"description": "A type of malware that allows unauthorized access to a computer system",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 95,
"type": "identity",
"id": "identity--3cf91ae9-0a36-4c4f-aad7-9717e2e1a2cd",
"name": "Condé Nast",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A global media company",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--0939e377-efcf-44d2-ba69-a9794c7184bc",
"name": "MongoBleed",
"description": "An event where data is accessed without authorization.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 85,
"type": "vulnerability",
"id": "vulnerability--8a04b2e2-62df-46c1-8ecc-373a1f0e90ce",
"name": "zlib ASAP",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 77,
"type": "vulnerability",
"id": "vulnerability--ae5f3705-fe19-4e4b-8a9f-84b24b282fe1",
"name": "Logitech Actions",
"description": "A flaw in zlib compression leading to information leaks.",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 95,
"type": "vulnerability",
"id": "vulnerability--42344d80-ab4f-401f-8745-d935e1d5ab90",
"name": "Dubbed MongoBleed",
"description": "A popular operating system",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 82,
"type": "vulnerability",
"id": "vulnerability--b92231d2-d9b1-4177-ab65-401adc9a2c6d",
"name": "SecurityWeek",
"description": "A vulnerability in MongoDB",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"vulnerability"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 95,
"type": "identity",
"id": "identity--62522ca0-5df7-4a7f-b817-a969c39fad76",
"name": "Non-Human Identities",
"identity_class": "unknown",
"labels": [
"identity"
],
"description": "A cybersecurity news website",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 95,
"type": "identity",
"id": "identity--a104157d-2858-45b7-af33-782cb8aa76f5",
"name": "University of Texas",
"identity_class": "organization",
"labels": [
"identity"
],
"description": "A person",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:19.949Z",
"modified": "2025-12-29T14:14:19.949Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"name": "Exploit Public-Facing Application",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1190",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1190/",
"external_id": "T1190"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"name": "Exploitation for Client Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1203",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1203/",
"external_id": "T1203"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"name": "Create or Modify System Process",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1543",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1543/",
"external_id": "T1543"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"name": "Boot or Logon Autostart Execution",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/",
"external_id": "T1547"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"name": "Command and Scripting Interpreter",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
}
],
"x_mitre_id": "T1059",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1059/",
"external_id": "T1059"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"name": "Spearphishing Attachment",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/001/",
"external_id": "T1566.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"name": "Spearphishing Link",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/002/",
"external_id": "T1566.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"name": "Spearphishing via Service",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "initial-access"
}
],
"x_mitre_id": "T1566.003",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1566/003/",
"external_id": "T1566.003"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"name": "Modify Registry",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
}
],
"x_mitre_id": "T1112",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1112/",
"external_id": "T1112"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"name": "Registry Run Keys / Startup Folder",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1547.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1547/001/",
"external_id": "T1547.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 90,
"type": "attack-pattern",
"id": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"name": "Remote Services",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "lateral-movement"
}
],
"x_mitre_id": "T1021",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1021/",
"external_id": "T1021"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 73,
"type": "attack-pattern",
"id": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"name": "Vulnerabilities",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "resource-development"
}
],
"x_mitre_id": "T1588.006",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1588/006/",
"external_id": "T1588.006"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 71,
"type": "attack-pattern",
"id": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"name": "Access Token Manipulation",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1134",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1134/",
"external_id": "T1134"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"name": "Scheduled Task",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "execution"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1053.005",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1053/005/",
"external_id": "T1053.005"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"name": "Socket Filters",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "command-and-control"
}
],
"x_mitre_id": "T1205.002",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1205/002/",
"external_id": "T1205.002"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"name": "Boot or Logon Initialization Scripts",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "persistence"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"x_mitre_id": "T1037",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1037/",
"external_id": "T1037"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"name": "Archive via Utility",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1560.001",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1560/001/",
"external_id": "T1560.001"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"name": "Screen Capture",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1113",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1113/",
"external_id": "T1113"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"spec_version": "2.1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"confidence": 70,
"type": "attack-pattern",
"id": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"name": "Adversary-in-the-Middle",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "credential-access"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "collection"
}
],
"x_mitre_id": "T1557",
"external_references": [
{
"source_name": "MITRE ATT&CK",
"url": "https://attack.mitre.org/techniques/T1557/",
"external_id": "T1557"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487"
],
"labels": [
"mitre-attack"
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3b8bfa40-b074-44a0-af40-a6d461b12c1d",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--280ebd89-59bc-4ae2-a9db-1c01a56e50dc",
"confidence": 55,
"description": "Co-occurrence: Trojan and Exploit Public-Facing Application (T1190) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4e10e30d-1634-4080-8c1b-dd59d5db0d01",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--e5974f70-5745-450a-908a-6483ad9c4678",
"confidence": 55,
"description": "Co-occurrence: Trojan and Exploitation for Client Execution (T1203) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--146b208a-ce40-465a-8f90-69fe92bf0ded",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--ce39e6f2-b20f-421e-83e1-242a773e1927",
"confidence": 55,
"description": "Co-occurrence: Trojan and Create or Modify System Process (T1543) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ae1676bb-cd7b-496b-a189-6d86c399be90",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--d5229cf6-f11b-41bc-8aca-0df713047400",
"confidence": 55,
"description": "Co-occurrence: Trojan and Boot or Logon Autostart Execution (T1547) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5157a2e1-4513-4ff3-9713-fc0347c4fd09",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--771ed4e5-6dde-43a8-9c72-d006b0c83e3d",
"confidence": 55,
"description": "Co-occurrence: Trojan and Command and Scripting Interpreter (T1059) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ef7835be-ae5f-423c-bf69-8af713323607",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--2da268b5-7100-4dbc-b23b-d5deafdf268c",
"confidence": 55,
"description": "Co-occurrence: Trojan and Spearphishing Attachment (T1566.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--6bc00c7f-1804-4d1d-8f9d-49ecd13a0cbe",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--baad7d00-8591-4c49-8f48-fabb6a35df65",
"confidence": 55,
"description": "Co-occurrence: Trojan and Spearphishing Link (T1566.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b4eceb1d-b918-459a-94a9-dbf0cd176e43",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--c627c29c-1385-4d76-9046-9c2db86dab11",
"confidence": 55,
"description": "Co-occurrence: Trojan and Spearphishing via Service (T1566.003) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--385326f4-c903-48b8-943e-f88a675fcdf4",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--af705332-242d-4c31-9955-6dca77d560de",
"confidence": 55,
"description": "Co-occurrence: Trojan and Modify Registry (T1112) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--17498b2e-9571-440c-909e-354d9f360dde",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--75f8063e-1388-4007-8255-4523fceba24e",
"confidence": 55,
"description": "Co-occurrence: Trojan and Registry Run Keys / Startup Folder (T1547.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--24579ec1-7ad5-47ec-863d-23caff81f818",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--5aa11eb6-804f-4920-a45f-1fae275ef314",
"confidence": 55,
"description": "Co-occurrence: Trojan and Remote Services (T1021) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--25db9670-941b-43af-a1e3-5353798df46a",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--0b9d5f9a-d372-4a5d-8f9f-e62f6d5e8719",
"confidence": 55,
"description": "Co-occurrence: Trojan and Vulnerabilities (T1588.006) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--29c88a29-0628-4d5f-a897-6b7509fbb0be",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--2d26e3d0-4bbf-44c3-aa9e-5aeab4937638",
"confidence": 55,
"description": "Co-occurrence: Trojan and Access Token Manipulation (T1134) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--2e1c1442-c80d-4db4-85b1-8b5257b0aece",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--27b36b6d-ae90-4767-b07a-563ecef589ea",
"confidence": 55,
"description": "Co-occurrence: Trojan and Scheduled Task (T1053.005) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e3a57dee-5156-434f-ab6f-6c2c4ea615d7",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--ed3369e1-8515-458a-99e3-cb9283fb73d1",
"confidence": 55,
"description": "Co-occurrence: Trojan and Socket Filters (T1205.002) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--f6f64112-cc29-442a-9629-99b6055d2b00",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--5cf0f3fb-3459-4a3d-ad3c-4700efcfecd8",
"confidence": 55,
"description": "Co-occurrence: Trojan and Boot or Logon Initialization Scripts (T1037) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--eec15416-38c4-41e5-a677-1d4750f355b1",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--d2a77ce3-d278-4f77-97f0-227b744a33d3",
"confidence": 55,
"description": "Co-occurrence: Trojan and Archive via Utility (T1560.001) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--db9fafc9-f375-4ba0-b312-5840540b40d3",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--a6ff86fe-f269-42e5-9428-ab17d04e30e2",
"confidence": 55,
"description": "Co-occurrence: Trojan and Screen Capture (T1113) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--00702047-c898-4adf-ab0f-30c4d04b1ec2",
"created": "2025-12-29T14:14:20.997Z",
"modified": "2025-12-29T14:14:20.997Z",
"relationship_type": "uses",
"source_ref": "malware--6975652f-c247-47d4-8b69-5eba0a4b6104",
"target_ref": "attack-pattern--e8d516a9-a107-4c4b-806f-bc9c612eef18",
"confidence": 55,
"description": "Co-occurrence: Trojan and Adversary-in-the-Middle (T1557) in same intelligence",
"x_validation_method": "mitre-cooccurrence"
},
{
"type": "domain-name",
"value": "filmver.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"Facebook Trojan"
],
"id": "domain-name--873a7760-75e5-4091-8162-384b2ee7f8c9"
},
{
"type": "domain-name",
"value": "pornokan.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"Facebook Trojan"
],
"id": "domain-name--b6f4ce85-04c1-4766-8b32-920df5510f37"
},
{
"type": "file:hashes.SHA-1",
"value": "b836facdde6c866db5ad3f582c86a7f99db09784",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"Facebook Trojan"
],
"id": "file:hashes.SHA-1--6a49a819-a2ed-476c-8c4d-298683bf4aa1"
},
{
"type": "domain-name",
"value": "www.pornokan.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"Facebook Trojan"
],
"id": "domain-name--29c753b0-3feb-4c7e-9a92-8f2c8c9fb24e"
},
{
"type": "domain-name",
"value": "www.filmver.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"Facebook Trojan"
],
"id": "domain-name--88b3d244-3c66-46a5-bae9-8ede217c69dc"
},
{
"type": "file:hashes.MD5",
"value": "cdcc132fad2e819e7ab94e5e564e8968",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"Facebook Trojan"
],
"id": "file:hashes.MD5--ecbd40d9-ee16-4c1b-a816-bfd172356f24"
},
{
"type": "domain-name",
"value": "ftp.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--b4af47a4-307a-4660-8a7f-5fec7db5ce8f"
},
{
"type": "domain-name",
"value": "web.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--77c38474-b68f-4fe8-b583-22621d3809c0"
},
{
"type": "domain-name",
"value": "www.hkchurch.org",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--61083450-53f9-4839-8bb0-9e9e94562d5d"
},
{
"type": "domain-name",
"value": "istore.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--9e54c80d-6418-4957-a529-996e711e3e5b"
},
{
"type": "domain-name",
"value": "capser.zues.info",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--907c5a78-86bc-48f8-b2b4-388ae2f5f068"
},
{
"type": "domain-name",
"value": "auto.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--44aa8286-6d7d-4433-820f-41049ad6237f"
},
{
"type": "domain-name",
"value": "scqf.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--18b76748-246e-4829-ae42-1d5ba38f6d69"
},
{
"type": "domain-name",
"value": "fas2t.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--492a43b7-80f2-436e-bde4-4641fc572c27"
},
{
"type": "domain-name",
"value": "casper.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--c2e2bc46-1714-4a1b-8c84-69cea9eb1de0"
},
{
"type": "domain-name",
"value": "fast2.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--e591389f-ae51-4f25-a6c2-cc90916f7697"
},
{
"type": "domain-name",
"value": "fast.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--f963ad67-318d-4bf4-88c6-e5ec6ceeb375"
},
{
"type": "domain-name",
"value": "ser.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--4bd36506-1306-4963-b6e8-553d41246a6a"
},
{
"type": "domain-name",
"value": "www1.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--3d248234-ba1b-4562-8c29-287cd044b600"
},
{
"type": "domain-name",
"value": "rfa.bacguarp.com",
"source": "OTX",
"malware_families": [
"Trojan"
],
"pulse_names": [
"PlugX Uses Legitimate Samsung Application for DLL Side-Loading"
],
"id": "domain-name--2ef63a72-ad0e-4818-a98f-201e2ee49934"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--92bf41a8-9b78-4cdc-8c0a-de27bd80e460",
"created": "2025-12-29T14:14:03.946Z",
"modified": "2025-12-29T14:14:03.947Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'filmver.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:03.947Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--39ccfbd9-7801-4cc0-9032-649d2b43d0b5",
"created": "2025-12-29T14:14:03.947Z",
"modified": "2025-12-29T14:14:03.947Z",
"relationship_type": "based-on",
"source_ref": "indicator--92bf41a8-9b78-4cdc-8c0a-de27bd80e460",
"target_ref": "domain-name--873a7760-75e5-4091-8162-384b2ee7f8c9"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--e334b704-a7ba-4724-abac-2b2fabe46e3d",
"created": "2025-12-29T14:14:03.956Z",
"modified": "2025-12-29T14:14:03.956Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'pornokan.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:03.956Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4627939b-8717-428f-bc72-de914957a9d1",
"created": "2025-12-29T14:14:03.956Z",
"modified": "2025-12-29T14:14:03.956Z",
"relationship_type": "based-on",
"source_ref": "indicator--e334b704-a7ba-4724-abac-2b2fabe46e3d",
"target_ref": "domain-name--b6f4ce85-04c1-4766-8b32-920df5510f37"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--c683af5a-14da-4554-ae80-c541e1f8a0de",
"created": "2025-12-29T14:14:03.964Z",
"modified": "2025-12-29T14:14:03.964Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'www.pornokan.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:03.964Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--96b0df48-2bc5-4638-8259-930948f13593",
"created": "2025-12-29T14:14:03.964Z",
"modified": "2025-12-29T14:14:03.964Z",
"relationship_type": "based-on",
"source_ref": "indicator--c683af5a-14da-4554-ae80-c541e1f8a0de",
"target_ref": "domain-name--29c753b0-3feb-4c7e-9a92-8f2c8c9fb24e"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--fa01565d-40fa-402c-97fc-3de873664dad",
"created": "2025-12-29T14:14:03.972Z",
"modified": "2025-12-29T14:14:03.972Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'www.filmver.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:03.972Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--0fdd0ef7-6d0b-4643-9013-e8a252ff4622",
"created": "2025-12-29T14:14:03.972Z",
"modified": "2025-12-29T14:14:03.972Z",
"relationship_type": "based-on",
"source_ref": "indicator--fa01565d-40fa-402c-97fc-3de873664dad",
"target_ref": "domain-name--88b3d244-3c66-46a5-bae9-8ede217c69dc"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--69c89b39-2813-40e5-8406-af3807744a3c",
"created": "2025-12-29T14:14:03.981Z",
"modified": "2025-12-29T14:14:03.981Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'ftp.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:03.981Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--bf53efcd-bea2-4b86-8191-4a336ee561d2",
"created": "2025-12-29T14:14:03.981Z",
"modified": "2025-12-29T14:14:03.981Z",
"relationship_type": "based-on",
"source_ref": "indicator--69c89b39-2813-40e5-8406-af3807744a3c",
"target_ref": "domain-name--b4af47a4-307a-4660-8a7f-5fec7db5ce8f"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--b97a5d3b-2d06-413e-8273-b0bd69174a24",
"created": "2025-12-29T14:14:03.990Z",
"modified": "2025-12-29T14:14:03.990Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'web.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:03.990Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--8b45807f-cc98-435b-893e-86c4509167c5",
"created": "2025-12-29T14:14:03.990Z",
"modified": "2025-12-29T14:14:03.990Z",
"relationship_type": "based-on",
"source_ref": "indicator--b97a5d3b-2d06-413e-8273-b0bd69174a24",
"target_ref": "domain-name--77c38474-b68f-4fe8-b583-22621d3809c0"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--ef1c7ecc-d636-4e2a-839f-c3e5137d5cc3",
"created": "2025-12-29T14:14:03.999Z",
"modified": "2025-12-29T14:14:03.999Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'www.hkchurch.org']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:03.999Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e7d6bfa4-e1ff-4bcd-a7bd-92e64a0a1166",
"created": "2025-12-29T14:14:03.999Z",
"modified": "2025-12-29T14:14:03.999Z",
"relationship_type": "based-on",
"source_ref": "indicator--ef1c7ecc-d636-4e2a-839f-c3e5137d5cc3",
"target_ref": "domain-name--61083450-53f9-4839-8bb0-9e9e94562d5d"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--549cb055-f6f4-4480-aa8d-e9c435e8fa58",
"created": "2025-12-29T14:14:04.009Z",
"modified": "2025-12-29T14:14:04.009Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'istore.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.009Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c6b8f8a9-7b9e-4a15-a580-37c25eb5ae24",
"created": "2025-12-29T14:14:04.009Z",
"modified": "2025-12-29T14:14:04.009Z",
"relationship_type": "based-on",
"source_ref": "indicator--549cb055-f6f4-4480-aa8d-e9c435e8fa58",
"target_ref": "domain-name--9e54c80d-6418-4957-a529-996e711e3e5b"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--90d542f9-511c-437d-8373-d8f1415029fd",
"created": "2025-12-29T14:14:04.019Z",
"modified": "2025-12-29T14:14:04.019Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'capser.zues.info']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.019Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--e95e833d-bfea-4fbe-a4ca-2af4da5db4d0",
"created": "2025-12-29T14:14:04.019Z",
"modified": "2025-12-29T14:14:04.019Z",
"relationship_type": "based-on",
"source_ref": "indicator--90d542f9-511c-437d-8373-d8f1415029fd",
"target_ref": "domain-name--907c5a78-86bc-48f8-b2b4-388ae2f5f068"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--b606e853-d967-4985-a601-e01782d90127",
"created": "2025-12-29T14:14:04.028Z",
"modified": "2025-12-29T14:14:04.028Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'auto.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.028Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--13edaa20-3a5b-4a07-9e53-b0713d9c5757",
"created": "2025-12-29T14:14:04.028Z",
"modified": "2025-12-29T14:14:04.028Z",
"relationship_type": "based-on",
"source_ref": "indicator--b606e853-d967-4985-a601-e01782d90127",
"target_ref": "domain-name--44aa8286-6d7d-4433-820f-41049ad6237f"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--8b5e18cc-0497-4595-a13b-2fff334e3511",
"created": "2025-12-29T14:14:04.038Z",
"modified": "2025-12-29T14:14:04.038Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'scqf.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.038Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5d8c3137-c71b-43e5-8062-d30b78806c6f",
"created": "2025-12-29T14:14:04.038Z",
"modified": "2025-12-29T14:14:04.038Z",
"relationship_type": "based-on",
"source_ref": "indicator--8b5e18cc-0497-4595-a13b-2fff334e3511",
"target_ref": "domain-name--18b76748-246e-4829-ae42-1d5ba38f6d69"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--1c36448b-f2d0-4232-9117-be3adb45c755",
"created": "2025-12-29T14:14:04.046Z",
"modified": "2025-12-29T14:14:04.047Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'fas2t.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.047Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c260d4e2-69ec-40c7-8869-d0452b13ac44",
"created": "2025-12-29T14:14:04.047Z",
"modified": "2025-12-29T14:14:04.047Z",
"relationship_type": "based-on",
"source_ref": "indicator--1c36448b-f2d0-4232-9117-be3adb45c755",
"target_ref": "domain-name--492a43b7-80f2-436e-bde4-4641fc572c27"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--1911bb55-2cf5-41fc-86dc-227270861959",
"created": "2025-12-29T14:14:04.055Z",
"modified": "2025-12-29T14:14:04.055Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'casper.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.055Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a59caa10-5127-4967-9cdd-eea587892a47",
"created": "2025-12-29T14:14:04.055Z",
"modified": "2025-12-29T14:14:04.055Z",
"relationship_type": "based-on",
"source_ref": "indicator--1911bb55-2cf5-41fc-86dc-227270861959",
"target_ref": "domain-name--c2e2bc46-1714-4a1b-8c84-69cea9eb1de0"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--67f2bc27-4140-4725-a44d-ffbed0cd8046",
"created": "2025-12-29T14:14:04.064Z",
"modified": "2025-12-29T14:14:04.064Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'fast2.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.064Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c6a62d26-d8b7-4331-8180-1bef83dfd867",
"created": "2025-12-29T14:14:04.064Z",
"modified": "2025-12-29T14:14:04.064Z",
"relationship_type": "based-on",
"source_ref": "indicator--67f2bc27-4140-4725-a44d-ffbed0cd8046",
"target_ref": "domain-name--e591389f-ae51-4f25-a6c2-cc90916f7697"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--74dcaa0e-3ac8-43ed-86e6-ed61fd7a87fd",
"created": "2025-12-29T14:14:04.072Z",
"modified": "2025-12-29T14:14:04.072Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'fast.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.072Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--dc17c1da-db4c-44ad-8f7c-656d24ae2ce5",
"created": "2025-12-29T14:14:04.072Z",
"modified": "2025-12-29T14:14:04.072Z",
"relationship_type": "based-on",
"source_ref": "indicator--74dcaa0e-3ac8-43ed-86e6-ed61fd7a87fd",
"target_ref": "domain-name--f963ad67-318d-4bf4-88c6-e5ec6ceeb375"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--f4c3126a-008f-4a3f-ab60-845f9cc2b02d",
"created": "2025-12-29T14:14:04.081Z",
"modified": "2025-12-29T14:14:04.081Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'ser.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.081Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--9e67b24c-c422-42aa-95f9-5f2dd5230c27",
"created": "2025-12-29T14:14:04.081Z",
"modified": "2025-12-29T14:14:04.081Z",
"relationship_type": "based-on",
"source_ref": "indicator--f4c3126a-008f-4a3f-ab60-845f9cc2b02d",
"target_ref": "domain-name--4bd36506-1306-4963-b6e8-553d41246a6a"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--1c5c8931-26b1-404a-895c-c230ff21a647",
"created": "2025-12-29T14:14:04.089Z",
"modified": "2025-12-29T14:14:04.089Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'www1.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.089Z",
"labels": [
"malicious-activity"
],
"confidence": 75
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--470668bf-98d3-49bf-90d6-02d29c60288f",
"created": "2025-12-29T14:14:04.089Z",
"modified": "2025-12-29T14:14:04.089Z",
"relationship_type": "based-on",
"source_ref": "indicator--1c5c8931-26b1-404a-895c-c230ff21a647",
"target_ref": "domain-name--3d248234-ba1b-4562-8c29-287cd044b600"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--4585efd3-2efa-46e2-bda4-f44884385a54",
"created": "2025-12-29T14:14:04.097Z",
"modified": "2025-12-29T14:14:04.097Z",
"name": "Malicious domain-name indicator",
"description": "Malicious domain-name identified in threat intelligence",
"pattern": "[domain-name:value = 'rfa.bacguarp.com']",
"pattern_type": "stix",
"valid_from": "2025-12-29T14:14:04.097Z",
"labels": [
"malicious-activity"
],
"confidence": 70
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--f3ea0ae5-ce8d-4f9f-abaf-6ac7b323e3a3",
"created": "2025-12-29T14:14:04.097Z",
"modified": "2025-12-29T14:14:04.097Z",
"relationship_type": "based-on",
"source_ref": "indicator--4585efd3-2efa-46e2-bda4-f44884385a54",
"target_ref": "domain-name--2ef63a72-ad0e-4818-a98f-201e2ee49934"
}
]
}


 CRITICAL ITEMS
CRITICAL ITEMS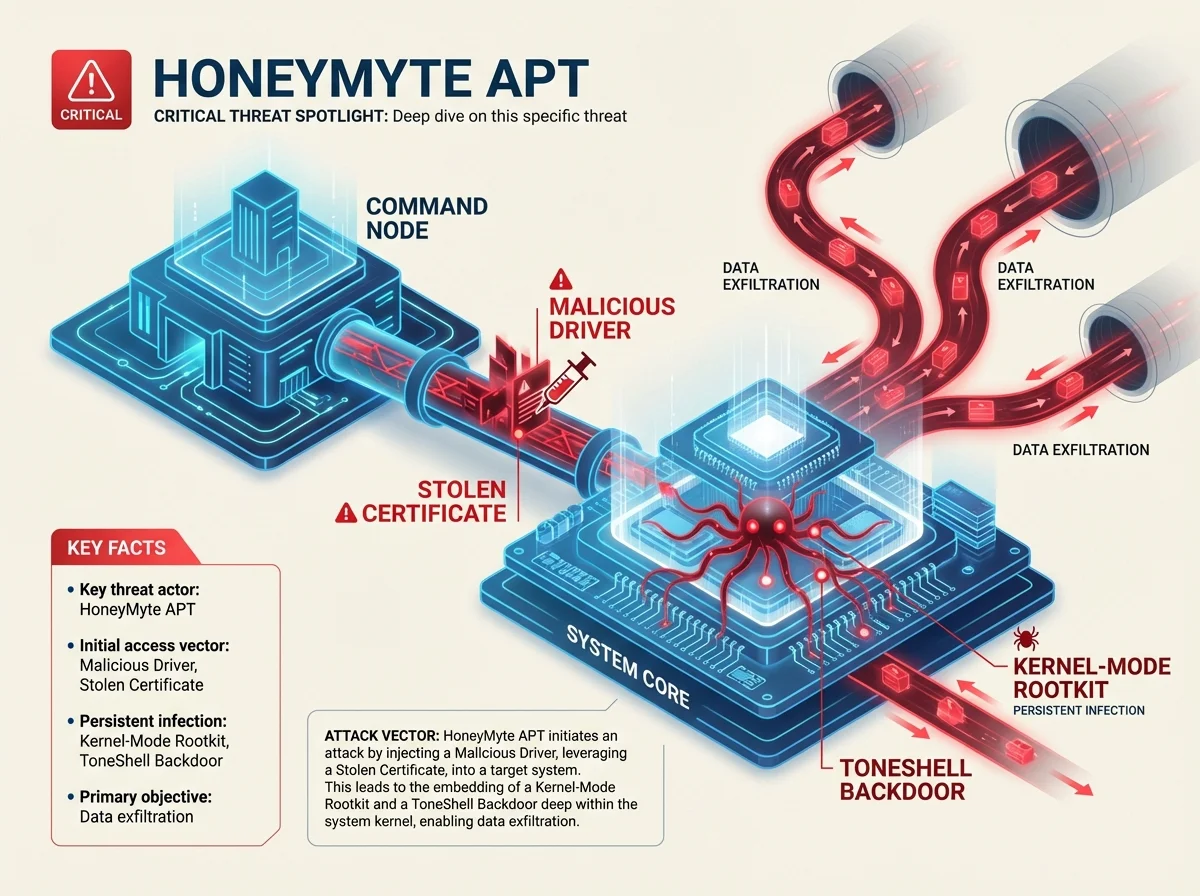
 HIGH SEVERITY ITEMS
HIGH SEVERITY ITEMS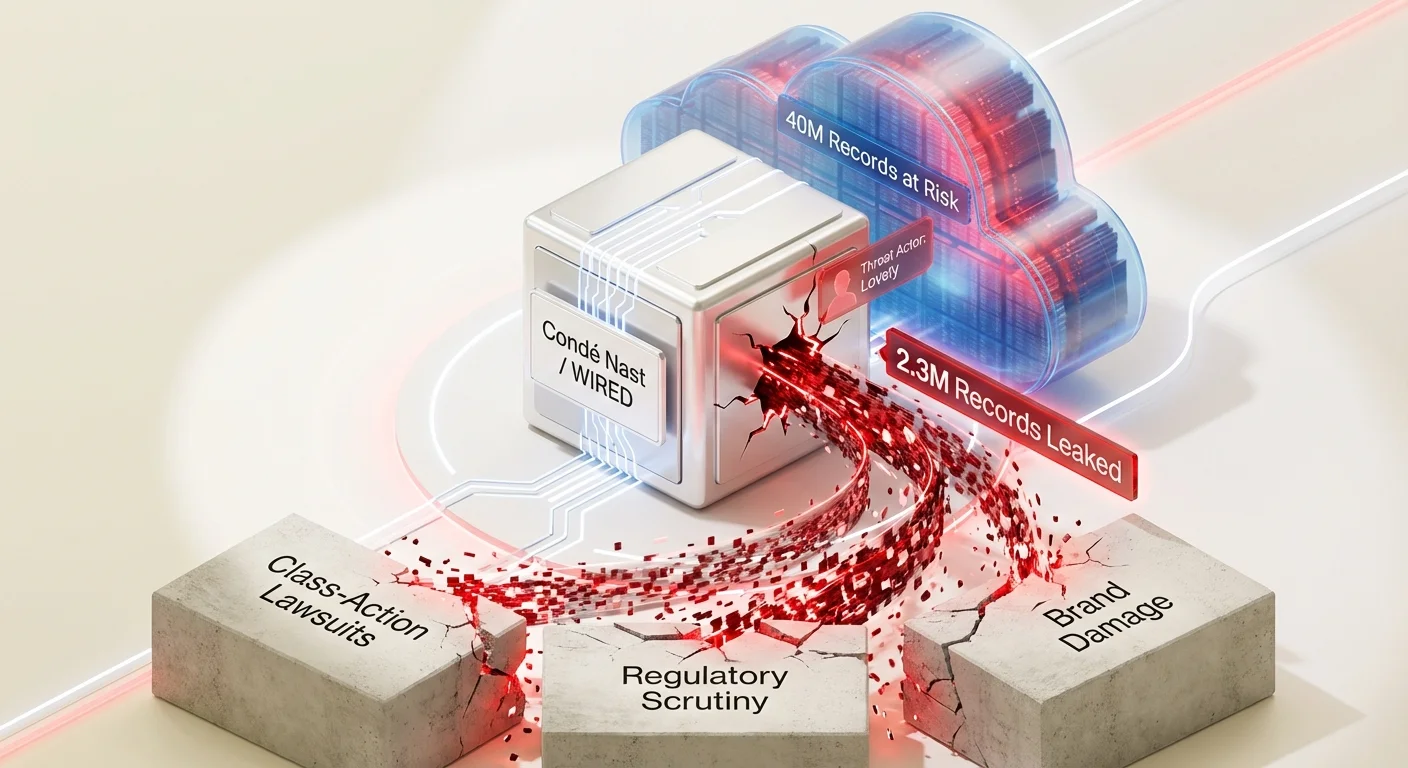
 EXECUTIVE INSIGHTS
EXECUTIVE INSIGHTS VENDOR SPOTLIGHT
VENDOR SPOTLIGHT DETECTION & RESPONSE KIT
DETECTION & RESPONSE KIT